What Apple's $5M Vulnerability-Bounty Upgrade Teaches Us About Fighting Spyware
Not a Medium member? Click here to read the full story for FREE.
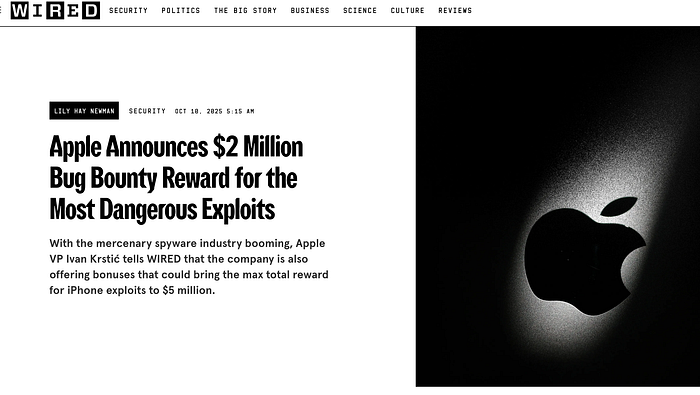
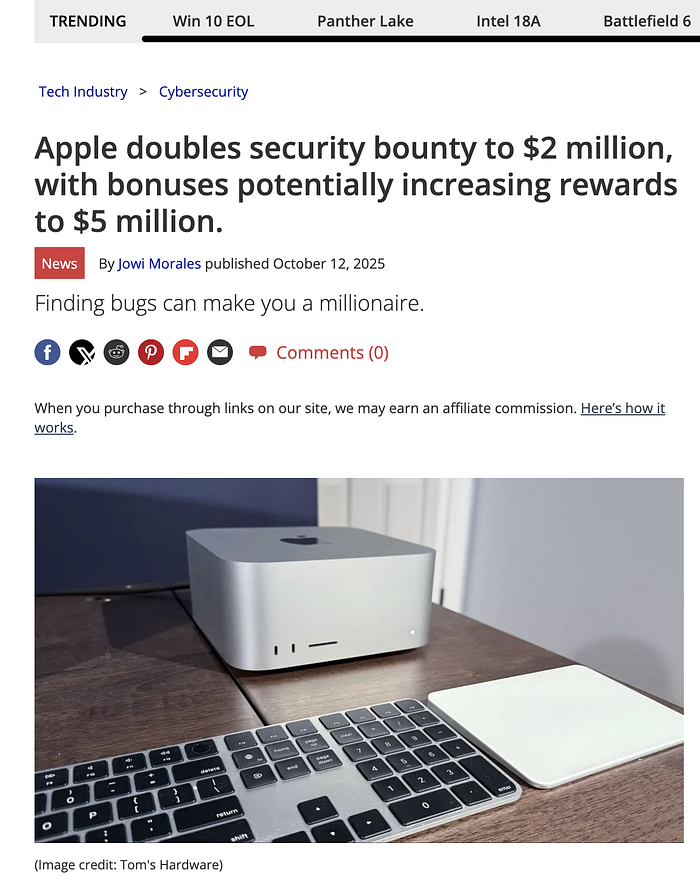
Apple just dropped a bomb on the security world: it's doubled the top payout in its Security Bounty program to $2 million for the most dangerous exploit chains, and added bonus rules that can push a single payout above $5 million. The company also opened more specific bounty categories (with clear dollar amounts for nine types of vulnerabilities) and said it will provide 1,000 secured iPhone 17 devices to at-risk civil-society groups — plus expand its Security Research Device program for researchers.

This isn't marketing theater. It's a strategic move to realign incentives — making it far more attractive for researchers to disclose vulnerabilities responsibly to Apple rather than sell them to mercenary spyware vendors.Here's what changed, why it matters, and what different people (researchers, defenders, regular users) should actually do next.
The headline facts (quick)
- Top payout for zero-click remote code execution (the nastiest class of spyware exploit) is now $2M; combined bonuses (Lockdown Mode bypass, discoveries in beta software, etc.) can push awards past $5M.
- Apple published specific reward ranges across nine categories — from modest $1,000 "encouragement" awards up to $1M (or more for the worst remote attacks).
- Apple says it has paid ~$35M (or more, depending on reporting) to over 800 researchers since 2020; several previous single payouts reached the $500K level.
- Apple will distribute 1,000 iPhone 17 "secure" devices to civil-society groups and make new Security Research Devices (special researcher iPhones) available — application window for SRD is open through Oct 31, 2025.
Why Apple doubled down — short version
There's an entire underground market for zero-day exploits used by mercenary spyware (Pegasus and the like). Those buyers will pay huge sums to stay anonymous and weaponize vulnerabilities against journalists, activists, and dissidents. Apple's calculus: raise the legitimate reward high enough that ethical researchers prefer to sell findings to Apple (and get paid and get credit) rather than to secretive spyware brokers. That both accelerates fixes and reduces the supply of exploits to abusive actors.
