Day 1 of my 100-Day Cyber Exploration focuses on Shodan, the search engine for the Internet of Things. We'll learn how to use filters, ASNs, and banners to discover internet-facing devices safely. This series documents my daily hands-on journey into real-world cyber techniques and tools.

Task 1:Introduction
Shodan.io is the search engine for the Internet of Things. It scans the public internet and indexes the services running on each IP address — everything from CCTV cameras and Pi-Holes to weirdly exposed office devices like smart coffee machines. Want to know which devices are publicly reachable and what services they expose? Shodan is the tool.
Finding services on a target
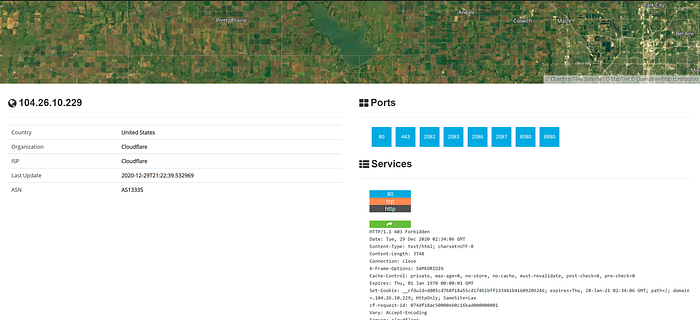
When performing a pentest or security review, a common first step is discovering what services a target runs. If you have a hostname, start by resolving it to an IP address (for example via ping or dig). That IP can then be fed into Shodan to see services, open ports and metadata Shodan has indexed for that host.
Example workflow:
- Resolve the host to an IP (e.g.,
ping tryhackme.com→ IP address). - Paste that IP into Shodan or query via the API.
- Review the results — Shodan will show open ports, service banners, geolocation, and organization information.
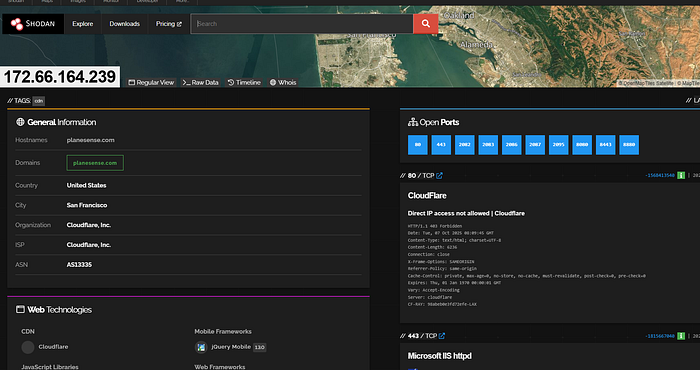
Sometimes the results show a content-delivery/proxy provider (e.g., Cloudflare). That hides the origin server IPs, which is unhelpful if your goal is to enumerate the target's actual infrastructure. To go beyond that, we can use Autonomous System Numbers.
Autonomous System Numbers (ASNs)
An Autonomous System Number (ASN) identifies a block/range of IP addresses owned or operated by an organization or provider. Large organizations often control an ASN for the IP space they own.
If you have an IP and want to find the broader network it belongs to:
- Use an ASN lookup tool (for example:
asnlookup.com) orwhoisto find the ASN for an IP.
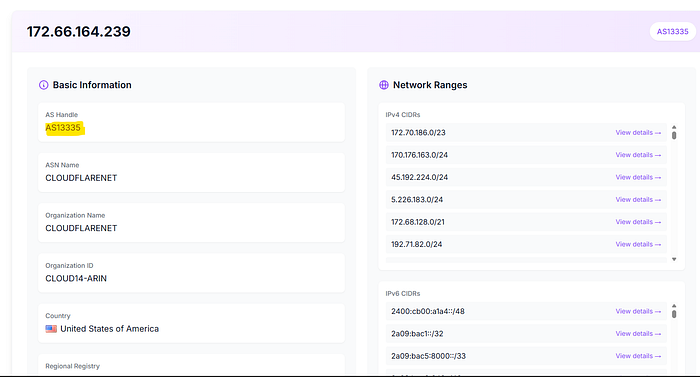
2.The ASN will look like AS14061, AS15169, etc.
