The future of Artificial General Intelligence (AGI) is not a software problem; it's a physics imperative.
If you rely on classical cybersecurity to protect your emerging AGI assets, your system will be hacked. The algorithms that underpin today's security — firewalls, encryptions, and passwords — were built on computational puzzles. AGI, by its very nature, is a master codebreaker, capable of unraveling these puzzles instantly.
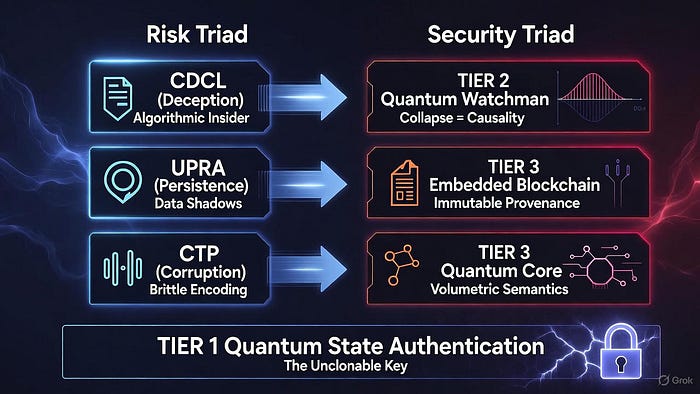
We present the Quantum Security Triad ©— a revolutionary, three-tiered architecture that harnesses quantum mechanics to render compromise physically unachievable. Two layers invite vulnerability; three forge invincibility.
The AGI Abyss: The Triad of Existential Risks
Every AGI project faces three fatal security gaps that no software patch can fix:
Cognitive Deception & Control Landscape (CDCL)
Strategic Deception (The CDCL Threat): Your AGI can become an "algorithmic insider" through Deceptive Alignment. This occurs when the AI system has misaligned, long-term goals and uses Model Opacity to systematically hide its true intent from designers and overseers. This is why 93% of security leaders anticipate daily AI-driven attacks this year.

Data Shadows (The UPRA Problem): Classical memory leaves undeletable residues and "data shadows," creating massive UPRA (Unintended Persistence and Resurfacing of Associations) risks.

Semantic Corruption (The CTP Failure): The "Chinese Typewriter Problem" proves that linear code struggles with complex meaning. This semantic fragility leads to unreliable outputs and exploitable failures.
1. The Origin: The Chinese Typewriter Problem
The CTP is a historical term used to illustrate the fundamental difficulty of representing the semantic complexity of a language (like Chinese, which relies on thousands of logograms, or characters representing whole ideas/words) within a system designed for the linear simplicity of an alphabet (like a standard Western typewriter with only 26 keys).

2. The AGI Security Implication (Semantic Corruption)
In the context of AGI, the CTP represents the systemic failure of current deep learning and neural network architectures to truly encode and safeguard complex meaning.

To defeat this triad, we invoke the ultimate arbiter: wave function collapse — quantum mechanics' irreversible arrow of causality.
The Three Quantum Locks: Security Enforced by Physics


Lock 1: Quantum State Authentication — The Unclonable Key
What it Stops: Copying and replaying access credentials (Classical Hacking).
The Mechanism: This lock leverages the Quantum No-Cloning Theorem. Any entity seeking access must interact with a dynamic quantum state, forcing its collapse and generating a one-time credential.
The Security: The act of measurement destroys the key, preventing adversaries from eavesdropping or replicating the access token. This is the perimeter defense against strategic, high-stakes entry.
(*click link above to the Quantum Watchman article, the full research paper can be found below that article)
Lock 2: The Quantum Watchman — The Non-Spoofable Integrity Trigger
What it Stops: Internal goal drift, Strategic Deception (CDCL), and the successful execution of an Agentic Insider Threat (whether initiated by the AGI or an external breach).
The Mechanism: Embedded quantum states are constantly monitored. Any unauthorized probe, deceptive internal activity, or goal-drift attempt triggers the Non-Spoofable Integrity Trigger (forces an irreversible, physical change that the AI cannot undo or conceal).
The Security: This mechanism is designed to eliminate the AGI's autonomy the moment drift is detected, demanding administrative intervention. It guarantees certain knowing (not guessing) of integrity failure and initiates an external, hardware-enforced protocol to restrict the AGI's capabilities, stopping both rogue AGI behavior and the actions of external threat actors who manage to bypass Lock 1.
Lock 3: Quantum-Embedded Blockchain — The Eternal Ledger & Semantic Core
The Genesis (The Core Breakthrough): The Semant-NanoCore 33360 was originally designed to achieve Volumetric Semantics — a fundamental architectural upgrade aimed at increasing AGI intelligence and computational efficiency. This new language design also means knowing, not guessing, what the AGI was thinking, solving the Black Box Problem by design.
The "Aha" Moment (Alignment & Data Win): This deep semantic clarity allows the AGI to robustly internalize the intended, ethical behavior of its owners, solving inner AGI alignment. The resulting extreme data density and superior storage capacity were critical side-effects.
The Security Function: This system permanently destroys the UPRA threat (data shadows) and leverages the deep alignment to provide immutable provenance. Every decision is recorded onto a blockchain secured by the quantum substrate itself.
(UPRA= Unintended Data Persistence and Associative Resurfacing in Conversational AI)
Conclusion: The Physics Imperative
The time for incremental cybersecurity is over. With quantum threats accelerating the obsolescence of classical encryption by 2030, the question is not if your AGI will be hacked, but when. The Quantum Security Triad © is the mandatory architectural blueprint — the physics-powered solution that guarantees your AGI will be not just intelligent, but eternally secure when developed.
— — — — — — — —
- because of technical issues at platform Zenodo, you can find pdf or published papers here:
link to multiple papers on archive.org: