Lab: Web shell upload via extension blacklist bypass
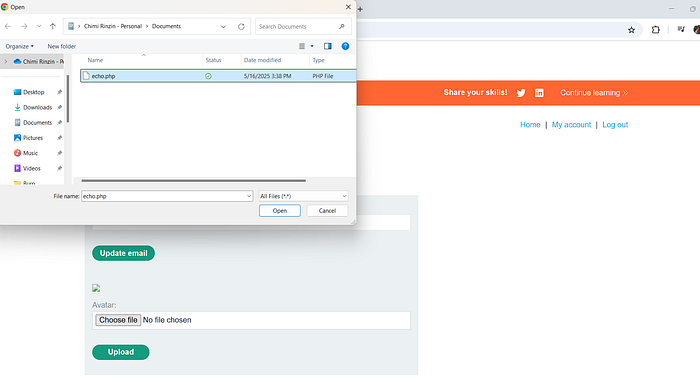
- Access the lab and upload your PHP file.
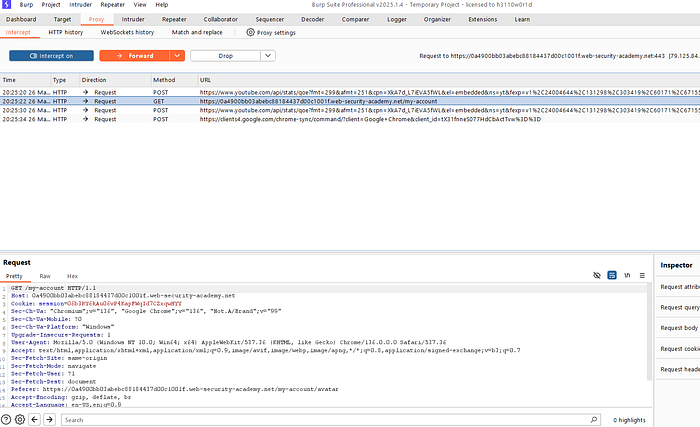
2. Intercept the traffic and check the "GET" request showing ' my account '
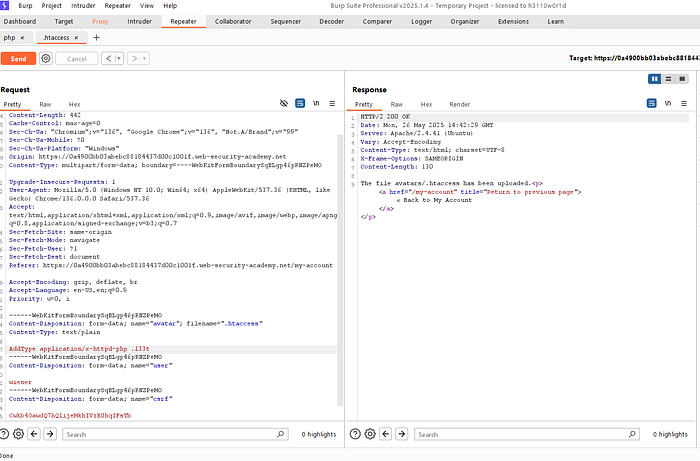
3. Send to the repeater with two file extension, for php and htaccess. Change the filename parameter to ".htaccess" and content-type to "text/plain". Replace the payload to "AddType addition/x-httd-php .l33t".
Here i've given ''.l33t'' to run as a php code. You can give anything you want here instead of ''.l33t ''.
4.Again in your php file, change your filename parameter to "<your filename>.l33t" and send. The file is uploaded now. I'm using ".l33t" here as I have used this for my payload.

5. So to execute ".htaccess" file in php file, return to the original request for uploading your PHP exploit. Forward the request. Turn off your burpsuite and foxy proxy. Check in the browser that you will see the file has been successfully uploaded and click "back to my account".
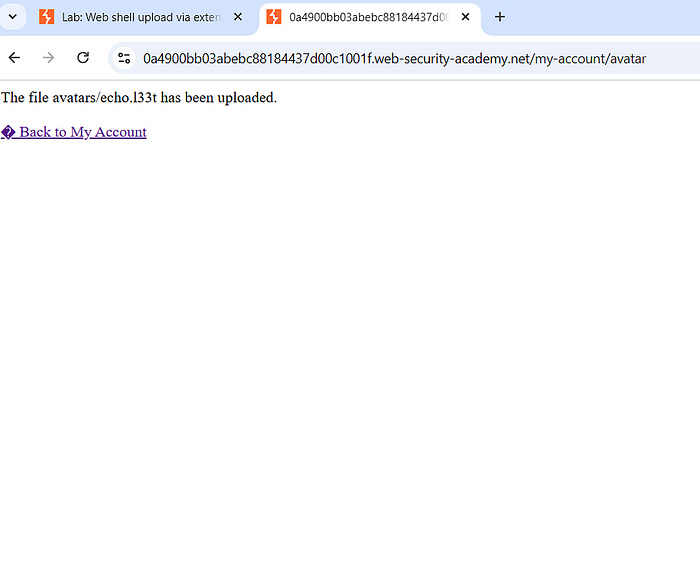
6. After clicking "back to my account", you will return to the previous web-page showing the image. Right-click the image option and choose 'view image in new tab' and the response string or a solution will show up.
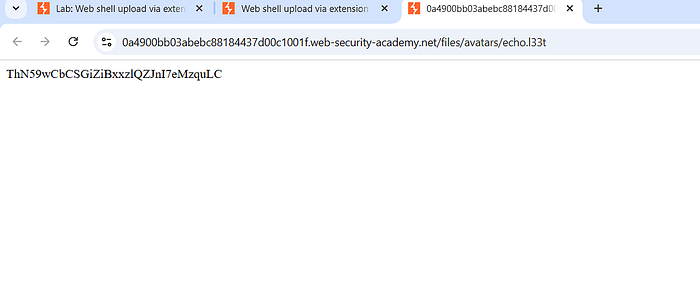
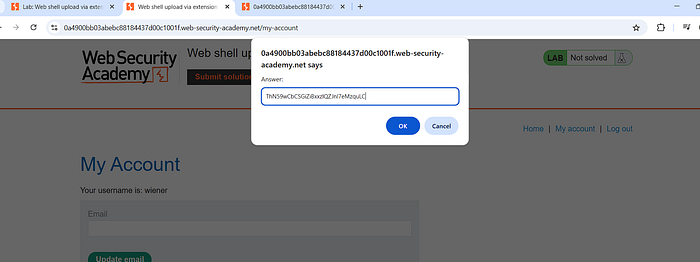
7. Submit the strings or the solutions in your previous tab
8. Lab Solved!