3.Searching Shodan for asn:AS14061 lists all hosts Shodan knows about within that ASN.
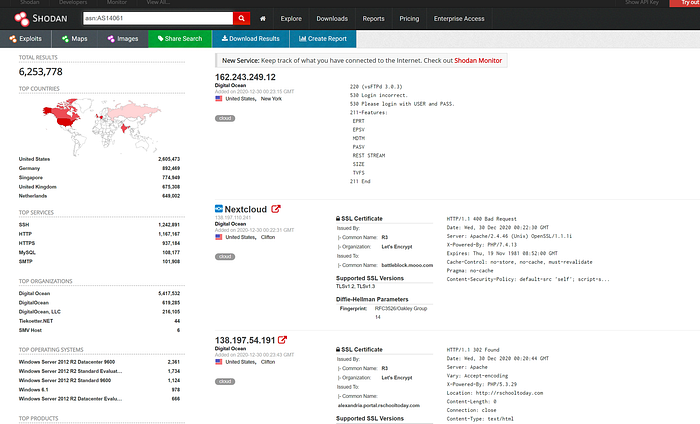
Why this helps: if the target owns an ASN, searching that ASN in Shodan shows you everything Shodan sees in that network — useful for discovering exposed services and devices that belong to the same organization. If the ASN belongs to a cloud provider (DigitalOcean, AWS, Google, etc.), you'll see lots of unrelated hosts that happen to be hosted there.
Banners — what Shodan stores
Shodan indexes service responses called banners. Banners are the raw information returned when Shodan connects to a port — they often include service strings, version info, device names, and configuration details (and sometimes sensitive info like authentication state).
A typical banner (JSON-style) might contain fields like:
{
"data": "Moxa Nport Device",
"Status": "Authentication disabled",
"Name": "NP5232I_4728",
"MAC": "00:90:e8:47:10:2d",
"ip_str": "46.252.132.235",
"port": 4800,
"org": "Starhub Mobile",
"location": { "country_code": "SG" }
}That output corresponds to a single port scan result and includes IP, port, organization and sometimes security-relevant flags (e.g., "Authentication disabled").
Task 2 : Filters
Filters On the Shodan.io homepage, we can click on "explore" to view the most up voted search queries. The most popular one is webcams.
Note: this is a grey area. It is legal to view a publicly accessible webcam, it is illegal to try to break into a password protected one. Use your brain and research the laws of your country!
One of the other most up voted searches is a search for MYSQL databases.
https://www.shodan.io/search?query=product%3AMySQL
If we look at the search, we can see it is another filter.
product:MySQL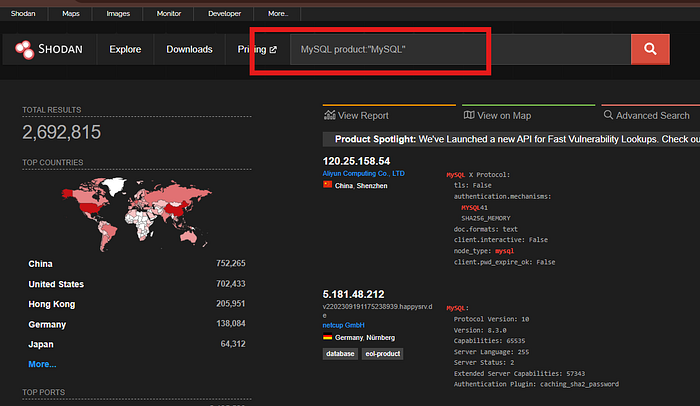
Knowing this, we can actually combine 2 searches into 1.
On TryHackMe's ASN, let's try to find some MYSQL servers.
