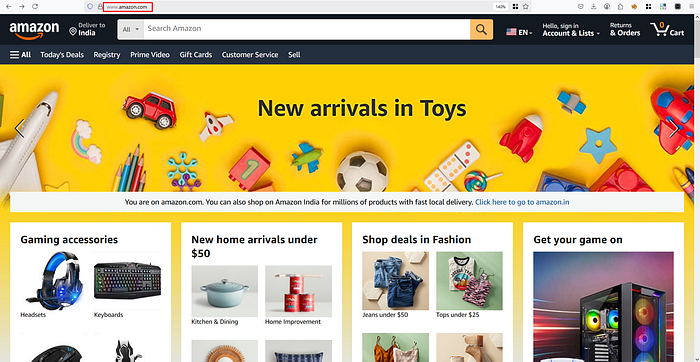
While browsing the internet, you've probably noticed the web address or URL at the top of your browser — something like "www.amazon.com". This is known as a domain name, and it's used to uniquely identify websites on the internet.
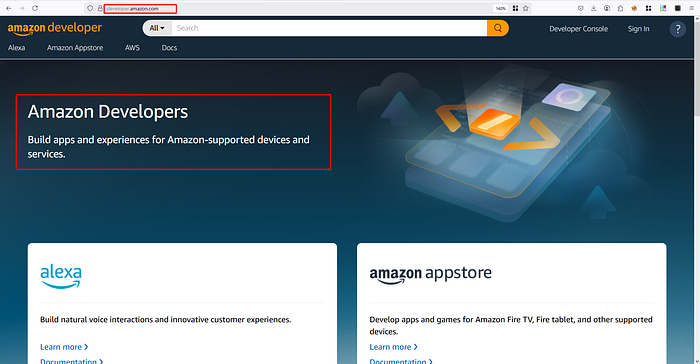
One day, I came across a slightly different URL: developer.amazon.com. Curious about the difference, I looked it up and discovered that this is what's called a subdomain.
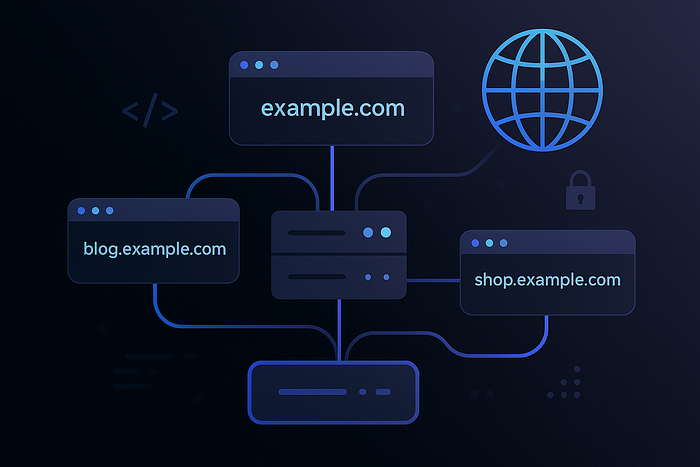
Subdomains are used to organize and separate different sections or environments of a website — like development, support, or blogs — while still being part of the main domain.
In this post, I want to share what I've learned about subdomains — what they are, why they're used, and how you can find them using various tools. This can be especially useful for web developers, cybersecurity enthusiasts.
What is Domain ?
A domain is the main address of a website that people use to visit it on the internet. It's what you type into your browser's address bar to go to a specific website.
For example: google.com is the domain.
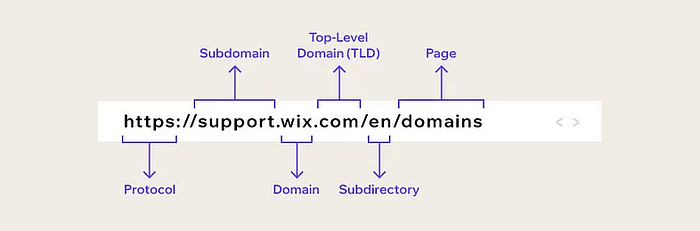
The URL https://support.wix.com/en/domains can be broken down as follows:
- wix.com is the main domain. It is the primary name of the website used to identify it globally.
- support is a subdomain, which is a part of the main domain and typically used to organize or separate content.
- /en is a subdirectory (also called a folder) of the website, often used to indicate language or regional content (in this case, "en" stands for English).
- /domains is a file or subpage located within the /en directory.
What is Subdomain ?
A subdomain is a prefix added to a domain name to organize or separate parts of a website. It appears before the main domain.
Example: If the main website is www.wix.com, the URL https://support.wix.com is a subdomain.
- www.wix.com is the main website where users can access Wix's homepage and services.
- support.wix.com is a subdomain dedicated specifically to customer support and help resources.
Subdomain Enumeration: Tools You Can Use
Sublist3r
Uses search engines and OSINT sources to gather subdomains.
sublist3r -d example.comassetfinder
A fast and simple tool for finding related subdomains using passive sources.
assetfinder --subs-only example.comSubfinder
A robust and modular tool optimized for speed and accuracy in passive subdomain enumeration.
subfinder -d example.comamass
A comprehensive and advanced framework for subdomain enumeration and DNS mapping.
amass enum -d "your target domain"FFUF
A fast web fuzzer often used to brute-force directories or subdomains with a wordlist.
ffuf -w /path/to/wordlist -u https://FUZZ.targetWhy Exposed Subdomains Can Be Dangerous
Subdomain Takeover
If blog.example.com points to a GitHub Pages site that has been deleted, an attacker can recreate that page and control it.
Example:
blog.example.com→ no longer linked to GitHub → attacker claims it.
Leaking Sensitive Info A subdomain like dev.example.com might show unfinished code, test APIs, or even database info.
Example:
dev.example.comshows internal API keys or debug logs.
Weak Security Settings
A subdomain like shop.example.com might not use HTTPS or might run old software.
Example:
shop.example.comruns an outdated version of WordPress without SSL.
Bigger Attack Surface More subdomains = more chances for something to be misconfigured or vulnerable.
Example:
admin.example.com,api.example.com,test.example.com— each is a potential entry point.
Phishing Risks A hacker can create a fake login page on login.example.com to trick users into entering passwords.
Example:
login.example.comlooks real but sends your data to an attacker.
How to Secure Your Subdomains
Prevent Subdomain Takeover
- Regularly check for unused subdomains and remove them.
- Don't leave subdomains pointing to inactive services.
Hide Sensitive Information
- Avoid exposing development or staging environments publicly.
- Protect sensitive subdomains with passwords or IP restrictions.
Use Strong Security Settings
- Always use HTTPS on all subdomains.
- Keep software up to date and apply security patches.
Reduce Your Attack Surface
- Limit the number of subdomains.
- Regularly review DNS records and remove unnecessary ones.
Avoid Phishing Risks
- Secure login subdomains with multi-factor authentication.
- Monitor for any suspicious activity on your subdomains.
Happy Hacking!!!
If you liked this blog post, please give it a like and follow for upcoming wonderful blog posts