In this write-up I will be showing my thought process behind solving the aforementioned Portswigger Academy challenge. DISCLAIMER! This write-up contains the answer to the challenge, so if you are here for hints, watch out:)
To start this challenge, I first had to find out and understand what custom tags were. In summary; Custom tags in HTML are tags that are named whatever you want, formatted in lower case and with a hyphen. E.g. "<xss-exploit>…</xss-exploit>".
The attack vector for this challenge could be two things. The search functionality or the comment functionality, since both reflect user input. I tested the search functionality first, and it was the correct one.
When i supplied my custom tag as input, "<custom-tag>", the DOM looked like this:
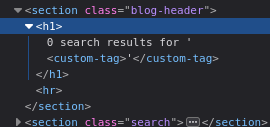
To show that this was vulnerable to XSS, i added an "onmouseover" attribute and, sure enough, it fired off:
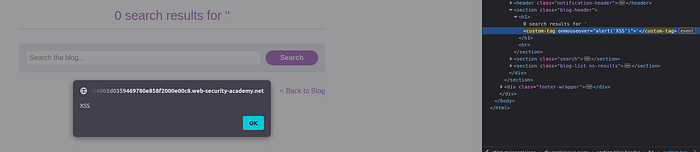
This will not solve the challenge, because it wants the exploit to fire automatically. The way I used to fire the exploit automatically was this: I gave the tag an ID, made the custom tag "tab-able" by using "tabindex=Ƈ'", and gave it an "onfocus" attribute so that when it was focused on, the given script would fire.
Then, using the built in bookmarking feature in HTML, where you can focus on an element on a website by using "#<element-id>", I referred to the element in the URL, and the XSS fired off. This is how the URL looked like (without URL-encoding):
https://<LAB-ID>.web-security-academy.net/?search=<custom-tag+onfocus="alert(document.cookie)"+id="x"+tabindex="1">#xTo solve the lab, we have to supply the URL from our exploit server, and this is how my final exploit looked like:
<script>
location = 'https://0a54003d0359469780e858f2000e00c8.web-security-academy.net/?search=%3Ccustom-tag+onfocus%3D%22alert(document.cookie)%22+id%3D%22x%22+tabindex%3D%221%22%3E#x';
</script>Thank you for taking the time to read this write-up! This is one of my first stories here on Medium, although maybe some time has passed and you are reading this at a later date, but do make sure to check out the few others that I have posted.