We use this search query
asn:AS14061 product:MySQLAnd ta-da! We have MYSQL servers on the TryHackMe ASN (which is really the DigitalOcean ASN).
https://www.shodan.io/search?query=asn%3AAS14061+product%3AMySQL
Shodan has many powerful filters. My favourite one is the vuln filter, which let's us search for IP addresses vulnerable to an exploit.
Let's say we want to find IP addresses vulnerable to EternalBlue:
vuln:ms17-010However, this is only available for academic or business users, to prevent bad actors from abusing this!
City Country Geo (coordinates) Hostname net (based on IP / CIDR) os (find operating systems) port before/after (timeframes)
API
Shodan.io has an API! It requires an account, so I won't talk about it here.
If you want to explore the Shodan API, I've written a blog post about finding Pi-Holes with it here:
https://github.com/beesecurity/How-I-Hacked-Your-Pi-Hole/blob/master/README.md
The API lets us programmatically search Shodan and receive a list of IP addresses in return. If we are a company, we can write a script to check over our IP addresses to see if any of them are vulnerable.
PS: You can automatically filter on Shodan by clicking the things in the left hand side bar!
Question 2.1 What command is used to find EternalBlue exploits on Shodan using the vuln filter?
vuln:ms17-010Task 3 — Google & Filtering
In this task, we'll explore how to use Shodan filters to analyze information under Google's ASN (AS15169). We'll learn to filter results by product, location, and operating system — and use this data to answer each question.
Question 3.1 — What is the top operating system for MySQL servers in Google's ASN?
Answer:
5.6.40-84.0-log
💡 Hint:
We used the search query asn:AS15169 product:MySQL on Shodan and checked the "Operating System" field. The most frequently appearing version under Google's ASN was 5.6.40-84.0-log.
(This question is an updated outbounded one.)
Question 3.2 — What is the 2nd most popular country for MySQL servers in Google's ASN?
Answer:
Netherlands
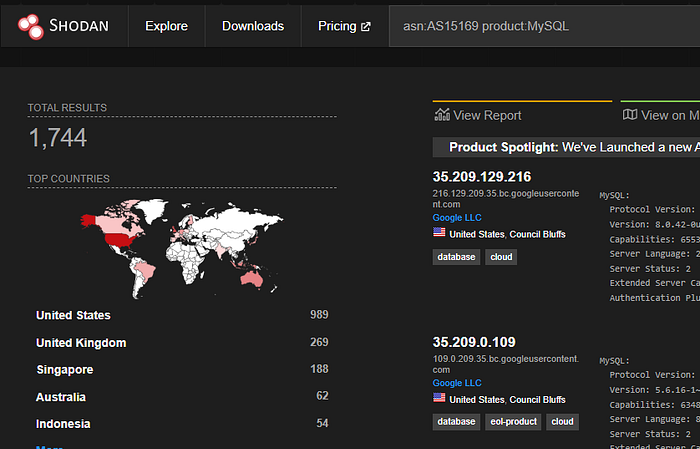
💡 Hint:
Using the same query asn:AS15169 product:MySQL, we checked the country distribution on the left sidebar in Shodan. The United States ranked first, while Netherlands appeared as the second most common country.
(This question is an updated outbounded one.)
Question 3.3 — Under Google's ASN, which is more popular for nginx — Hypertext Transfer Protocol or Hypertext Transfer Protocol with SSL?
✅ Answer:
Hypertext Transfer Protocol
💡 Hint: We compared two Shodan queries:
asn:AS15169 product:nginx port:80→ HTTPasn:AS15169 product:nginx port:443→ HTTPS The results showed a higher count for port 80 (HTTP), making it more popular overall.
Question 3.4 — Under Google's ASN, what is the most popular city?
Answer:
Kansas City
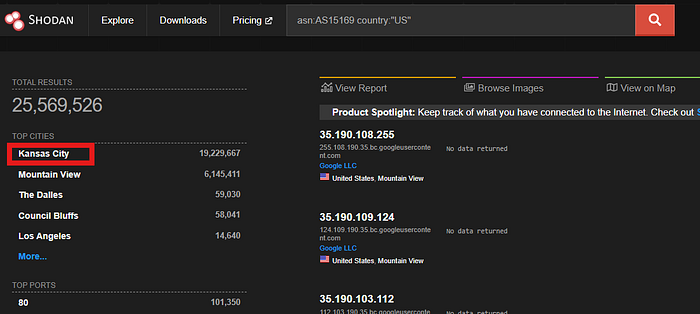
💡 Hint:
After running asn:AS15169 on Shodan, we looked at the City filter on the left-hand side. Among all results, Kansas City appeared as the top city.
(This question is an updated outbounded one.)
Question 3.5 — Under Google's ASN in Los Angeles, what is the top operating system according to Shodan?
Answer:
Debian
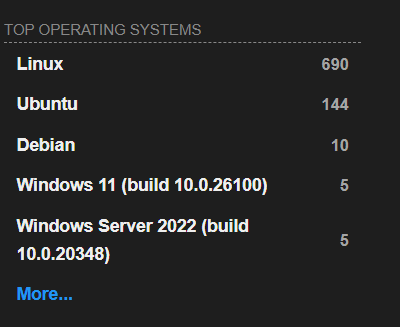
(This question is an updated outbounded one.)
💡 Hint:
We refined our search using asn:AS15169 city:"Los Angeles" and then observed the "Operating System" filter. The most listed OS for Google's Los Angeles-based servers was Debian.
Question 3.6 — Using the top Webcam search from the Explore page, does Google's ASN have any webcams?
Answer:
Nay
💡 Hint:
We used the top explore search term category:webcam combined with asn:AS15169.
Result: No publicly listed webcams were found under Google's ASN.
Task 4 — Shodan Monitor
Shodan Monitor is a Shodan application for tracking devices you expose to the internet. It lets you add IP ranges, receive notifications, launch scans, and get visibility into connected devices. You can use it to monitor your own network (or saved targets for bug-bounty monitoring) and receive email alerts when Shodan detects notable issues.
When you add a network, Shodan Monitor shows a dashboard with items like:
- Top Open Ports
- Top Vulnerabilities
- Notable Ports
- Potential Vulnerabilities
- Notable IPs
Note: Shodan Monitor is a premium feature.
4.1 — What URL takes you to Shodan Monitor?
Answer:
https://monitor.shodan.io/dashboard
Hint (how we got that):
Open Shodan's Monitor documentation or the Monitor product page and follow the "dashboard" link. The Monitor dashboard URL is shown in the app and is https://monitor.shodan.io/dashboard.
Task 5 — Shodan Dorking
Shodan has many useful "dorks" (search patterns) that let you surface interesting or dangerous things on the public internet. Below are some examples and a short explanation of each.
has_screenshot:true encrypted attentionUses optical character recognition (OCR) on screenshots and looks for strings like "encrypted" and "attention" — commonly present on compromised machines showing ransomware notes. This helps find PCs that appear to be infected by ransomware.screenshot.label:icsFinds screenshots that Shodan's OCR or labeling has tagged as industrial control system (ICS) interfaces.vuln:CVE-2014-0160Finds internet-connected machines vulnerable to Heartbleed. (Note: CVE /vuln:searches may be restricted to academic/business subscribers.)http.favicon.hash:-1776962843Favicons can fingerprint products or codebases — this particular hash was used to help find hosts involved in the SolarWinds supply-chain incident.
You can find curated lists of Shodan dorks on places like GitHub and in Shodan's own examples.
