You'll find it humming quietly in factories, energy systems, transit networks, and smart buildings — an invisible backbone powering automation.
It's called PC WORX — a proprietary protocol from Phoenix Contact. It handles everything from PLC programming to real-time control across industrial networks. But here's the part that too many overlooks:
It's often exposed. And when it is, it's dangerously vulnerable.
Let's break it down.
What Is PC WORX?
PC WORX is a protocol developed by Phoenix Contact for:
- Programming PLCs (Programmable Logic Controllers)
- Device-to-device communication
- Monitoring and control over Ethernet networks
It typically runs over TCP/IP, usually on port 1962. Not officially registered but widely used across Phoenix Contact environments — from small installations to national-scale infrastructure.
Where You'll Find It
If your setup involves Phoenix Contact controllers, PC WORX is likely in play. It shows up in:
🏭 Factory automation ⚡ Power generation and utilities 🚊 Rail and transit systems 🏢 Smart buildings 🛠️ Machine-level control systems
It's a niche protocol — but it's everywhere once you start looking.
Why It's a Problem
PC WORX was built for functionality, not for security. Here's what's missing:
- No encryption
- No authentication
- No integrity checking
Older implementations are completely open to the network. No login required. No checks. Just trust.
And guess what? Attackers are catching on.

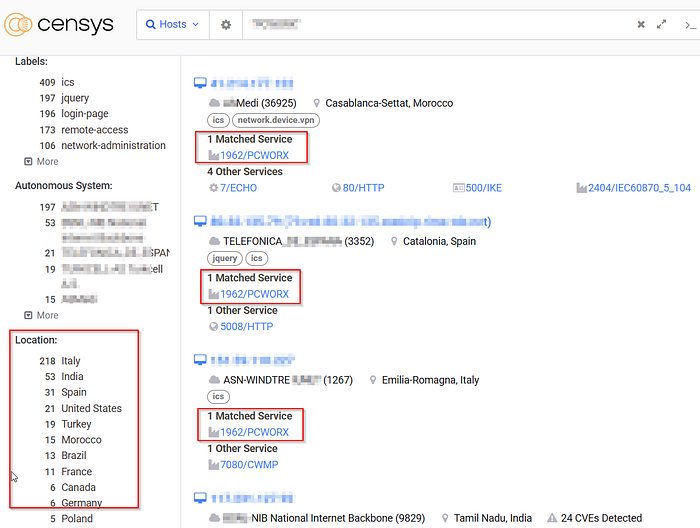
What the Internet Is Telling Us (Latest Scan Data)
From a recent sweep using Censys:
- 🎢 411 endpoints openly running PC WORX
- 🇮🇹 Italy leads in global exposure
- 🚇 22 of those link to systems with actively exploited CVEs
These aren't hypothetical risks. They're real-world exposures, sitting wide open on the internet.
What Could Go Wrong?
If PC WORX is exposed, here's what's on the table for attackers:
- 🎛️ Remote command injection
- 🧠 Unauthorized logic access to your PLCs
- 💥 Full remote code execution (see CVE-2022–40145)
- 🕵️ Man-in-the-middle attacks
- 🔧 Reprogramming of critical industrial controllers
One unprotected port can mean full control of your system.
Defense Strategies (That You Need Yesterday)
Don't wait for an incident. Take action:
🔒 Isolate operational technology (OT) from IT networks 🚫 Block public access to TCP/1962 🧱 Use DPI firewalls that understand industrial protocols 🔍 Monitor for weird traffic (Zeek, Nozomi, Suricata are your friends) 🔄 Update firmware on Phoenix Contact devices regularly 📋 Apply security standards like IEC 62443 and NIST 800–82
TL;DR
PC WORX is niche. But when exposed, it's dangerous. If you have Phoenix Contact devices in your infrastructure, you might be more vulnerable than you think.
Audit now. Patch now. Lock it down.
Because attackers aren't waiting for you to catch up.
Want help scanning for exposed ports or building a mitigation roadmap? Drop a comment — let's secure these networks before someone else takes control and support Palestine.
This research part of oaps_another_attack_surface series, another interesting blog about industrial exposed: The Invisible Threat Lurking in Industrial Networks: GE SRTP And you found me LinkedIn
