Hey everyone — winteri3coming here (aka Djalel). I'm gonna start posting some writeups about bugs I found that were fun, weird, or actually worth reporting. I'll keep things simple, honest, and a bit messy — like how I talk. Hope you enjoy the reads. Stick around, there's some good stuff coming.
So I was doing what I normally do, scraping random URLs from public sources (VirusTotal, URL archives, etc.) just to see what kind of weird stuff is out there for my target. Usually it's boring. But then I run into these paths that look like chat sessions from an AI platform. Something like:
https://target.ai/p/a/5J9q9mWdke5rYj3Rcmo
https://target.ai/p/i/a/sqU0rYfa9NexrXTSgUyQ
https://target.ai/p/a/ku5dGq32w29aS4JkUMRdThese URLs having some random looking IDs at the end. Normally, you'd expect these to be protected, to require login or some magic header. But nope. I just dropped the URL into the browser… and bingo. Full conversation. Prompts, replies, everything. It was not my conversation. Not anyone I know. Just exposed chats.
These IDs are random, so you can't really guess them manually. But the issue isn't about guessing. The issue is: once the link leaks anywhere — logs, analytics, public archives — it becomes a permanent backdoor into private conversations.
I quickly crafted a simple report, nothing complicated. I dropped some random URLs in the address bar and ended up seeing full conversations from other users. No auth, no token, just the link, which is what i included in the report.
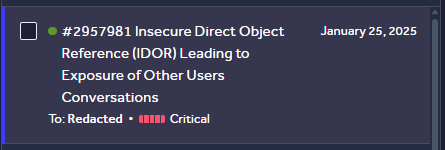
It took about 10 days before the report got triaged, so during that time I kept digging to understand what was really happening behind the scenes. While inspecting the network requests, I noticed a POST call hitting an API endpoint. In the request body, there was this id parameter, and guess what? It matched the same random-looking identifiers I saw in the URLs. So that basically confirmed the whole thing: the chat ID is directly used as the object reference, with no authorization around it. Classic IDOR.
So honestly, I got a bit lucky spotting this — but it wasn't pure luck. If I wasn't constantly monitoring those online indexing sources, this would've slipped right past me. That's the whole point: these things don't always show up on the target itself… they leak around it. Staying plugged into these sources is half the game in bug bounty.
Time To Triage: 10 Days
Time To Bounty: 22 Days
Bounty Amount: 3000$
Bug Type: IDOR

That's it for this one. Hope you enjoyed the ride. I've got more findings lined up, so stick around — see you in the next report. winteri3coming out.