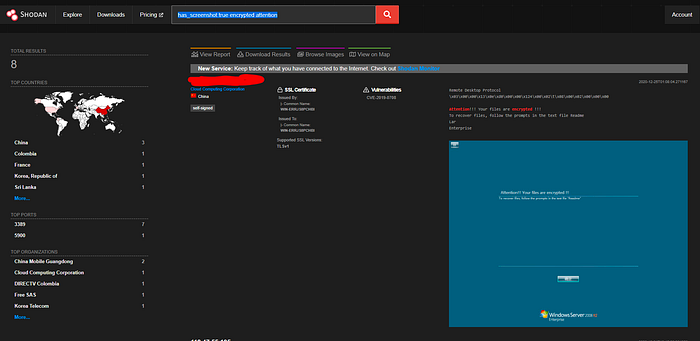
5.1 — What dork lets us find PCs infected by Ransomware?
Answer:
has_screenshot:true encrypted attention💡 Hint (how we got that):
This dork requests hosts with screenshots (has_screenshot:true) and searches those screenshots (via OCR/labels) for words commonly present in ransomware notes such as "encrypted" and "attention". The combination surfaces machines showing ransomware messages.
Task 6 — Shodan Extension
Shodan Extension
Shodan provides a browser extension (Chrome) that surfaces Shodan data about the site you're visiting — useful for quick reconnaissance and spotting low-effort targets when doing bug-bounty triage.
Install / view: https://chrome.google.com/webstore/detail/shodan/jjalcfnidlmpjhdfepjhjbhnhkbgleap
What it shows when you click the extension
- The webserver's IP address.
- Open ports Shodan has indexed for that IP.
- Geolocation / organization information (where the IP is registered).
- Any security issues or notable flags Shodan has for that host (vuln banners, unusual services, etc.).
Why it's useful
- Fast, one-click context: checks the exposed surface without leaving your browser.
- Great for quick bug-bounty triage — you can immediately tell if a host looks interesting (old software, open management ports, uncommon services).
- Saves time when scanning many targets manually — use it to prioritize deeper investigation.
Notes & caveats
- The extension shows Shodan's indexed data — it doesn't actively scan the site when you click. Data may be cached or slightly out-of-date.
- Don't attempt to probe or exploit anything you don't have permission to test — using Shodan data to identify potential vulnerabilities is fine, but exploitation without consent is illegal.
- Some sites (CDNs, reverse proxies) will show the proxy IP rather than the origin server.
PS: The Chrome webstore image is the official icon — yes, it's a bit blurry, but the extension itself works fine.
(That's it — no answer required for this task.)
Task 7 — Exploring the API & Conclusion
Shodan.io has an API! The API requires a Shodan account and an API key. With it you can programmatically search Shodan, retrieve lists of IPs, pull banners, request facets, and automate monitoring or inventory checks across an organisation's address space.
If you want a worked example and a walk-through, read the blog post linked below — it's a hands-on guide showing how the API can be used to find Pi-Holes and automate checks:
https://github.com/beesecurity/How-I-Hacked-Your-Pi-Hole/blob/master/README.md
Why use the API?
- Automate discovery: run periodic searches (e.g.,
asn:YOUR_ASN product:MySQL) and ingest results into an asset inventory. - Alerting & remediation: integrate with ticketing/monitoring so teams get notified when new vulnerable hosts appear.
- Aggregation: use facets to get fast statistics (top ports, top ASNs, etc.) without fetching every result.
- Scalability: script bulk lookups, map IP → ASN, and produce summary reports.
Minimal example (Python) — what it looks like
# requires: pip install shodan
import shodan
API_KEY = "YOUR_API_KEY"
api = shodan.Shodan(API_KEY)
# simple search
results = api.search("asn:AS15169 product:MySQL", limit=100)
for match in results['matches']:
print(match.get('ip_str'), match.get('port'), match.get('org'))Note: the exact fields returned may vary by match; use facets for aggregated counts.
Final notes / best practices
- Account & quota: the API requires an API key and different features (facets, vuln filters, exports) may be limited by plan.
- False positives: Shodan's clues are leads — always verify with authorized scanning.
- Legal & ethical: only scan or probe systems you own or have explicit permission to test. Use the API for asset management, monitoring and authorized security work.