If you're preparing for a SOC 2 audit, chances are you're juggling a mix of business plans, customer demands, and a growing pile of security policies.
It's exciting — SOC 2 compliance unlocks bigger contracts, reassures business partners, and proves you take customer data protection seriously. But it can also feel daunting: rigid requirements, external auditors, and a mountain of evidence to manage.
The truth? A SOC 2 audit is designed to test how well your security controls and processes are operating. Many organisations out there stumble in the same five areas — but with the right preparation (and a little automation), you don't have to.
Having worked closely with service organisations through their audits, we've seen what works.
This guide walks through the most common SOC 2 audit mistakes and how to avoid them, so your audit feels less like chaos — and more like progress.
Mistake 1: Treating the SOC 2 Audit Like a Sprint
What happens: Organisations often underestimate how long the SOC 2 process takes. The average journey — from defining scope through to receiving your final report — runs six months to a year. Teams that leave preparation too late scramble to collect evidence, often missing key gaps in internal controls.
Why it matters: A SOC 2 audit assesses how effectively you protect your organisation's and customer data. It's not about one snapshot at a specific point in time. Especially for a Type II report, you're proving your security controls are operating effectively across months, not days.
How to avoid it:
- Define your scope early, including relevant systems, services, and third-party SaaS companies.
- Run a readiness or gap analysis to flag missing controls.
- Remember: security is the only mandatory criterion in the five trust services criteria (security, availability, processing integrity, confidentiality, privacy). Decide whether your business partners and customers expect you to cover more.
- Build evidence collection into day-to-day processes instead of waiting for audit panic week.
Hicomply Helps: The platform keeps you on track with workflows that map directly to the trust services criteria. Evidence is collected automatically across the audit period, so you don't end up in last-minute scramble mode.
Mistake 2: Ignoring Scope and Stakeholders
What happens: You forget that SOC 2 is a company-wide effort. Teams assume it's just for IT, while departments like HR, Finance, and Operations quietly hold crucial evidence — from hiring practices to financial reporting systems.
Why it matters: SOC 2 audits look at how your organisation manages sensitive data and runs data processing across departments. It's about your whole internal control environment, not just firewalls and passwords. Many businesses and investors in North America can only do business with organisations that demonstrate their information security with a SOC 2 report.
How to avoid it:
- Map all stakeholders — IT, HR, Finance, Customer Success — and assign control owners.
- Document where customer data lives (databases, SaaS tools, data centers).
- Engage other stakeholders early. Don't make SOC 2 an IT-only project.
Hicomply Helps: With Hicomply, you can assign control owners across departments and track progress in one dashboard. Everyone — from HR to Finance to IT — knows what's theirs, and nothing falls through the cracks.
Mistake 3: Evidence Chaos
What happens: Your external auditor asks for access logs. You respond with an Excel sheet called "Controls-FINAL-v7." Evidence is scattered, inconsistent, or unverified.
Why it matters: A SOC 2 audit is an attestation engagement. That means certified public accountants (AICPA) or another independent auditor must review your evidence to provide assurance. If your materials are messy, auditors dig deeper — costing you time, money, and credibility.
How to avoid it:
- Centralise evidence for each of the five categories of trust services criteria.
- Use compliance automation tools to streamline collection — especially recurring evidence like access reviews, employee security training, and change management logs.
- Keep detailed information linked to each control. Don't make auditors guess which file proves what.
Hicomply Helps: Policies, risk assessments, and documentation can be auto-generated from templates aligned with SOC 2 requirements. Evidence is centralised, time-stamped, and mapped to each criterion — so your independent auditor sees one clear picture, not a dozen messy files.
Mistake 4: Forgetting People and Processes
What happens: Your security systems look great on paper, but employees are reusing "Password123" and ignoring outdated security policies.
Why it matters: SOC 2 reports don't just check your tech — they also evaluate your organisation controls, processes, and people. The common criteria cover cultural aspects like onboarding, access management, and role clarity. Without strong security policies and regular training, your controls aren't truly operating effectively.
How to avoid it:
- Train employees on data security, confidentiality, and integrity, confidentiality and privacy obligations.
- Keep policies updated and practical (nobody reads a 100-page PDF).
- Design and implement required internal controls to address identified gaps.
- Document everything: auditors want proof that your processes run as written.
Hicomply Helps: Automate reminders for security training, policy reviews, and staff tasks. Instead of nagging your colleagues, the platform does it for you — keeping your security posture consistent and your processes actually followed.
Mistake 5: Misunderstanding SOC 2 Reports
What happens: Some organisations confuse a Type I SOC report (covering a specified date, showing controls exist at a single point) with a Type II report (proving controls are operating effectively over time). Others assume their SOC 2 report is only for auditors, when in reality it's a vital trust tool for clients, customers, and business partners.
Why it matters: A SOC 2 report is more than a compliance checkbox. It reassures other stakeholders — from investors to procurement teams — that your security, availability, processing integrity, confidentiality, and privacy practices meet international standards. A weak or incomplete report slows down deals.
How to avoid it:
- Choose the right report type for your stage of growth (Type I vs. Type II).
- Use your final report proactively with customers, not just your board.
- Remember: many SaaS providers and SaaS companies rely on SOC 2 compliance to close deals with enterprise clients.
Hicomply Helps: Whether you're aiming for a Type I SOC report or a Type II report, Hicomply guides you through the differences and keeps your audit evidence aligned. Once your final report is issued, you can upload it into the platform — making it easy to share with customers, investors, or other stakeholders.
Why SOC 2 Matters (and Why You Can't Ignore It)
A SOC 2 audit isn't just a compliance framework checkbox. Done right, it:
- Identifies vulnerabilities, risks, and inefficiencies in your data security and privacy controls.
- Strengthens your security posture so you can operate confidently.
- Signals to customers and business partners that protecting sensitive information is a core value.
- Provides assurance through a recognised international standard maintained by the American Institute of Certified Public Accountants (AICPA).
Put simply: SOC 2 compliance is about building trust. And in today's market, trust = growth.
Quickfire FAQs
How long does a SOC 2 audit take? Between 6–12 months, depending on your audit type, readiness, and whether you automate evidence collection.
Who performs a SOC 2 audit? An independent auditor (licensed CPA firm) under the American Institute of Certified Public Accountants.
What are the five trust service principles? Security, availability, processing integrity, confidentiality, privacy.
Do startups need SOC 2? If you're a SaaS company aiming for enterprise clients, yes. Procurement teams expect a SOC 2 report before signing.
What's the single most important criterion? Security. It's the only mandatory one, though most companies choose additional criteria to reassure customers.
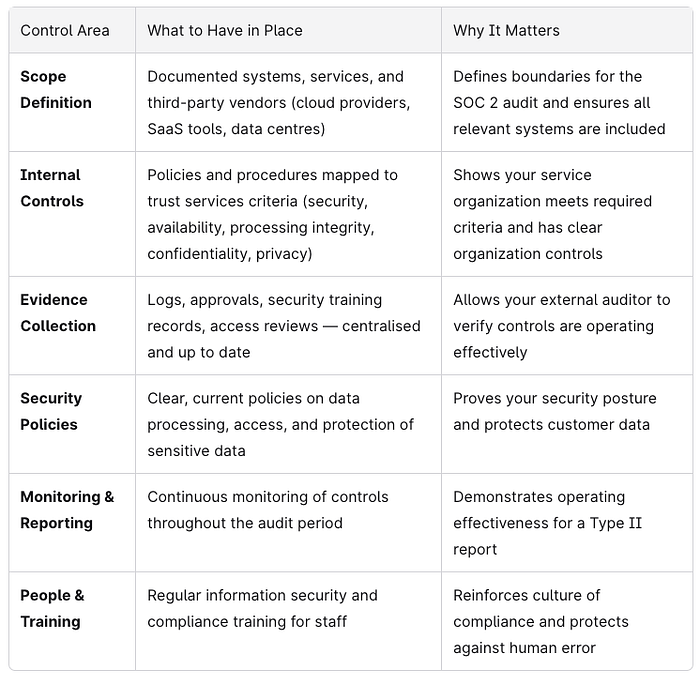
The Audit-Ready Checklist
Before facing your external auditor, confirm you can tick these off:
Ready to Skip the Audit Headaches?
Passing a SOC 2 audit isn't about luck or scrambling at the last minute. It's about building processes that protect customers' data, operate effectively, and scale with your business.
Avoid these five common mistakes, and you'll set yourself up not just for a clean SOC 2 report, but for stronger relationships with clients, customers, investors, and business partners.
And the best part? You don't need to slog through it manually. With Hicomply, you can automate evidence collection, track your own controls against rigid requirements, and be audit-ready long before your independent auditor even sends the first email.
Try the interactive demo and see how Hicomply makes SOC 2 compliance less of a headache — and more of a growth driver.
Originally published at https://www.hicomply.com.

