Task 1 — What Are Vulnerabilities
Question 1: What is the process of fixing the vulnerabilities called?
- Patching
Task 2 — Vulnerability Scanning
Question 1: Which type of vulnerability scans require the credentials of the target host?
The authenticated scanning purpose is to identify which vulnerabilities could exploit if an attacker were to have access to the host.
- Authenticated scanning
Question 2: Which type of vulnerability scan focuses on identifying the vulnerabilities that can be exploited from outside the network?
When dealing with differentiating scans, for inside the network, think internal, and for outside, think external.
- External
Examples of external scans are:
- Public websites
- Network perimeter (searching for open ports)
- Outdated software
- Unsecured APIs
- Misconfigurations
Task 3 — Tools for Vulnerability Scanning
Question 1: Is Nessus currently an open-source vulnerability scanner? (Yea/Nay)
- Nay (says the horsey 🐴 )
Question 2: Which company developed the Nexpose vulnerability scanner?
- Rapid7
Question 3: What is the name of the open-source vulnerability scanner developed by Greenbone Security?
- OpenVAS
Task 4 — CVE & CVSS
Question 1: CVE stands for?
- Common Vulnerabilities and Exposures
Question 2: Which organization developed CVE?
- MITRE Corporation
Question 3: What would be the severity level of the vulnerability with a score of 5.3?
- Medium
Tas 5 — OpenVAS
Question 1: What is the IP address of the machine scanned in this task?
You'll have to reference task photos for this one.
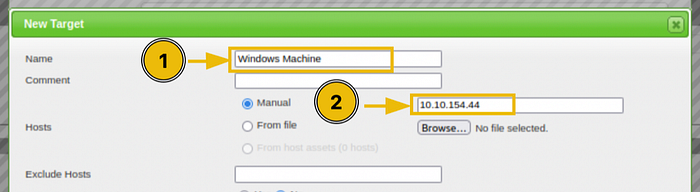
- 10.10.154.44
Question 2: How many vulnerabilities were discovered on this host?
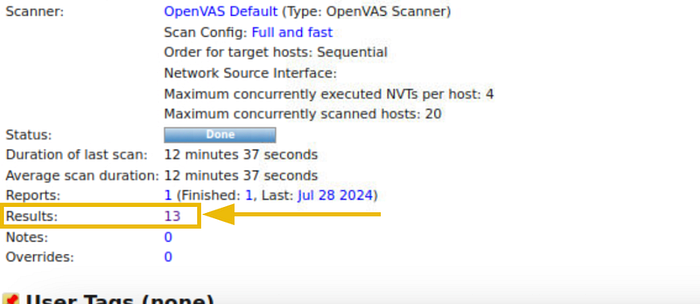
- 13
Task 6 — Practical Exercise
Scenario: A reputable firm conducted a vulnerability scan on a server (MACHINE_IP) on its network that stores critical information. This activity was intended to enhance the organization's security posture. The security team conducted the activity using the OpenVAS vulnerability scanner, and the vulnerability scan report was placed on the desktop. You are an information security engineer working for that firm. You are tasked with reviewing this report. You can simply open the report placed on the desktop or perform the vulnerability scan again to answer the questions below. OpenVAS is pre-installed on the host to which you are given access.

Question 1: What is the score of the single high-severity vulnerability found in the scan?
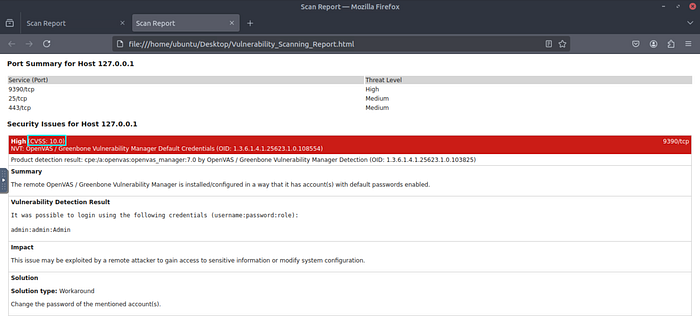
- 10
Question 2: What is the solution suggested by OpenVAS for this vulnerability?
- Change the password of the mentioned account(s).
One day, I'll make a vulnerability scanner called OpenVato for all my vatos out there pursuing education in cybersecurity.

