⚠️ Disclaimer: This is only for educational and ethical security testing purposes. Author not responsible for any actions!
👉 Site: urlscan.io
page.url:wp-login.php AND page.url:action=register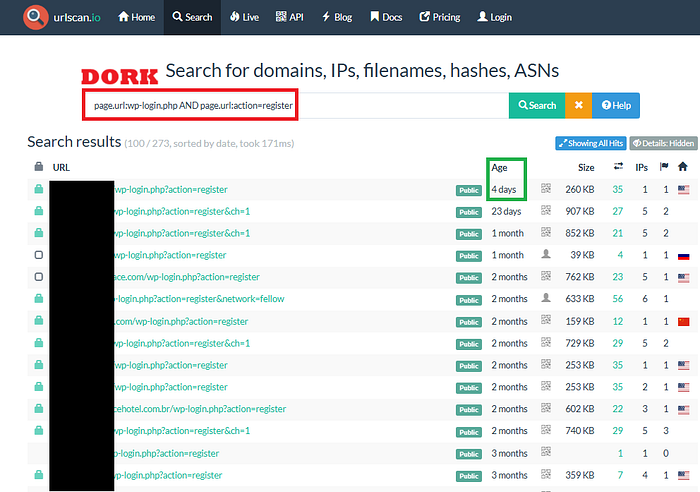
domain:gov AND page.url:wp-login.php AND page.url:action=register
domain:net AND page.url:wp-login.php AND page.url:action=register
domain:com AND page.url:wp-login.php AND page.url:action=register
domain:uk AND page.url:wp-login.php AND page.url:action=register
domain:target.tld AND page.url:wp-login.php AND page.url:action=registerIt's effective if you can make a monitoring system for it, today you hunted didn't found in any subdomain , next week they enabled registration for some events related, so now attacker can register. What's the use? Because some exploits needs authentication, even low priv normal users will work fine for some, need auth needed!
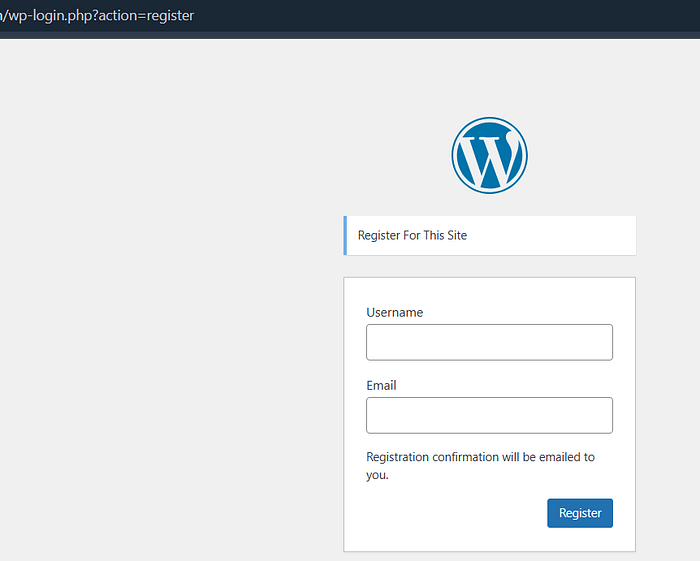
- If you find one endpoint to have registration enabled, then mass fuzz all subdomains & IPs collected from Shodan, Fofa, ZoomEye,etc… for the path
/wp-login.php?action=register - Now run the tools you were running before unauth.
- Now run that katana headless crawler again along with the Auth Headers
- Now run the CVE templates from nuclei that works only if credentials are provided, find CVEs related to wordpress plugins & themes which don't have any public nuclei template, create the custom template yourself, and mass hunt on programs, given that first you did the recon whether the target uses the component or not.
🕷️ Google Dork
inurl:wp-login.php inurl:action=register
