When most people think of cyber security, they think of antivirus software, strong passwords or firewalls. However, the biggest vulnerability is often not in the software, but in the human being. When an employee clicks on a link they don't recognize or enters their passwords on a fake website, million-dollar security systems can be neutralized in an instant.
In this article, we will talk about SEToolkit (Social-Engineer Toolkit), one of the most popular tools developed to test human vulnerabilities and simulate social engineering attacks. Our goal is to show how we can use this tool not for malicious purposes, but for awareness and education.
What is Social Engineering?
Social engineering is an attack method that targets human psychology, not technical vulnerabilities. The attacker gains the target's trust and convinces them to leak information, click on malicious links or share confidential data. These attacks often don't even require technical knowledge — just a good story and some persuasion.
The most common social engineering attacks:
Phishing: Stealing information from the user via a fake email or web page
Vishing (Voice Fraud): Getting information by pretending to be a bank official on the phone
Tailgating: Unauthorized persons infiltrating the premises with an employee
These types of attacks always pose a threat, no matter how good the cyber security measures are.
What is SEToolkit? SEToolkit (Social-Engineer Toolkit) is an open source tool used to simulate social engineering attacks. Developed by Dave Kennedy (TrustedSec), it is Python-based and comes pre-installed or can be easily installed, especially on penetration testing platforms such as Kali Linux.
This tool allows security professionals performing penetration testing or trainers providing training to test user awareness. With SEToolkit, you can create fake websites, orchestrate email phishing scenarios, design QR code redirection attacks, or create a USB autorun exploit.
The most important feature: You can do all this easily with a menu-based interface. Scenarios can be created with step-by-step instructions without the need for in-depth technical knowledge.
Install and run SEToolkit!
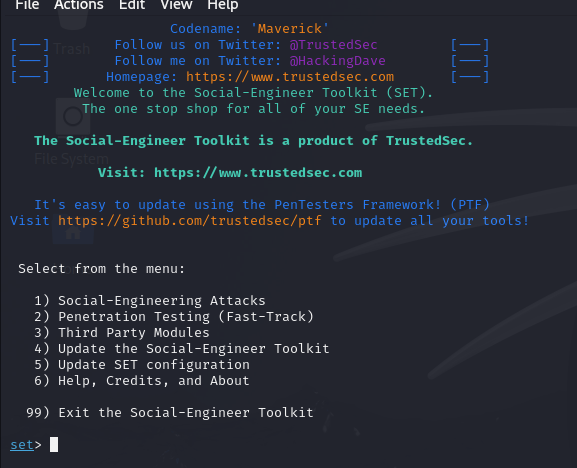
When we go in Social-Engineering Attacks we saw this:
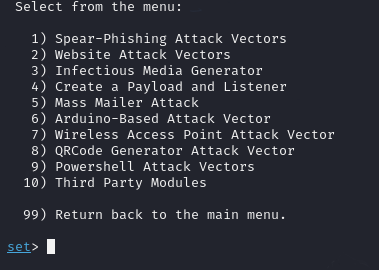
Here you can see that we have a lot of options, from QR code attacks to fake websites.
Lets type 2 and enter.
After we saw that we type 3.
now, just press enter.
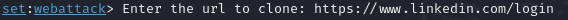
Now type the ip address on browser and a cloned login page will appear.

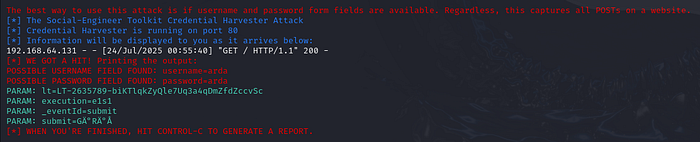
and when we enter the username and password, the person's username and password appear on our screen.
Key Features and Use Cases
SEToolkit is menu-based, allowing the user to easily experiment with different social engineering scenarios. Below you can find some of the most important modules in SET and what they do: 1. Social-Engineering Attacks Simulates real-world social engineering attacks. It includes methods such as phishing, USB attacks, email traps. Website Attack Vectors: Creates an exact copy of a real website. It is used to collect critical data such as username and password through the fake page. 3. Credential Harvester: Displays the information entered by the target on the terminal. Usually used in conjunction with cloned fake login screens. 4. Metasploit Integration: For those who want to perform advanced attacks, SET can integrate with the Metasploit Framework. For example, it can create malicious payloads. 5. QRCode Generator: Phishing or malicious site redirects can be done via QR code. It is a creative tool for physical social engineering.
Ethical and Legal Boundaries
Tools like SEToolkit are useful simulation tools for ethical hackers and cybersecurity professionals. However, they can have serious consequences when misused: Unauthorized use against individuals, companies or networks is a crime. Use outside your own machine or an isolated test environment (e.g. VirtualBox virtual machine) is strictly prohibited. In corporate companies, such tools can only be used for authorized cyber security testing (Pentest) and awareness training.
Remember: Testing security is one thing, hacking into someone else's system is quite another. The one who crosses the line becomes a criminal, not a hacker.
Conclusion and Recommendations
SEToolkit is a powerful tool that shows how effective and widespread social engineering attacks can be. Anyone with moderate technical knowledge can easily create simulations with this tool.
It can be used as an effective "wake-up call" in corporate awareness trainings.
Security teams can use SET to measure how users react to such attacks.
Individual users can learn from SET to better recognize real-life threats.

