الحمد لله والصلاة والسلام على رسول الله وعلى آله وصحبه أما بعد
Hello Hacker
I'm Mohamed also known as Mado, a dedicated security researcher and bug hunter
NOTE: The target is an external application with a disclosure program, but since I haven't received official permission yet, I'm using
target.comas a placeholder in this write-up
Target Overview
The target platform provides a team workspace where members can collaborate by creating and managing tasks. In addition, the platform offers a built-in team chat feature that allows users to communicate directly within the workspace
The Discovery
During my testing I focused on the chat functionality specifically the file upload feature since it allows users to share images and documents with other team members
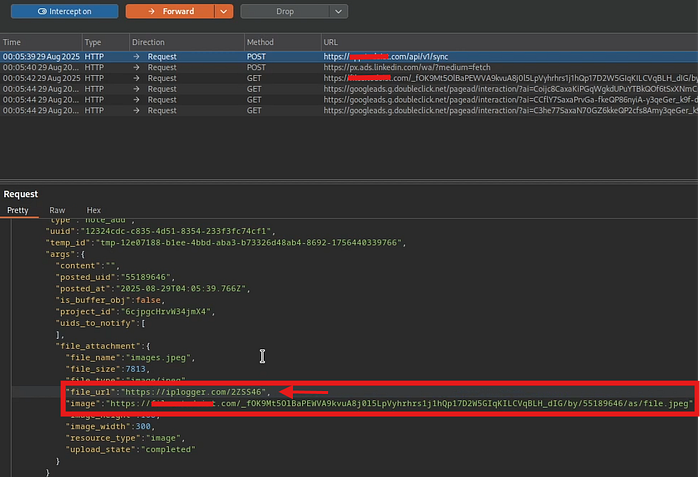
While uploading an image I noticed that the request included a parameter called file_url This parameter pointed to the location of the uploaded image. Naturally I wondered: what if I change this value to an external domain under my control

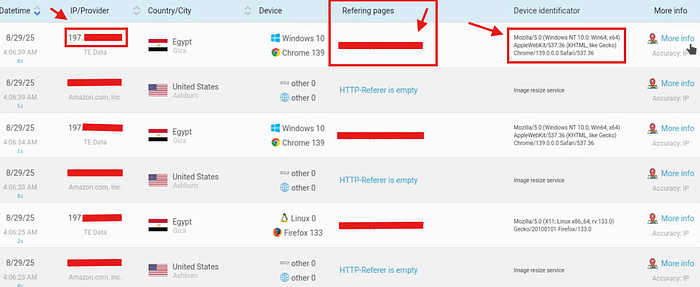
I first tried replacing the URL with one of my own collaboration servers But it didn't receive any requests To confirm the Bug I then used an IP-Logger which successfully captured
I also checked the server response to confirm whether the request returned a 200 OK or a 400 Bad Request
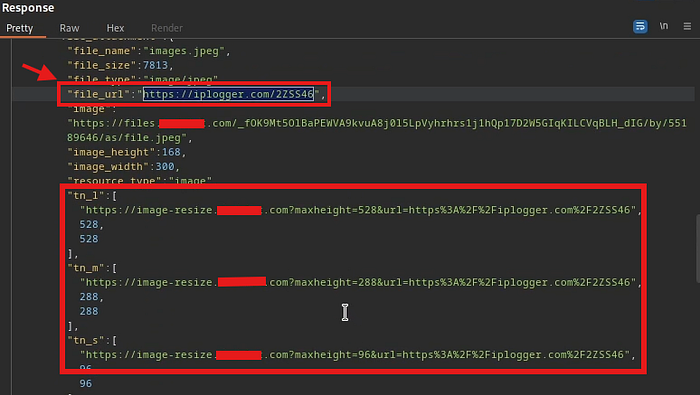
After forwarding the request, the result was that the image showed an error when the chat was opened
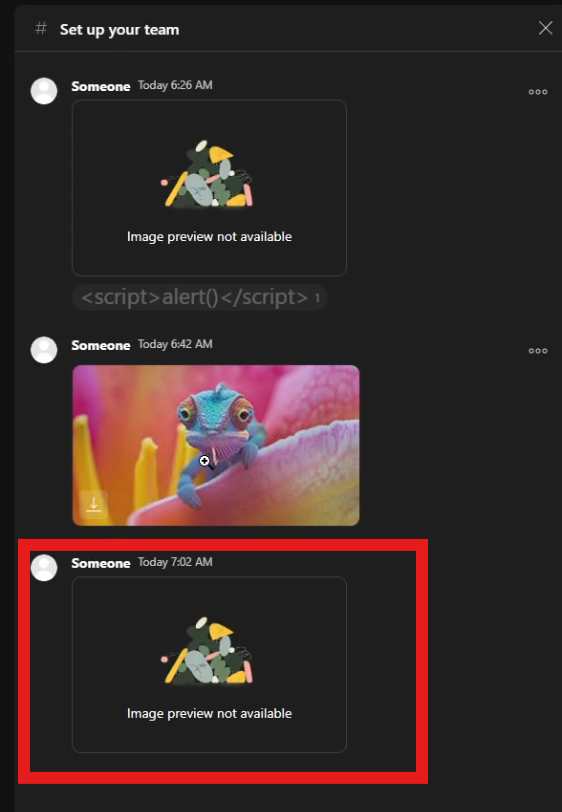
Then I switched to the victim account opened the chat and went back to The IP logger Then BOOM
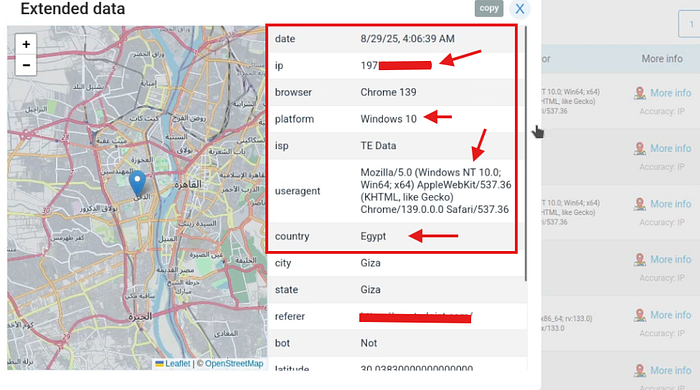
I clicked on "More Info" to see more details about the victim
MindSet:

Impact:
Black Hat Hackers can get critical information about all The Target users in Team The information obtained is very important for the privacy of the users and includes information such as IP address, OS version , city …
The Result:
In the end I was able to prove that simply by uploading a modified JPEG in the team chat it was possible to trigger requests to an external server As a result I successfully collected sensitive information from other team members including their (IP address, time zone, operating system version country and browser details (User-Agent) all without any user interaction)
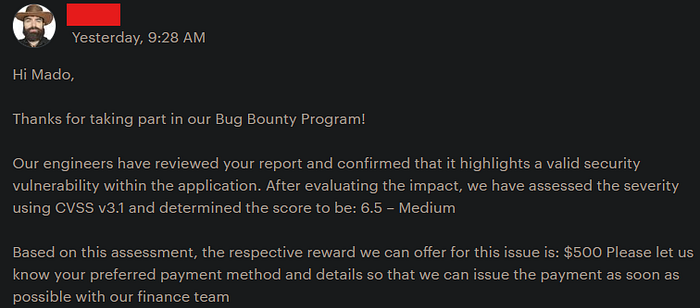
Severity is : Medium To High
If You Want To Reach Me All My Contact Info is Here: Click Here
……………Thank You For Reading And I hope This Was helpful………………

