Introduction
In the busy world of cybersecurity, browser vulnerabilities often fly under-the-radar compared to server or network bugs , but they're among the most dangerous because they sit at the interface between users and the web. That's exactly what we're looking at with CVE-2025–10585, a type-confusion flaw in the V8 JavaScript and WebAssembly engine of Google Chrome (and by extension, many Chromium-based browsers). According to vendor advisories, this bug is actively exploited in the wild.
With Chrome commanding a large share of the desktop browser market globally, the exposure is immense. The attack surface is huge: simply visiting a malicious or compromised webpage may trigger exploitation.
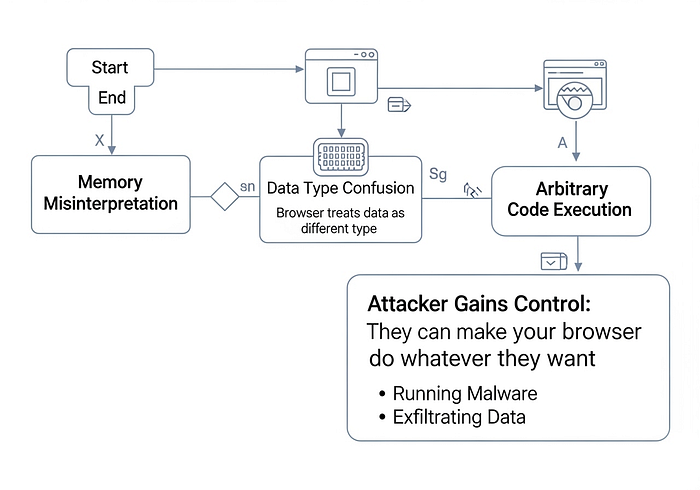
This isn't a theoretically possible bug waiting for someone to craft a proof-of-concept; this is "we know people are abusing it. That elevates it from academic interest to urgent business and security operations risk. Moreover, because it's a type-confusion issue inside the V8 engine, it's not just about crashing a tab , arbitrary code execution becomes feasible, meaning the attacker can potentially break out of what the browser sandbox promises and pivot into more substantial compromise.
In short: if you have Chrome (or a Chromium-based browser) in your environment, this is a bug you have to act on now, not later.
Impact
Let's talk impact in practical terms.
First, any user with a vulnerable version of Chrome (pre-140.0.7339.185/.186 for Windows/Mac, or pre-140.0.7339.185 for Linux) can be targeted simply by visiting a malicious webpage.
What this means for organizations: endpoints (desktops, laptops) become weak links. A compromised browser session might lead to credential theft, session hijack, persistence via browser exploits, or full system compromise if the sandbox is bypassed. Because the bug lives in the JavaScript/WebAssembly engine (V8), it affects a fundamental component of how web content is handled.
Type confusion vulnerabilities typically exploit memory mis-interpretation: the program treats a chunk of memory as one object type when it's actually another, leading to heap corruption, unintended behavior, and ultimately arbitrary code execution. From a business perspective, this means the potential for commodity malware delivery, zero-click user exploitation via drive-by, lateral movement inside networks, and perhaps even access to privileged data if the compromised endpoint has elevated access.
Given that Chrome is everywhere , in organisations, in homes, on contractor machines , the blast radius is high. Also key: because it's already being exploited, the window of opportunity for defenders is closing. Vendors often withhold full technical details until patches are widely deployed , which means attackers have a head-start.
The fact that the vulnerability is listed in the Cybersecurity & Infrastructure Security Agency (CISA) Known Exploited Vulnerabilities catalog further underscores its severity: according to NVD data, the bug has a CVSS 3.x base score of 9.8 (AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H) , meaning network-accessible, no privileges required, user interaction minimal or none.
Exploitation
So how are attackers exploiting this? While Google and other sources do not publish full proof-of-concepts or detailed chain logic (in part to protect defenders and limit additional exploitation), what we do know is enough to sketch the attack chain and derive defensive posture.
The bug is a type-confusion in V8: that means a crafted HTML page (or embedded JavaScript/WebAssembly module) can trigger memory corruption.
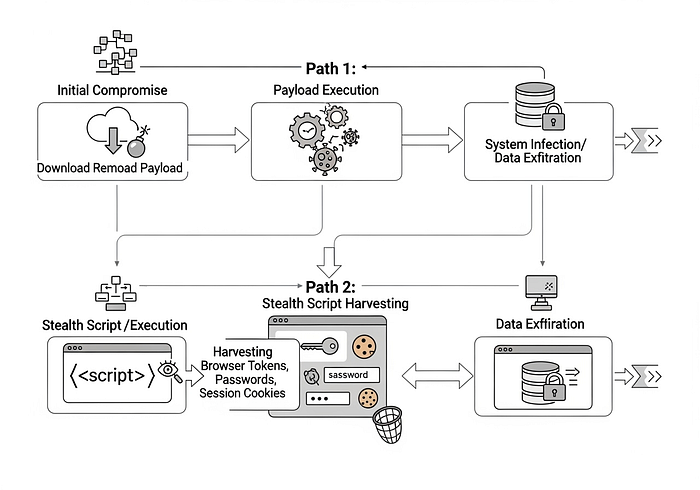
The attacker's likely path: host a malicious webpage (or compromise a legitimate one, or embed the malicious JS in an ad-network), lure or redirect a user's browser to that page, the V8 engine mis-handles object types, heap corruption ensues, the exploit triggers arbitrary code execution, the attacker escapes the browser sandbox or drops a payload, then proceeds to persistence, data exfiltration or further latenral movement.
