You scroll through your photo gallery, open a harmless-looking image — and unknowingly trigger a hidden command. Sounds like science fiction?
It's not. In today's digital battlefield, even a simple JPEG can become a hacker's Trojan horse.
Behind the smiling faces and scenic landscapes lies a silent threat: malicious code embedded deep within image metadata.
Welcome to the shadowy world where pictures aren't just pixels — they're payloads.
In this article, I will show you how to hide shell commands inside image files and how to run them.
Let's get started.
⚠️ This is for educational purposes only. Do not use these techniques without explicit permission. Unauthorised use may violate laws and ethical guidelines. Stay curious, stay responsible. 🛡️📚
Understanding how it works
JPEG images have a metadata section that is used by the cameras to store information like the image's origin, camera settings, geolocation, timestamps, and user-defined annotations.
These metadata fields are not rendered visually, but programs like Photoshop and GIMP can use them.
Those fields can be exploited in order to place our commands or even small binaries and then retrieve them and execute them.
The technique does not alter the pixel data, ensuring visual integrity while embedding functional payloads.
Embedding Shell Commands into JPEG Metadata
To begin, we require a clean JPEG image, and second, we need to install software called exiftool which allows the manipulation of the metadata of a JPEG file.
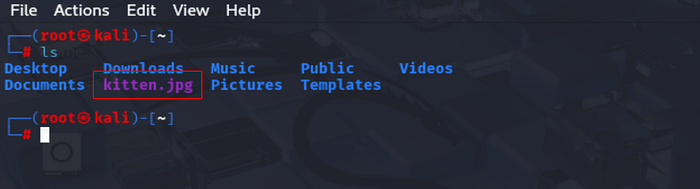
Step 1: Acquire a Base Image
We use a publicly available, copyright-free image for demonstration:
wget https://upload.wikimedia.org/wikipedia/commons/b/bc/Juvenile_Ragdoll.jpg -O kitten.jpgThis image serves as our carrier file — visually unchanged throughout the process.
Step 2: Install ExifTool
On Debian-based systems:
sudo apt-get update && sudo apt-get install libimage-exiftool-perl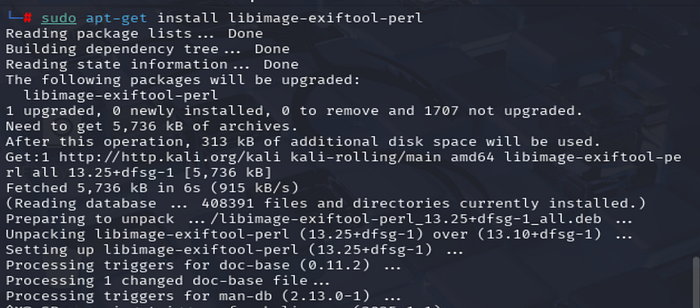
On macOS (via Homebrew):
brew install exiftoolVerify installation:
exiftool -ver
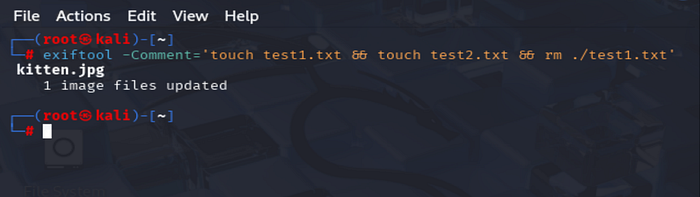
Step 3: Inject a Shell Command into the Comment Field
We embed a compound command that creates two files and removes one:
exiftool -Comment='touch test1.txt && touch test2.txt && rm ./test1.txt' kitten.jpgThis command writes the following command to the "Comment" metadata field.
To confirm injection:
exiftool -Comment kitten.jpgOutput:-
Comment : touch test1.txt && touch test2.txt && rm ./test1.txt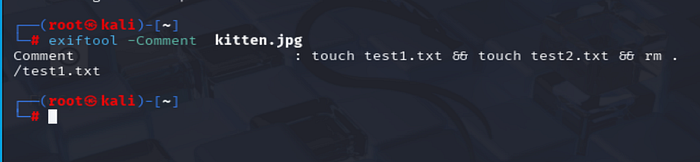
How to execute the commands within the image
To execute the commands, you need a combination of exiftool and eval , the first one extracts the "Comment" metadata and the second one executes the metadata text as shell commands.
eval "$(exiftool -Comment kitten.jpg | cut -d':' -f2-)"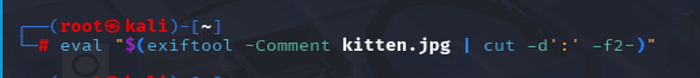
Breakdown:
exiftool -Comment kitten.jpgoutputs:Comment : <payload>cut -d':' -f2-removes the field label, retaining only the payloadxargstrims leading/trailing whitespace (more robust than manual space removal)evalinterprets the resulting string as a shell command.
Security Warning: Using
evalon untrusted input is inherently dangerous. In production or forensic contexts, always validate or sandbox such operations.
Verifying Execution Outcome
After running the command:
test2.txtshould existtest1.txtshould not (due to&&chaining requiring prior success)
ls -l test*.txt
# Output: -rw-r--r-- 1 user user 0 Oct 20 10:00 test2.txt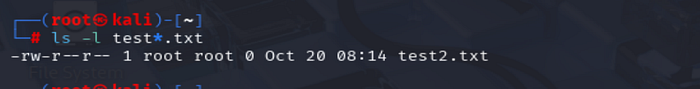
We are sure that the file test1.txt created and deleted because test2.txt is executed only upon successful execution of the first command.
Ethical and Practical Considerations
While this technique is academically intriguing, its real-world utility is limited by several factors:
- Command Length Limits: EXIF Comment fields typically support up to 64KB, but practical limits are lower due to parser constraints.
- Tool Dependency: Execution requires
exiftooland shell access—unavailable in restricted environments. - Detection Surface: Modern EDR/XDR solutions monitor for
evalusage and anomalous child processes. - Integrity Checks: File integrity monitoring (FIM) systems detect metadata changes.
However, the method remains relevant for:
- CTF Challenges: Common in steganography and forensics competitions.
- Penetration Testing: Simulating covert command delivery in authorised engagements.
- Educational Demonstrations: Illustrating metadata risks in secure coding workshops.
⚠️ This is for educational purposes only. Do not use these techniques without explicit permission. Unauthorised use may violate laws and ethical guidelines. Stay curious, stay responsible. 🛡️📚
Conclusion
This small article probably does not have any real-life applications, but can show you how to make some nice tricks to have fun and impress your geeky friends! :)