Assalamu'alaikum warahmatullah…
Hello, Allow me to introduce myself — my name is Idris, and I'm a passionate Bug Hunter.
This is my very first post on Medium, so I'll do my best to make this article as engaging as possible. Previously, I've written several interesting articles about tips and insights on Bug Hunting at →
- https://discord.com/channels/941942387813539850/1381829705837314108
- https://discord.com/channels/941942387813539850/1381834196959494144
After diving into the world of bug bounty hunting a few years ago, I quickly realized that you don't always need zero-day vulnerabilities or advanced deep fuzzing tools to earn meaningful rewards. Sometimes, a well-placed "basic" bug is all it takes.
In this article, I'll share a bug I reported through a bug bounty program. The issue was an Improper Access Control vulnerability (OWASP API Top 10 — A01:2021: Broken Access Control) where an API endpoint exposed other users' private records in a well-known SIEM program that competes with platforms like Elastic. I'll explain how I discovered the bug, including the steps and tools I used, so readers can better understand how to identify similar vulnerabilities in their own bug bounty research.
No special tools except Burp Suite and the logic of a bug hunter.
This is the story of how I found a simple Improper Access Control vulnerability in a staging environment — a finding that resulted in a $1,800 (High) payout. If you're new to bug bounty hunting or just need a reminder that the fundamentals still matter, this story is for you.
On Wednesday, August 13 at 21:56, I received an email inviting me to join a private program to test their system — with the bounty amount already listed, as shown in the image below:

When the invite arrived, unfortunately I was traveling to attend an international hacking event in Indonesia. So, long story short, I began hunting a few days after the event ended. On August 18, 2025 I opened my toolkit (my personal laptop) and started probing the target web application, exploring its flow little by little.
Let's call the target REDACTED.COM — http://redacted.com:8000/en-US/app/launcher/home. I first checked the main page. As the Owner, I created a private note that only I could see, then invited a new user to act as an "attacker" with a very low-privilege role (User).
At first glance the server logic in the UI looked correct: a regular User should not be able to see private notes belonging to an Admin or other users with the same role. A pro tip from experienced bug hunters:
Never trust what the UI enforces. If the UI restricts access, always test the underlying API endpoints and craft several clever scenarios.
Acting as the attacker, I then attempted to call the API endpoint for the Admin's private notes.
GET /en-US/Redacted/__raw/servicesNS/nobody/system/storage/collections/data/HomePageAdminConfig?query=%7B%22%24or%22%3A%5B%7B%22_key%22%3A%22cards%22%7D%2C%7B%22_key%22%3A%22settings%22%7D%2C%7B%22_key%22%3A%22domains%22%7D%5D%7D HTTP/1.1
Host: Redacted.com:8000
X-Requested-With: XMLHttpRequest
Accept-Language: id-ID,id;q=0.9
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/138.0.0.0 Safari/537.36
Content-Type: application/json
X-Redacted-Form-Key: 9008046797052257836
Accept: */*
Accept-Encoding: gzip, deflate, br
Cookie: █████████
Connection: keep-aliveAs expected, the attacker still couldn't access the Admin's private note — the server returned a 403 Forbidden response. 😔
I decided to try a different scenario while staying within the Private Notes feature. As the Owner, I changed the note's visibility to Admin-only (so the note could be viewed by any member with the Admin role).
Then I switched back to the attacker account and called the same API endpoint again.
GET /en-US/Redacted/__raw/servicesNS/nobody/system/storage/collections/data/HomePageAdminConfig?query=%7B%22%24or%22%3A%5B%7B%22_key%22%3A%22cards%22%7D%2C%7B%22_key%22%3A%22settings%22%7D%2C%7B%22_key%22%3A%22domains%22%7D%5D%7D HTTP/1.1
Host: Redacted.com:8000
X-Requested-With: XMLHttpRequest
Accept-Language: id-ID,id;q=0.9
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/138.0.0.0 Safari/537.36
Content-Type: application/json
X-Redacted-Form-Key: 9008046797052257836
Accept: */*
Accept-Encoding: gzip, deflate, br
Cookie: █████████
Connection: keep-aliveAnd guess what? It felt like hitting a jackpot — finding an extra 10 grams of gold for free. I was relieved and thrilled to discover that the API response leaked an Admin-only private note, even though the attacker account only had a regular User role.
Yes!
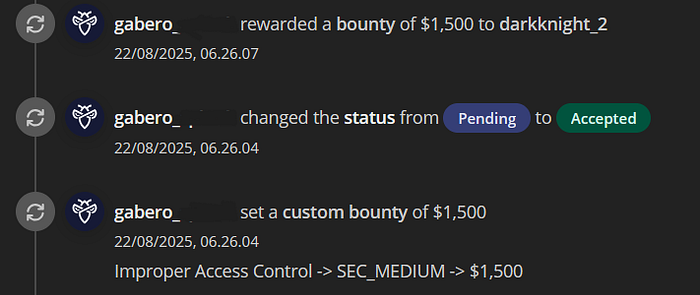
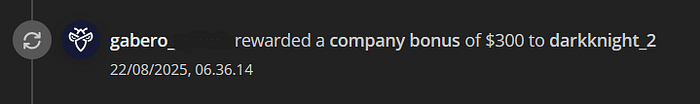
I immediately recorded a video PoC and drafted a report on the target's private bug bounty program via the well-known cybersecurity platform Intigriti. The report was filed on August 18, 2025 at 04:27:31. Four days later I was surprised to receive a direct reward of $1,500 — classified as a High severity Improper Access Control issue according to the bounty table — plus a $300 bonus. The total payout for that single report was $1,800, paid on August 22, 2025 at 06:26:07.

# Steps performed on my private target
- As Admin, invite an attacker account with any low-privilege role or capability (for example, a role with the
accelerate_searchcapability). - As Admin, create a new account and a note marked Shared by my administrator, then restrict that note so it is visible only to fellow Admins.
- As the attacker, log in and open the Bookmarks page at
http://redacted.com:8000/en-US/app/launcher/home. The attacker cannot see Admin-only bookmarks via the UI. - As the attacker, call the vulnerable API endpoint directly.
- In the REST API response, the server leaks bookmark information that should be visible only to Admins.
Impact
- Severity: High (Private Bookmark leak)
- Wider risk: Violation of user privacy; exposure of sensitive or administrative data to unauthorized users.
Timeline
- Discovered: Agust 18, 2025
- Patched: Agust 24, 2025
- Rewarded: Agust 22, 2025 — $1,800
I'm not sure whether a CVE was issued for this report, as the program had not yet published a new release.
Terima Kasih telah membaca dengan seksama !
Thank you for reading carefully! I hope you enjoyed this write-up — God willing, there are many more findings and interesting tips & tricks I'll share. ❤️
Contact Me
If you have questions, feedback, or want to connect and talk security, feel free to reach out:
- https://www.linkedin.com/in/mohammad-suropati-4bb557280/
- https://www.instagram.com/muhammadidris0904/
- https://www.linkedin.com/in/mohammad-suropati-4bb557280/
- https://www.instagram.com/muhammadidris0904/
- Sebagai Penyerang, masuk dan buka halaman Bookmark di
http://152.42.163.233:8000/en-US/app/launcher/homePenyerang tidak dapat melihat Bookmark khusus Admin - Sebagai Penyerang, buat panggilan ke titik akhir berikut