Hey Hackers , my name is zack0X01 and today i am gonna share with you one if the bugs i have found which is "Business Logic Vulnerability lead to PII theft & account take over" , When testing the checkout process, I discovered a business logic flaw that could lead to PII exposure and full account takeover.
The logic of the app is easy : if the user is registered ( have an account ) , whne you go to make a purchase as a guest user , it shows "sorry this user already exist you need to login first " , but if you use an email that have never registered befor you can make an order as a guest user
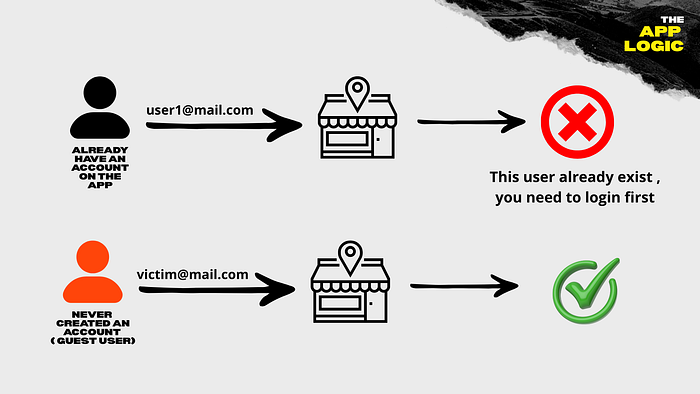
Here's how it works 👇
- The victim places an order as a guest using their email address.
- Once the order is complete, the attacker creates a new account using that same victim email address.
- Because the application does not verify email ownership, the newly created account gets linked to the victim's existing guest order.
- The attacker can now see the victim's order details, including sensitive PII such as name, phone number, and address.
- Additionally, the attacker can modify account details, effectively taking over the victim's account.
If you try to make a purchase using another already registered account, the system correctly prompts you to log in first — meaning this behavior only affects guest checkout users, which makes it a clear authorization issue caused by improper business logic handling.
This type of bug can have a high impact since it allows an attacker to access private user data and control over accounts without any interaction from the victim.
Impact:
- Full Account Takeover
- PII Disclosure (Name, Email, Address, Phone Number)
Bug reported & triaged , i will update you on the bounty when i receive it ;)
follow me on :
X : https://x.com/zack0x01
youtube: https://youtube.com/@zack0x01
instagram: https://instagram.com/zack0x01
check out my store : https://lureo.shop/

