Read the policy page thoroughly yourself before directly starting the hunt 🔍
1️⃣ Zoho
https://bugbounty.zohocorp.com/bb/infoScope
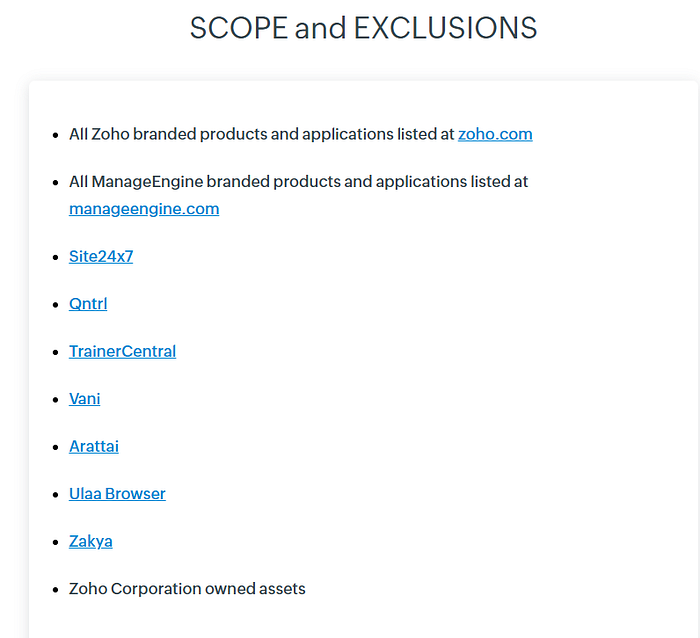
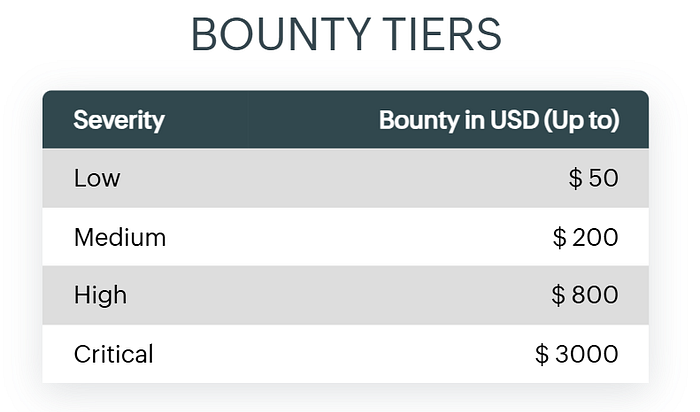
Severity <> Reward
Exact figure might get changed at the time you read this article
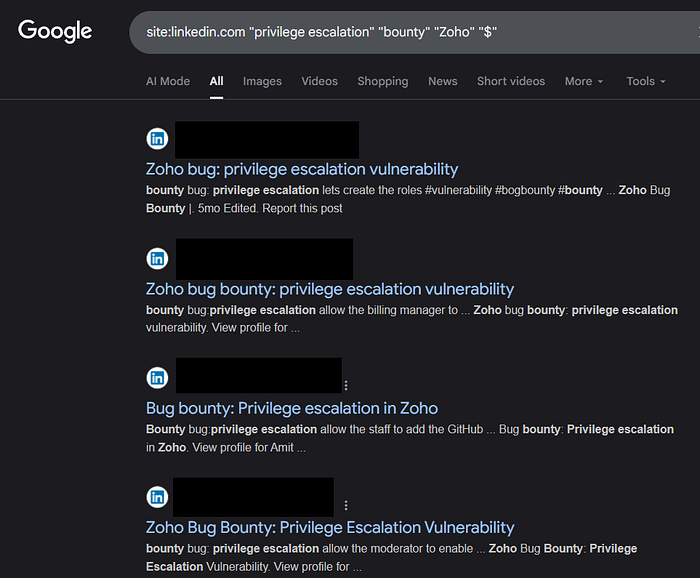
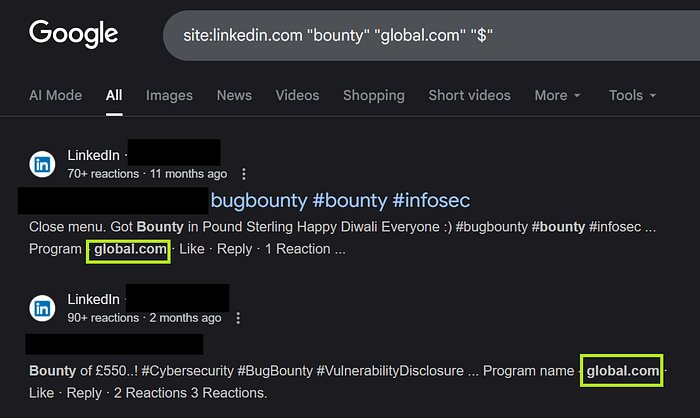
LinkedIn OSINT via Dorking
2️⃣ Global
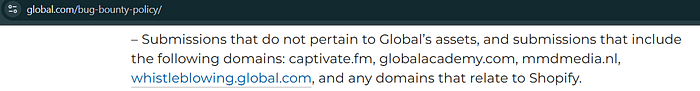
global.com/bug-bounty-policy/In-Scope
At the time of writing this article, the scope is all assets owned by Global except below domains
Out of scope
Reward
Exact number not mentioned in the policy, depends on case by case with CVSS score and impact demonstrated in the POC.
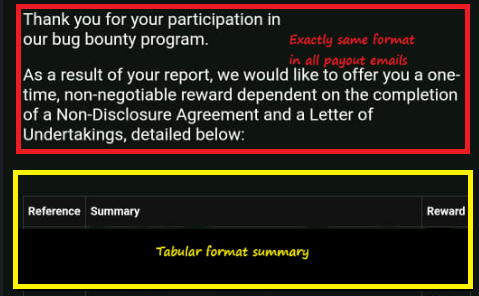
Understanding the Payout Email Format
- You can easily predict (99% of the time) that the screenshot shared in X or LinkedIn belongs to this program. A tabular structured format is followed in the email for valid reports like below
LinkedIn OSINT via Dorking
Finding response time before investing time in it
- To know the response time, use these dorks and DM those researchers in LinkedIn politely :)
Top Bug Class that will never disappoint you
- Broken Access Control 🔓
- Business Logic Flaw/Error
- Sensitive information disclosure 🗝️
- Bypass based (Bypass of the patch)
What majority of the beginners focuses on ?
- Only injection based vulnerabilities (Mainly XSS)
Have fun 🤘 See you in next article!


