Hello F.R.I.E.N.D.S, My name is Suprit (Hacker name- s3ctat0r) & I'm a bug bounty hunter & enthusiast learner.
I choose a large scope program to hunt on, selecting a program & sticking to it is very difficult part rather than hunting for vulnerabilities. So, I decided to stick to the selected program and start hunt for bugs!!

I performed all my Reconnaissance stuff and started focusing for sensitive information leakage via directory listing vulnerability.
About Directory listing?
Directory listing vulnerability, in simple terms, refers to a security weakness in a web server or file hosting system that allows unauthorized users to view the contents of directories (folders) on a website or server.
Normally, when you visit a website or access files on a server, the server is configured to display only the specific files that you request. However, in cases where the server is not properly configured or secured, it may mistakenly allow anyone to see a list of all the files and directories present in a particular folder.
This directory listing vulnerability can be problematic because it reveals sensitive information that is not intended for public access. It can expose important files, confidential data, or even reveal the structure and organization of a website's directories, which could aid attackers in planning further attacks or unauthorized access.
For example, if a website has a directory listing vulnerability, and an attacker knows or guesses the name of a sensitive file, they can easily navigate to the directory and view the file's contents without proper authorization. This could lead to the exposure of private information or give the attacker insights into system vulnerabilities that can be exploited.
To mitigate this vulnerability, website owners and system administrators should ensure that their servers are properly configured to disable directory listing and only allow access to authorized files and directories.
Fuzzing comes in the picture!
Fuzzing directories, in simple terms, refers to a technique used in cybersecurity to discover hidden or sensitive files and directories on a website or web application.
Imagine a website as a big house with many rooms. Some rooms are easily accessible and visible to everyone, while others may be hidden or locked. Fuzzing directories is like systematically trying to find and access those hidden or locked rooms.
To perform fuzzing directories, security professionals use specialized tools that automatically generate and test different combinations of URLs or directory names. These tools systematically send requests to the web server, trying out various combinations in an attempt to discover hidden or restricted directories.
The goal of fuzzing directories is to uncover files or directories that were not intended to be publicly accessible. This could include sensitive information such as login pages, configuration files, backup files, or even directories with unrestricted access that could potentially be exploited by attackers.
By identifying and securing these hidden or vulnerable directories, website owners can better protect their systems and sensitive information from unauthorized access or potential security breaches.
Choosing your wordlist wisely
There are many wordlists available and as well as security researchers can also create your own wordlist by using permutation of keywords or directories recursively.
Generally, I prefer raft wordlist by SecList, because it has amazing words in few different lists and start Brute forcing over the web URL.
What's next ?
Tooling with Dirbuster, Dirsearch, ffuf, etc are my personal preferred one's and are absolutely amazing!!
Start Brute force aka Fuzzing attack and observe the response from the web server to get directory listing type of vulnerabilities.
Impact
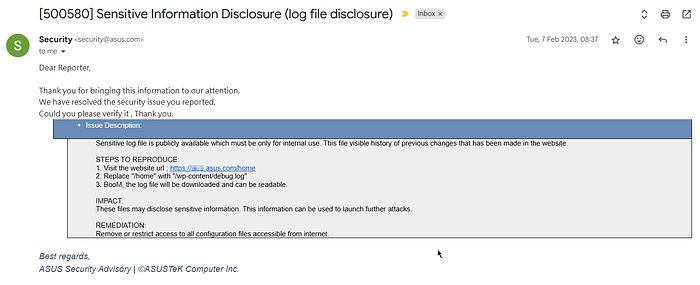
It was observed that SQL Database credentials were leaked along with the DB IP address in the exposed log file.
I've discovered 3 directory listing vulnerabilities which leaked sensitive information!!
ASUS Hall of Fame — ASUS Product Security Advisory | ASUS Global

