In the vast ocean of public code, GitHub has unintentionally become a goldmine for security researchers and bug bounty hunters. From leaked API keys to internal configurations, secrets lie scattered—often unknowingly—across repositories.
Welcome to the world of GitHub Dorking, where a few smart queries can uncover critical vulnerabilities.
💡 What is GitHub Dorking?

GitHub Dorking is the technique of using search queries (dorks) to find sensitive data exposed in public GitHub repositories. This data may include:
- Hardcoded credentials
- API keys and tokens
- Internal endpoints
- Configuration files
- Source code with security flaws
These "dorks" act like laser-targeted Google searches—but within GitHub's search engine.
🧠 Why Should Bug Bounty Hunters Care?
Many companies push code to GitHub without thoroughly reviewing what's committed. CI/CD environments, junior developers, or forgotten forks can leak secrets into public view.

By dorking, you can:
- Discover high-severity bugs passively (no interaction with target infra)
- Find assets or subdomains
- Spot logic flaws or insecure implementation patterns
- Potentially gain initial footholds for deeper testing
And the best part? It's totally legal if you're searching public content and reporting responsibly through the company's bug bounty or VDP.
🔍 Common GitHub Dorks (That Work)
Here are some dorks you can try in GitHub's search bar:
company.com password
company.com api_key
company.com "Authorization: Bearer"
company.com filename:.env
company.com filename:config.json
company.com language:json AWS_SECRET_ACCESS_KEY
company.com language:yaml password🔧 Replace company.com with the target domain, company name, or GitHub username/org.
You can also use org::
org:examplecorp filename:.env
org:examplecorp api_key 🛠️ Tools That Help Automate GitHub Dorking
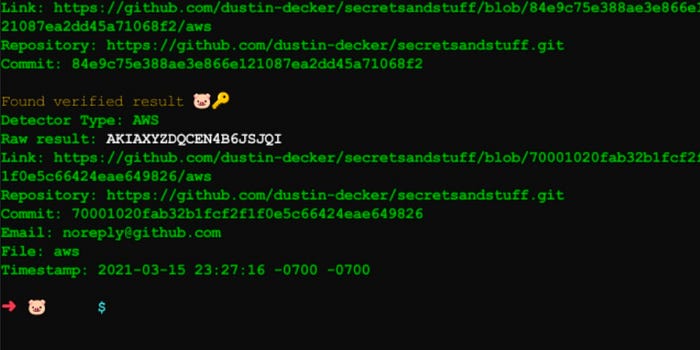
- GitHub Search – Manual but powerful.
- GitHub-Dorks – A tool to automate dork scanning. Repo-Link
- TruffleHog – Scans repos for secrets using entropy and regex. Repo-Link
- Gitleaks – Static analysis for detecting hardcoded secrets. Repo-Link
🚨 Real-World Impact
Many critical reports on HackerOne and Bugcrowd stem from GitHub dorking.
- Leaked Slack tokens that allowed takeover of communication channels.
- AWS keys with full access to cloud infrastructure.
- Internal API documentation exposing undocumented endpoints.
These reports often rank high in severity—with rewards between $500 to $5,000+.
🧭 Best Practices
- Always validate if the leak belongs to the target.
- Respect scope and rules of the bug bounty program.
- Report only publicly available information.
- Don't clone entire repos unnecessarily—respect privacy and bandwidth.
📢 Final Thoughts
GitHub dorking turns open-source intelligence (OSINT) into a high-impact bug bounty tactic. While it's often under estimated, mastering it can give you an edge over others.
Start by picking a target, learning their naming patterns, and experimenting with dorks. With patience and creativity, GitHub might just reveal your next big bounty.
🔁 Found this helpful? Clap 👏, share, or leave a comment
Thank you guys…