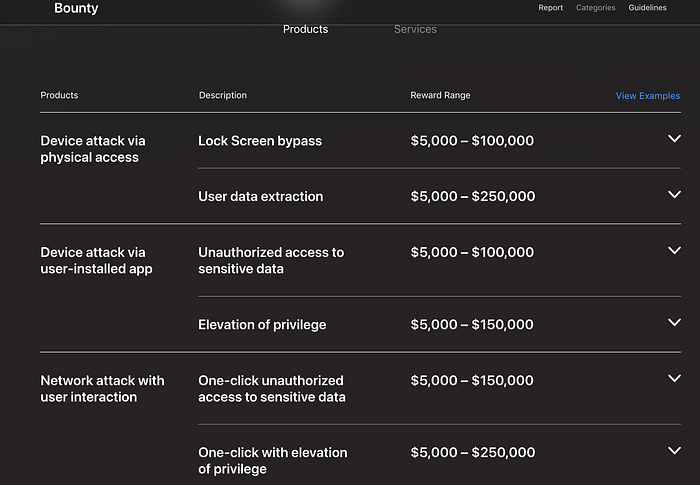
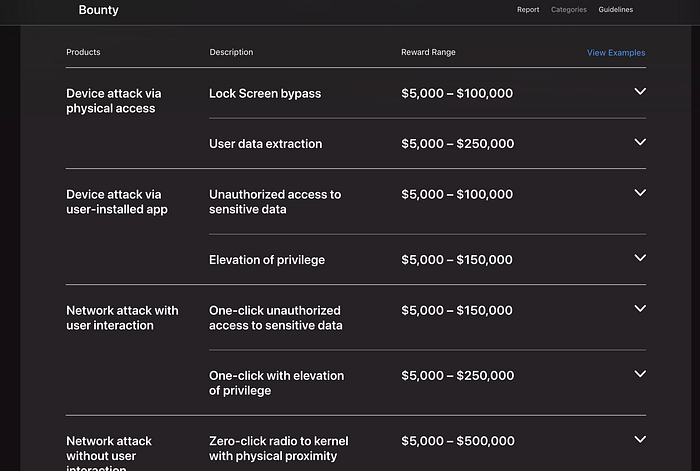
Breaking down the new categories (what the dollar signs mean)
Apple's announcement is unusually explicit about how much it values specific attack vectors — that's important because specificity shapes researcher focus.
- One-click (user interaction) remote attack — $1,000,000 Social-engineering + a single click = big blast radius. Apple raised this because those vulnerabilities remain common and risky.
- Zero-click remote code execution — $2,000,000 (base) The rarest and most dangerous: the attacker needs no interaction from the user. That's the class most often abused by commercial spyware vendors. Bonuses can push this much higher.
- Wireless proximity attacks (Bluetooth/Wi-Fi/N1/C1-class chips) — $1,000,000 Apple explicitly called out attacks against its in-house chips (C1/C1X modem, N1 wireless). This both rewards and challenges researchers to focus on lower-level wireless paths.
- Unauthorized iCloud access — $1,000,000 Bypass iCloud auth and you get access to photos, backups, contacts — high value and high impact. Apple says this is a priority area.
- WebKit chains causing unsigned code execution — $1,000,000 WebKit has been the traditional path for drive-by browser-based compromises; a chain that leads to arbitrary code execution is treated as equivalent to a remote takeover.
- Physical contact attacks on locked devices / sandbox escapes / Gatekeeper bypasses / smaller WebKit sandbox escapes / "encouragement" awards — amounts vary from $50K down to $1K depending on scope and impact.
Apple's bounty categories page lists the full table and examples — I recommend anyone interested read it directly for precise eligibility and example scenarios.
Why the change matters practically
- Research flow shifts: With bigger, clearer prizes and fast validation paths, more experienced researchers will spend time chasing complex exploit chains for Apple rather than for a private buyer. That should shorten patch windows for critical vulnerabilities.
- Defensive product + incentive combo: Apple has been adding defensive primitives (Lockdown Mode, Memory Integrity Enforcement on iPhone 17). Now it layers incentives to find holes in those defenses so they can be fixed before abuse.
- Civil society protection: Giving 1,000 hardened iPhone 17s to at-risk organizations is a practical mitigation step — not perfect, but better than only talking about policy.
What this means for different readers
If you're a security researcher
- Consider applying for a Security Research Device (SRD) — Apple's application is open and the program runs on an annual cycle (apply by Oct 31, 2025 for the 2026 cohort). SRDs come with shell access and beta builds and automatically feed eligible findings into the bounty program.
- High complexity = high reward. If you can build exploit chains that bypass Lockdown Mode and work in beta builds, you could be eligible for those extra bonuses that push totals above $5M.
If you run a civil-society org or are at risk of targeted spyware
- Apple's pledge to donate 1,000 secured iPhone 17 devices is aimed at people exactly in your situation. Keep an eye on official Apple channels or partner NGOs for distribution details.
If you're an everyday user
- The headline isn't "Apple solved spyware." It's "Apple is investing in detection and incentives." Do the basics: keep your devices updated, enable Lockdown Mode if you're likely targeted (journalists, activists), and install updates from Apple quickly. The changes reduce systemic risk over time, but they don't make you invincible overnight.
A short, practical checklist
- Researchers: read the Apple Security Bounty page and SRD page, prepare an SRD application, and make sure your reporting is thorough (good reproduction steps + exploit demonstration = faster validation and bigger award).
- NGOs / at-risk users: monitor Apple's civil-society device distribution announcements and coordinate with local digital-security NGOs.
- Everyone else: update iPhones and Macs, enable recommended privacy options, and treat security updates as urgent (not optional).
Closing thought — a small but important reality check
Money reshapes markets. By raising the official price of the most dangerous exploits and offering researcher devices and protected phones to vulnerable groups, Apple is trying to change the math that powers the mercenary-spyware market. It's not a silver bullet — vulnerabilities will still exist — but it's a strategic and expensive signal: if you find a critical exploit, there's now a clear, high-value route to get paid and get it fixed. That alignment matters.
If you liked the article, show your support with a clap 👏 and follow me! Feel free to highlight your favorite parts too. Your engagement keeps me inspired!