Because this is drive-by capable (i.e., minimal user interaction beyond visiting a site), it can implicate remote users, contractors, and even unmanaged endpoints. The fact that Chrome's Threat Analysis Group (TAG) flagged this bug and Google acknowledged in its advisory that "an exploit for CVE-2025–10585 exists in the wild" confirms attackers are already using this in real-world attacks.
Also the release notes show that this is the sixth exploited Chrome zero-day this year , meaning attackers and researchers alike know this vector is fertile ground.
From a practical perspective for defenders: you cannot assume "this is just a browser bug" with low priority. It's a potential entry vector into your network , especially if users browse to untrusted or compromised domains, or if the organization uses browser-based applications with insufficient segmentation.
Mitigation
Here's where your rubber meets the road: what must you do right now to reduce risk. First and foremost, ensure that all instances of Chrome in your environment (and ideally all Chromium-based browsers) are updated to the patched version.
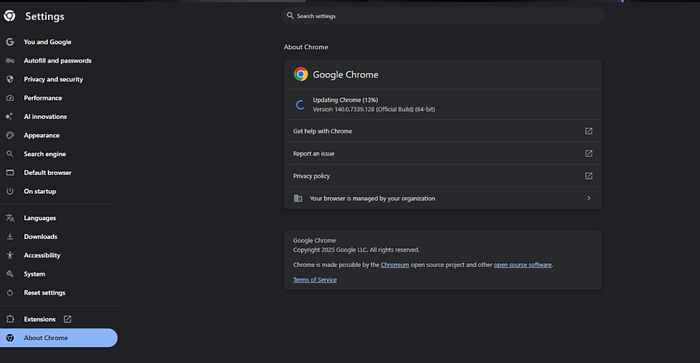
According to Google's advisory and multiple vendor posts, the fixed versions are: 140.0.7339.185/.186 for Windows/Mac and 140.0.7339.185 for Linux. If you have auto-updates enabled and verify periodically, you're likely covered , but don't assume: many enterprises disable auto-update, have lag, or manage via image builds. Next, track all Chromium-based browsers (Edge, Brave, Opera, Vivaldi, etc.) because the same underlying V8 engine may be shared or similar; until they publish patches you're still exposed.
Beyond patching, apply compensating controls: block or restrict access to high-risk or untrusted domains via web gateway / firewall / DNS filtering; use browser isolation for risky web browsing; enforce least privilege, disable or restrict browser extensions, and ensure endpoint detection & response (EDR) monitors for anomalous child process creation by browsers or sudden spawning of system-level commands from browser context.
Monitor logs for abnormal browser crashes, tab terminations, or memory corruption events. From a network viewpoint, isolate unmanaged/guest browsing devices on separate VLANs or via zero-trust segmentation so that a compromised browser does not lead directly to high-value systems.
Finally, train users: while this bug is drive-by capable, reducing clickbait, phishing links, and encouraging caution with unknown sites is always part of the defence posture. In organizations subject to regulatory or government compliance (e.g., US federal agencies), note that CISA's BOD 22–01 requires remediation of this vulnerability by October 14, 2025.
They condemn media sensationalism but thrive on it. They claim to be educators, but the lesson is rarely about cybersecurity. It's about mastering the art of manipulation.
They will produce a 20-minute on CORPORATE HYPOCRISY, while their own channels and affiliate links are riddled with more trackers, Discord links and overpriced courses than a bloodhound convention.
They'll warn you about state-sponsored surveillance and then promote a VPN with a sketchy privacy policy because their affiliate payout is the highest in the industry.
IOCs & Detection Considerations
Although full exploit details have been withheld (for very good reason), you can still deploy hunting and detection logic leveraging known indicators of compromise (IOCs) and behavioural patterns. Here are some practical ones:
- Browser version audit: Identify all clients running Chrome < 140.0.7339.185/.186 (Windows/Mac) or < 140.0.7339.185 (Linux).
- Web gateway / proxy logs: Look for users connecting to URLs or domains recently flagged for browser exploit campaigns; unusual sites served from ad networks or redirect chains; repeated browser crashes on memory corruption (e.g., V8 engine crashes).
- Endpoint telemetry: Monitor for the browser process (chrome.exe / chromium) spawning unexpected child processes with SYSTEM or elevated privileges, or loading DLLs/components from unusual paths.
- Memory or sandbox escape indicators: If you see a browser process suddenly modifying other system processes, writing to file paths outside user space, or communicating outwards to C2 domains shortly after browsing sessions , these should be flagged.
- Browser extension / plugin anomalies: Unexpected installation of extensions shortly after a browser crash or after suspicious tab visits.
- Unmanaged endpoint detection: Guest or contractor machines with outdated browser versions can be measured via asset inventory tools; monitor for those and isolate or upgrade them immediately.
While these IOCs do not surface the exploit itself, they give defenders visibility into the exploitation chain and allow earlier response.
Final Thoughts
In the world of cybersecurity, ease of exploitation often equals focus. A bug like CVE-2025–10585 doesn't require a user to download an attachment or open a document , just browsing a compromised web page might be enough. That makes it exceptionally potent. Every organization should treat this as a top-tier patch priority: update your browsers, verify update status, widen compensation controls for browsers, and monitor your endpoints and gateways for any signs of browser exploitation. Because once attackers gain entry via the browser, they typically escalate quickly.
As the landscape of browser-engine bugs continues to expand (and this is already the sixth zero-day for Chrome this year), defenders must consider browsers not as benign utilities but as frontline attack surfaces. By tackling this vulnerability now, you reduce the window of opportunity for attackers and protect your endpoint hygiene in a domain often overlooked.

