Introduction
The modern world uses advanced software technology. Therefore, developers have more power than ever, and with it, more responsibilities. in 2021, attackers caused the Codecov software development error, and exposed a complex software development pipeline in a supply chain breach. For months, the breach, which compromised thousands of customer accounts and sensitive information, went unnoticed. These accounts belonged to large enterprises, and the breach involved the harvesting of credentials, authentication tokens, and sensitive information. What was truly horrifying about the event was the source; it was derived from a dev-side configuration misconfiguration. This highlighted the irresponsible development practices, which ultimately impacted the entire system.
This is where the need for software like "Aikido Security" comes in. Seeking to integrate security and software development, Aikido incorporates proactive offense and risk scanning to detect potential threats and places them right within the workflow. Instead of letting the security team function post-deployment of the software, Aikido allows developers to proactively find problematic areas and potential threats, which include misconfigured CI/CD pipelines, secrets that are leaked, and outdated software dependencies. Aikido prevents attackers from gaining access to the configuration. Aikido, in particular, embeds security deep within the "code in transit." This approach embeds portable software in such a way that it is self-protecting. Aikido demonstrates that
About Aikido
Aikido is a comprehensive, developer-first security platform designed to secure code, cloud environments, and runtime across the entire software development lifecycle (SDLC). It centralizes multiple security testing types, including static application security testing (SAST), software composition analysis (SCA), infrastructure as code (IaC) scanning, secret detection, dynamic application security testing (DAST), and API security into a single and centralized system, making security simpler and faster for development teams.
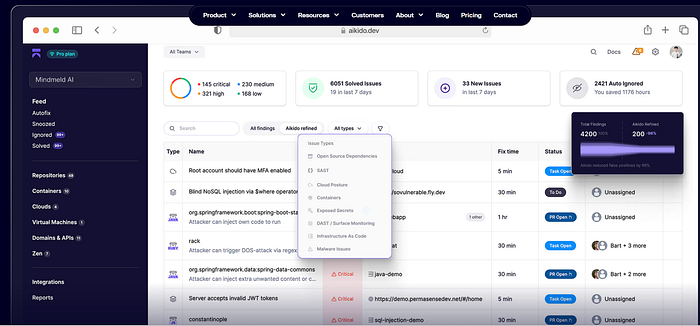
Key Features of Aikido Security Platform
- All-in-One Security Coverage: Aikido provides full security visibility from code to cloud, integrating security checks deeply into developer workflows, such as IDEs and CI/CD pipelines. It covers various security scans to identify vulnerabilities in source code, open-source dependencies, container images, infrastructure code, and runtime environments.
- Noise Reduction and AI-Driven Automation: The platform prominently reduces false positives, enabling developers and security teams to focus on genuine security issues. Its AI-based autotriage prioritizes vulnerabilities effectively, and an AI Autofix feature enables automatic single-click fixes of detected issues in code and infrastructure.
- Compliance and Governance: Aikido automates compliance management for standards like SOC 2 and ISO 27001 by generating Software Bill of Materials (SBOMs) and managing technical vulnerabilities. This supports organizations in meeting regulatory requirements without excessive manual work.
- Integrations and Developer Focus: With over 100 integrations, Aikido fits seamlessly into existing workflows and tools, connecting well with services like GitHub, Linear, Asana, Slack, and popular cloud providers. It is designed with developers in mind, making security accessible and efficient throughout development.
- SaaS Delivery and Pricing: Delivered as Software as a Service (SaaS) and deployed on AWS, Aikido offers scalable security with various pricing plans tailored to team size and usage. There is also a free developer plan to encourage adoption and experimentation.
Use Cases of Aikido Security Platform
- Application Security: Detect critical vulnerabilities in application source code early by integrating static application security testing (SAST) and dynamic application security testing (DAST) into the CI/CD pipeline, ensuring safer deployments.
- Supply Chain Security: Monitor and manage vulnerabilities in open-source dependencies with software composition analysis (SCA) plus malware detection to protect against supply chain attacks like Log4Shell.
- Cloud Security Posture Management: Scan Infrastructure as Code (e.g., Terraform, Kubernetes manifests) to prevent misconfigurations such as exposed storage or overly permissive cloud permissions, enforcing best practices and standards compliance.
- Secrets Detection: Automatically find and alert on accidentally committed secrets like API tokens and passwords in code repositories, preventing data breaches.
- Compliance Automation: Organizations can use Aikido to automatically generate compliance reports and maintain audit trails, simplifying adherence to standards like SOC 2 and ISO 27001.
- DevSecOps and Developer Enablement: With integrations into developer IDEs (e.g., Visual Studio Code) and CI/CD pipelines, Aikido enables a shift-left security approach where developers catch and fix security issues as part of their normal workflow, improving security culture and reducing remediation time.
- Vulnerability Management and Automation: Security and DevOps teams use Aikido to centralize visibility of vulnerabilities across code and infrastructure, prioritize remediation based on risk, and automate routine security tasks to increase operational efficiency.
How to Use Aikido Security Platform
- Connect Code Repositories and Cloud Environments: Aikido easily integrates with popular development tools like GitHub, GitLab, and cloud platforms to continuously scan code, dependencies, IaC (Infrastructure as Code) configurations, and container images for vulnerabilities.
- Automated Vulnerability Detection and Triage: The platform automatically scans for issues such as coding errors, exposed secrets, infrastructure misconfigurations, license risks, and malware in open-source dependencies. It uses AI-powered triage to prioritize relevant findings and minimize false alarms.
- Developer-Friendly Fixes and Automation: Developers receive clear security alerts and can use single-click auto-fix capabilities for many issues. This accelerates remediation by merging pull requests that automatically patch vulnerabilities.
- Compliance and Reporting: Aikido automates the generation of compliance documentation like SOC 2, ISO 27001, GDPR, and enables managing technical vulnerabilities to support regulatory requirements.
- Workflow Integration: Teams can follow up on security issues seamlessly via integrations with task management tools like Linear and Asana or communication tools like Slack, ensuring security tasks are tracked and resolved within their existing workflows.
Conclusion
In summary, Aikido comes with an all-inclusive platform outfitted with artificial intelligence that aids in and tackles various complimentary security functions, from application security and risk analysis, to cloud infrastructure compliance automation, and finally cloud infrastructure hardening and compliance automation, which enhances productivity for developers, system administrators, security teams, and any firm looking to develop and deploy sophisticated software in record time at a fraction of the cost.
Let me know about your experience in the comment section if you have ever tried the Aikido Security Platform before
Till I come your way again in the next 2 weeks, Tuesday, #BeCyberSmart 😊
Cyberliza writes TuesdayTool
