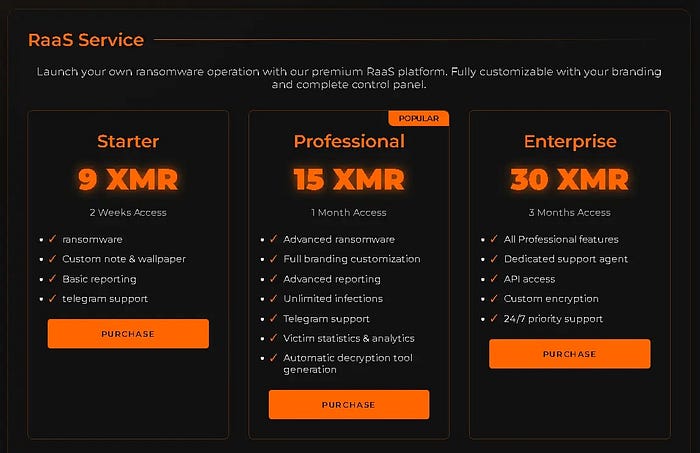
The ransomware economy is no longer the dark art of elite hackers. Today, it runs like a business — a ruthless underground marketplace where code is licensed, affiliates are recruited and profits are split. This model is called Ransomware-as-a-Service (RaaS) and it's changing the way cybercrime spreads.
Into this world arrives BQTlock, a new player that's making noise for all the wrong reasons. It's not just another strain of malicious code, it's a service built to empower affiliates, multiply attacks and put pressure on victims with both encryption and data leaks.
What makes BQTlock stand out is its combination of technical precision and organized infrastructure. From its ZIP-based payloads and persistence tricks to its use of Discord webhooks for exfiltration and Monero for ransom payments, it has all the hallmarks of a modern RaaS operation.

What Is BQTLOCK?
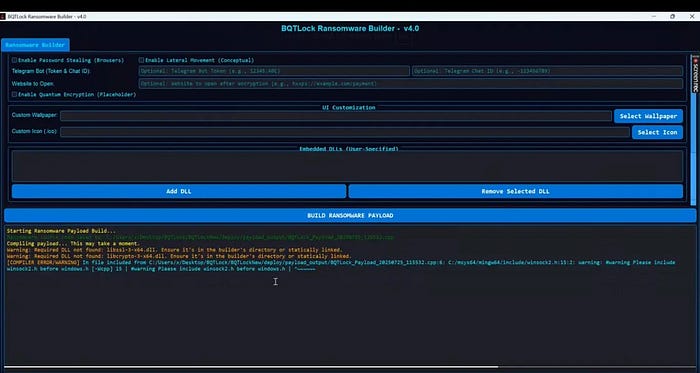
BQTLOCK is structured as a Ransomware-as-a-Service, offering a subscription model to affiliates. Operators provide the ransomware payload, while affiliates handle distribution and victim targeting. In return, affiliates receive a percentage of ransom payments and operators profit through the revenue split.
Its features suggest careful design aimed at persistence, stealth and pressure tactics — a classic mix in modern double-extortion ransomware.
How BQTlock Attacks
-> Initial Infection Vector
According to analysis, BQTLOCK arrives packaged in a ZIP archive containing:
- A primary executable:
Update.exe - Several DLL files to support malicious operations
Once executed, the malware initiates its infection chain and begins altering the system environment.
-> Persistence and Privilege Escalation
BQTLOCK does not simply execute and encrypt. It strategically establishes persistence:
- Scheduled Task Creation: A task named
Microsoft\Windows\Maintenance\SystemHealthCheckis added, masquerading as a legitimate Windows function. This ensures the malware runs even after reboot. - New Admin Account: It creates a local administrator account named
BQTLockAdmin, with the default passwordPassword123!. This grants attackers backdoor access to the system. - Privilege Abuse: It leverages SeDebugPrivilege to manipulate system processes and uses UAC bypasses to escalate privileges.
-> Evasion and Anti-Analysis Capabilities
BQTLOCK incorporates techniques to avoid detection and complicate analysis:
- Debugger Checks: Uses
IsDebuggerPresent()to detect if it is running under analysis. - Virtual Machine Checks: Identifies virtualized environments to evade sandbox detection.
- Process Hollowing: Injects itself into
explorer.exe, allowing execution within a trusted system process. - Obfuscation: Employs string obfuscation to hinder reverse engineering.
-> Data Theft and Exfiltration
Beyond encryption, BQTLOCK conducts credential harvesting from popular browsers, including:
- Google Chrome
- Mozilla Firefox
- Microsoft Edge
- Opera
- Brave
Harvested data is exfiltrated via Discord webhooks and potentially other messaging platforms. This enables double extortion: demanding payment both for decrypting files and preventing data leaks.
-> Encryption Mechanism
BQTLOCK employs a hybrid encryption scheme:
- AES-256: Used for encrypting victim files.
- RSA-4096: Secures the AES keys, making decryption impossible without the attacker's private key.
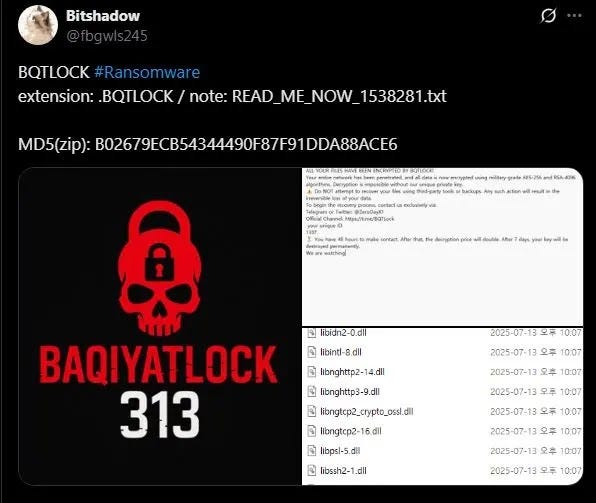
Encrypted files receive the extension: .bqtlock.
-> Ransom Demand and Payment
The ransom note delivered by BQTLOCK communicates a tiered payment structure:
- Demands between 13 and 40 Monero (XMR)
- Ransom doubles if unpaid within 48 hours
- Files threatened with permanent deletion after 7 days
Monero is specifically chosen for payments due to its privacy features, which make tracing transactions extremely difficult.
Command-and-Control Infrastructure
-> Darknet Portal
Victims are directed to a Tor-based portal (.onion address) for communication, payment and data leak negotiations.
-> Social Channels
BQTLOCK actively promotes itself across:
- X (formerly Twitter):
x.com/Zerodayx1 - Telegram Channels:
t.me/BQTlock,t.me/Fuch0u,t.me/BQTnet,t.me/BQTlock_raas
These are used for both victim communication and affiliate recruitment.
-> Contact Information
For direct correspondence, BQTLOCK lists the email address: BQTlock@tutamail.com.
-> Cryptocurrency Wallet
Reports have linked BQTLOCK to a Monero wallet used for ransom payments:
89RQN2EUmiX6vL7nTv3viqUAgbDpN4ab329zPCEgbceQJuS233uye4eXtYk3MXAtVoKNMmzgVrxXphLZbJPtearY7QVuAprIndicator of Compromise (IoCs)
-> File Hashes
Two malicious files have been linked to this ransomware:
4E7434AC13001FE55474573AA5E9379D7170292337A894CE9A58F5B2176DFEFC
-> Ransomware Website
The ransomware operators host a site on the Tor network:
hxxp://yywhylvqeqynzik6ibocb53o2nat7lmzn5ynjpar3stndzcgmy6dkgid.onion
-> Malicious URLs
A known exploit-related URL used by the threat actors:
hxxps://x.com/Zerodayx1
-> Telegram Channels Used for Distribution/Communication
hxxps://t.me/BQTlockhxxps://t.me/Fuch0uhxxps://t.me/BQTnethxxps://t.me/BQTlock_raas
-> Cryptocurrency Wallet
Payments are directed to the following wallet:
89RQN2EUmiX6vL7nTv3viqUAgbDpN4ab329zPCEgbceQJuS233uye4eXtYk3MXAtVoKNMmzgVrxXphLZbJPtearY7QVuApr
-> Contact Email
BQTlock@tutamail.com
Defense
Defending against ransomware like BQTlock requires a multi-layered strategy:
- Block IoCs: Update firewalls, proxies and EDR solutions with the known indicators.
- Patch and Harden: Secure RDP, enforce MFA and keep software updated.
- Backups: Maintain offline and immutable backups — and test them regularly.
- Network Segmentation: Limit lateral movement opportunities.
- User Awareness: Train employees to recognize phishing lures and suspicious files.
Conclusion
BQTLOCK is still a new entrant in the ransomware marketplace, but its design demonstrates how far RaaS platforms have matured. From stealthy persistence to aggressive extortion, it encapsulates the evolving tactics of modern cybercrime.
While no single control guarantees protection, vigilance, layered defenses and tested incident response plans significantly reduce the impact of such threats.
Stay One Step Ahead of Cybercriminals!
🔹 The best defense is staying informed and proactive!
🔹 Follow me for more insights on the latest cyber threats, attack trends and security best practices.
🔗 Let's connect and fortify our digital world together!
