Hey hardworking people 👋 Welcome back to my Finding Bugs Without Tools series. Today, we're diving into a logic flaw in the order processing flow that essentially gives out free credit (money), leading to unlimited financial loss for an e-commerce platform.
The Spark 🔍
It all started with a simple observation. I was testing an application's order workflow, specifically the Cash on Delivery (COD) option. The platform had a campaign for new user.
Get ₹30–50 credit on every order!
My hacker-sense started tingling. The promotion was clear, but the conditions were not. What happens to that ₹50 if the order never completes? What if it's cancelled?
This is the core of testing without tools: always ask, "What happens next?" and "What if I change the expected flow?"
Let's Talk About Website
So, our target is an e-commerce website that's really popular in India especially among girls💅. The site gives you ₹30–50 free credit when you place an order. These promo amounts are called credit on the site, and you can use that credit to buy stuff later.
In practice, the flow is simple: place an order, the site immediately adds promo credit to your account, and you can use that credit toward future purchases.but because of a logic flaw I found, those small promo credits can be stacked into free orders. In short: place, cancel, repeat — and the site keeps the credit. I didn't need any tools to find it.
The flaw I found was a broken handshake between the order placement and order fulfillment systems.
- Step 1 (Place Order): The system's logic was: "Order Placed" → "Grant Credit."
- Step 2 (Cancel Order): The system's logic was: "Order Cancelled" → "Update Inventory, Send Email." But it failed to execute the crucial step: "Revoke Credit.
Step-by-Step: Exploiting the Logic Flaw
- Log in to your account..
- Add any item to the cart the cheapest item available was perfect for testing.
- Place an order for any item using Cash on Delivery (COD) or another eligible payment method.
- Immediately after the "Order Successful" message, the account's wallet balance increased by the promotional amount (e.g., ₹40).
- Immediately cancel the order. The order moved to a "Cancelled" status.
- Check the wallet balance. The 40 was still there. The revocation logic was missing.
- Repeat steps 2–5. Each cycle adds more credit. Rinse and repeat.
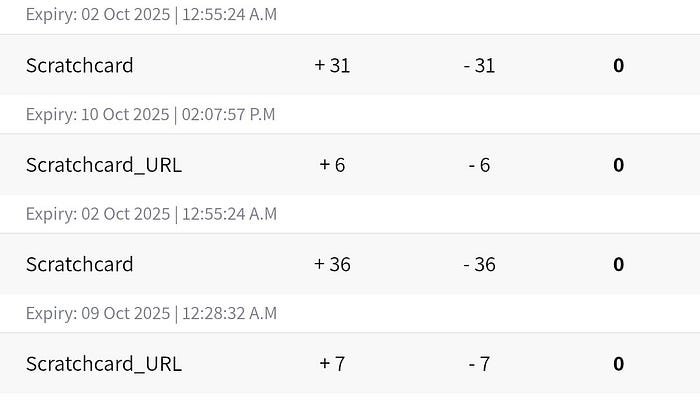
Short note: This was marked as a duplicate. Anyway, no big deal moving on.
The Impact: More Than Just a Bug
- Direct financial loss: Attackers can convert wallet credit into real purchases, draining inventory and revenue.
- Low Barrier to Abuse: This exploit required zero technical skill. Anyone who discovered it could exploit it, and it could easily be turned into a "life hack" tutorial on social media, leading to widespread abuse
Final Thought
It's wild how something so simple just placing and cancelling orders can turn into unlimited free shopping. No scripts, no hacks, just basic curiosity and a bit of "wait… what if I do this again?"
Bugs like these remind us that even big platforms can miss the small details. And sometimes, those small details cost the most.
👀 Stay tuned for more "No-Tool Bug Bounty" write-ups! Got questions? Email me: strangerwhite9@gmail.com or reach out on Twitter: @StrangeRwhite9
by StrangeRwhite | Series: Finding Bugs Without Tools

