Imagine uncovering hidden doors to a company's digital fortress — servers, applications, or even forgotten admin panels that could expose critical vulnerabilities. This is the power of subdomain enumeration, a cornerstone of ethical hacking and reconnaissance. Whether you're a bug bounty hunter or a cybersecurity enthusiast, mastering this skill expands your ability to find weaknesses before attackers do. In this beginner-friendly guide, we'll break down what subdomain enumeration is, why it matters, and how to do it effectively using free tools and techniques.
What Is Subdomain Enumeration?
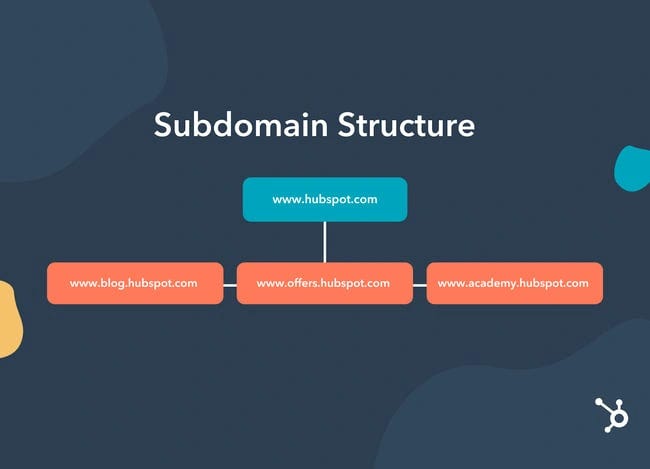
Subdomains are extensions of a main domain name, likeblog.hubspot.com or academy.hubspot.com, where hubspot.comis the root domain. Each subdomain can point to different servers or applications, often hosting unique functionalities. Subdomain enumeration is the process of discovering these subdomains to map out a target's digital footprint, known as its attack surface — all the points where an attacker might strike.
Why It Matters
Subdomains often hide overlooked assets, making them prime targets for both ethical hackers and malicious actors. Here's why enumeration is critical:
- Uncover Hidden Systems: Development environments (e.g.,
dev.hubspot.com) may have weaker security than production systems. - Expose Sensitive Portals: Admin panels (e.g.,
admin.hubspot.com) might reveal login pages or APIs. - Prevent Subdomain Takeovers: Forgotten subdomains with expired DNS records can be hijacked, as noted in resources like the 0xffsec Handbook.
For organizations, regular enumeration ensures all assets are monitored. For ethical hackers, it's a way to identify risks within bug bounty program scopes.
Important: Always obtain explicit permission before scanning, as unauthorized enumeration can violate laws like the U.S. Computer Fraud and Abuse Act (CFAA) or resemble a denial-of-service (DoS) attack if not rate-limited.
Types of Subdomain Enumeration
There are two main approaches to subdomain enumeration: passive and active. Passive methods use public data without contacting the target, making them stealthy. Active methods query the target directly, which can reveal more but risks detection. Let's explore both.
Passive Enumeration: Stealthy Recon with OSINT
Passive enumeration relies on Open-Source Intelligence (OSINT) — publicly available data from sources like search engines or certificate logs. It's ideal for staying under the radar.
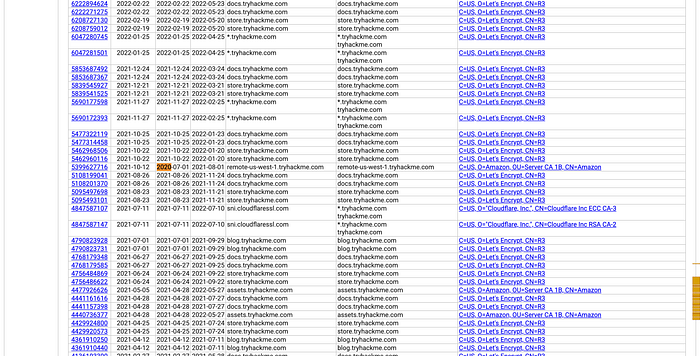
1. Certificate Transparency Logs with crt.sh
When websites secure SSL/TLS certificates, Certificate Authorities (CAs) log them in public Certificate Transparency (CT) logs to prevent misuse. These logs often reveal subdomains, especially for wildcard certificates (e.g., *.example.com).
How to Use crt.sh:
- Visit crt.sh.
- Enter the target domain (e.g.,
tryhackme.com). - Filter results by date or issuer to see historical entries.
Example: Searching tryhackme.com might uncover shop.tryhackme.com from a log dated 2020–12–26.
2. Search Engine Dorking
Search engines like Google index billions of pages, including subdomains. Advanced queries called dorks help you find them.
Example Google Dork:
site:*.example.com -site:www.example.comThis finds subdomains of example.com excluding the main site. For instance, site:*.tryhackme.com- site:www.tryhackme.com might reveal access.tryhackme.com.
Other Useful Dorks:
site:example.com filetype:pdf: Finds documents that might leak subdomains.inurl:admin site:example.com: Uncovers admin panels.
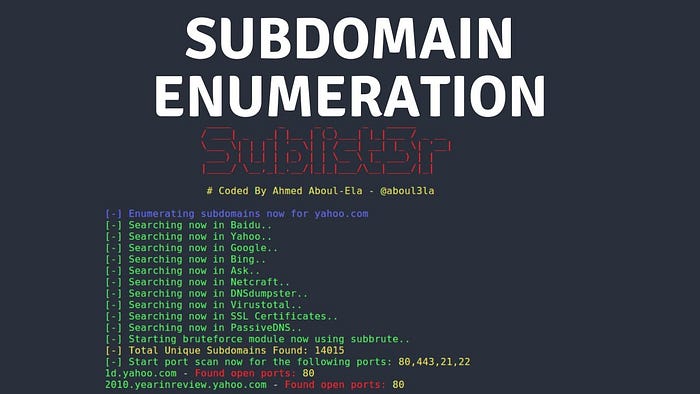
3. Automated OSINT with Sublist3r
Sublist3r is a Python tool that automates OSINT by querying sources like Google, Bing, Netcraft, and VirusTotal. It also supports brute-forcing subdomains.
Installation:
git clone https://github.com/aboul3la/Sublist3r.git
pip install -r requirements.txtExample Command:
python sublist3r.py -d acmeitsupport.thm -v -o results.txt- -d: Specifies the target domain.
- -v: Enables verbose output.
- -o: Saves results to a file.
This might reveal subdomains like mail.acmeitsupport.thm. You can filter results with grep, e.g., grep admin results.txt, or use the -p flag to scan specific ports.
Active Enumeration: Digging Deeper with Brute Force
Active methods directly query the target's DNS servers or web servers, using wordlists of common subdomain names (e.g., admin, api, test). These are more likely to be detected, so use them cautiously.
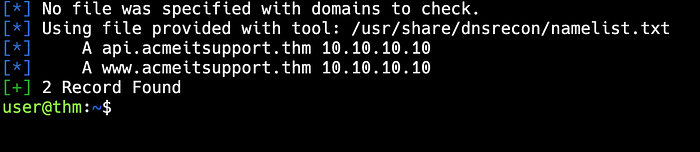
1. DNS Brute Force with dnsrecon
dnsrecon tries wordlist entries as subdomains to see if they resolve.
Example Command:
dnsrecon -t brt -d acmeitsupport.thm -D /path/to/wordlist.txt-t brt: Specifies brute force mode.-D: Points to a wordlist (e.g., SecLists' namelist.txt).
This might uncover subdomains like mail.acmeitsupport.thm. Use rate limiting (e.g., — threads 10) to avoid overwhelming the target.
2. Virtual Host Enumeration with ffuf
Some subdomains aren't in public DNS but are configured on servers via HTTP Host headers. ffuf is a fast fuzzing tool to discover these.
Installation:
go install github.com/ffuf/ffuf/v2@latestExample Command:
ffuf -w /usr/share/wordlists/SecLists/Discovery/DNS/namelist.txt -H "Host: FUZZ.acmeitsupport.thm" -u http://MACHINE_IP -fs 1234-w: Specifies the wordlist.-H: Fuzzes the Host header withFUZZas the placeholder.-fs: Filters common response sizes (e.g.,1234bytes) to highlight unique responses.
This might reveal internal.acmeitsupport.thm. Use ffuf's interactive mode (press Enter during execution) to tweak filters live.
Advanced Tools for Power Users
Once you're comfortable with the basics, explore these advanced tools:
- Recon-ng: A modular framework with subdomain modules (e.g., recon/domains-hosts/brute_hosts).
- SubDomainizer: Scrapes URLs for subdomains, ideal for finding hidden assets.
- Massdns: A high-performance DNS resolver for large-scale brute forcing.
Integration Tip: Pipe Sublist3r output into ffuf for a hybrid passive-active scan:
python sublist3r.py -d example.com -o subdomains.txt && ffuf -w subdomains.txt -H "Host: FUZZ.example.com" -u http://MACHINE_IPBest Practices and Legal Considerations
- Stay Ethical: Always operate within bug bounty scopes or with explicit permission. Unauthorized scanning can lead to legal consequences.
- Rate Limit: Use rate-limiting options in tools like dnsrecon or ffuf to avoid DoS-like behavior.
- Combine Tools: Start with passive methods (e.g., crt.sh, Sublist3r) to minimize detection, then use active methods for deeper insights.
- Document Findings: Save outputs (e.g., results.txt) for analysis and reporting.
Conclusion: Start Your Recon Journey
Subdomain enumeration is a gateway to mastering reconnaissance in ethical hacking. By uncovering hidden assets, you can help organizations secure their systems or earn bug bounty rewards. Start practicing in safe environments like TryHackMe or HackTheBox, and experiment with tools like Sublist3r and ffuf. The more you explore, the better you'll get at finding those hidden digital doors.
Connect with Me
Reference: