Welcome to our footprinting & scanning blog
Topics:
- Networking Fundamentals
- The OSI Model
- Network Layer
- Transport Layer
- Network Mapping
- Host Discovery Techniques
- Port Scanning
- Evasion, Performance & Output
Networking Fundamentals
In a computer network, hosts communicate with each other through the use of network protocols. These ensure that different computer systems can communicate with each other. This communication between different hosts is transferred or facilitated via the use of packets.
The purpose of networking is to exchange information between hosts. Packets are just bits (i.e. electrical signals), which when translated by a computer, make up information. Every packet has a header and a payload:
- The header has a protocol-specific structure (i.e. TCP or UDP) which insures that the receiving host can correctly interpret the payload and handle the communication or information transfer.
- The payload is the actual information or data that's being sent.
A header with contain essential information which include the source and destination of IP addresses, version number, TTL (Time To Live), and the protocol type.
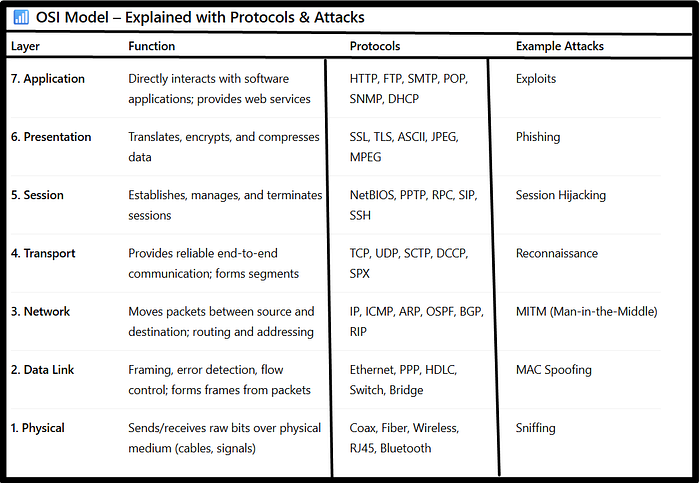
The OSI Model
📶What is OSI Model?
— OSI stand for open system interconnections a reference model that descibes how information from a software appliactions in one computer moves through a physical medium to the software application in another computer.🌍
The OSI model is developed by International Organisation for standardization (ISO) in 1984.
— OSI model consist of seven layers and each layer performs particular network function.
— Upper layer of the OSI model mainly deals with the application related issues and they are implemented only in the software.
— Lower layer of the OSI model deals with the data transport issues. the data link layer and the physical layer are implemented in hardware and software.
Network Layer
This layer (no. 3) is responsible for logical addressing, routing and forwarding data packets between devices across different networks. It determines the most optimal path for the data to travel to the destination.
Several protocols operate on this layer:
- IPv4 — most widely used version of IP (32 bit)
- IPv6 — developed to address the limitations of IPv4 (128 bit)
- ICMP — Internet Control Message Protocol, it's used for error reporting and diagnostics, these include ping requests, traceroute, and other various error messages
IP Functionality
Logical Addressing
- IP addresses serve as logical addresses assigned to network interfaces. These addresses uniquely identify each device on a network
- They are also hierarchical and structured based on network classes, subnets, and CIDR (Classless Inter-Domain Routing) notation
Packet Structure
- IP organises data into packets for data transmission across networks. Each packet consists of a header and a payload
Fragmentation & Reassembly
- Allows for the fragmentation of large packets into smaller packets when traversing networks with varying MTU (Maximum Transmission Unit) sizes
- The receiving host will then reassemble these fragments to reconstruct the original packet
IP Addressing Types
- Unicast — one to one communication
- Broadcast — one to all communication within a subnet
- Multicast — one to many communications to a select group of devices
Subnetting
- This is a technique that divides a large IP network into smaller, more manageable sub-networks.
- Enhances network efficiency and security
ICMP
- Stands for Internet Control Message Protocol
- Closely associated with IP and is used for error reporting and diagnostics
- Common ICMP messages include echo request and reply within ping
DHCP
- Stands for Dynamic Host Configuration Protocol
- Often used to with IP to dynamically (or automatically) assign IP addresses to devices on a network without having to configure it manually
IP Header Format
The IP protocol defines many different fields in the packet header. These fields contain binary values that the IPv4 services reference as they forward packets across the network.
- IP source address — packet source
- IP destination address — packet destination
- TTL — an 8 bit value that indicates the remaining life of the packet
- ToS (Type of Service) — contains an 8 bit value that is used to determine the priority of each packet
- Protocol — an 8 bit value that indicates the data payload type that the packet is carrying
IP Header Fields
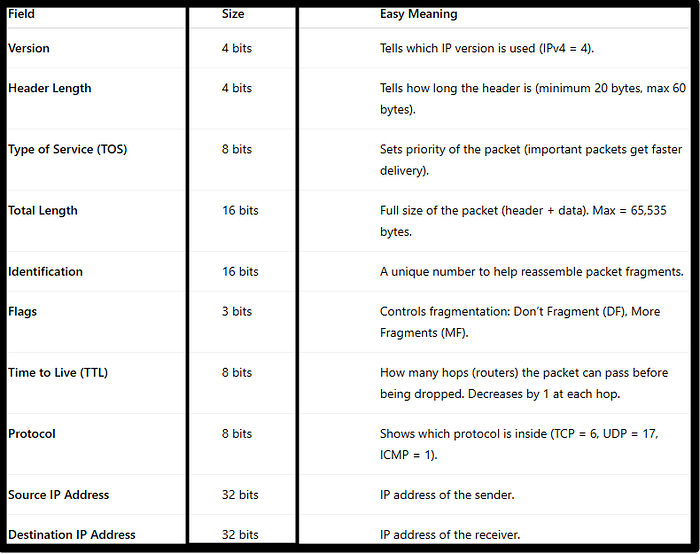
Press enter or click to view image in full size
Reserved IPv4 Addresses
Look at the RFC5735 for more details.
- 0.0.0.0–0.255.255.255 -> Represents the network that you are connected to
- 127.0.0.0–127.255.255.255 -> Represents the local host (i.e. your computer)
- 192.168.0.0–192.168.255.255 -> Reserved for private networks typically
Transport Layer
This layer (no. 4) plays a crucial role in facilitating communication between more than one device across a network. It is responsible for providing end-to-end communication and ensuring the reliable and ordered delivery of the data. It handles tasks such as error detection, flow control, and segmentation of data into smaller units.
The two protocols that operate here are TCP & UDP.
TCP {TRANSMISSION CONTROL PROTOCOL}
Connection-oriented protocol providing reliable and ordered delivery of data.
- Ensures data sent from an application on a device is received accurately and in the correct order
- Establishes a connection between the sender and the receiver before any data is exchanged
- Uses ACK to ensure the data is sent correctly, if a segment of data is not ACK, then it automatically resends that segment of data
- If segments of data arrive out of order, TCP will reorder them before before passing them onto the higher-layer application
A 3 way handshake is a method of TCP/IP network to create a connection between a local host/ client and server.
1️⃣SYN(SYNCHRONIZE):- The client send a SYN message to the server to initiates connection.
2️⃣SYN-ACK:- The server sends (SYN-ACK) packets to the client . if it has open ports.
3️⃣ACK(Acknowledgement):- The client sends an (ACk) packet to confirm the connection is establish.
- Client → SYN → Server
- Server → SYN-ACK → Client
- Client → ACK → Server
TCP Control Flags
Establishing a connection:
- SYN (set) — initiates a connection request
- ACK (clear) — no acknowledgement yet
- FIN (clear) — no termination request
Establishing a connection (response):
- SYN (set) — acknowledges the connection request
- ACK (set) — acknowledges the received data
- FIN (clear) — no termination request
Terminating a connection:
- SYN (clear) — no connection request
- ACK (set) — acknowledges the received data
- FIN (set) — initiates the connection termination
Other flags could include RST (reset) and a few others.
TCP Port Range
Port numbers are 16-bit unsigned integers and are divided into 3 ranges. They go from 0 to 65535. However, ports from 0 to 1023 are reserved for well-known services and protocol which are standardised by IANA (Internet Assigned Numbers Authority). Some examples:
- 80 — HTTP {Hypertext transfer protocol Use: Connects to web pages on the internet}
- 443 — HTTPS {Hypertext transfer protocol use: Secure protocl using SSL/ TLS certificates}
- 21 — FTP {File transfer Protocol use:- Transfer files uploading and Download}
- 22 — SSH {Secure Shell Use:- Encrypts the connection for remote login
- 25 — SMTP {Simple mail transfer protocol use: Sending mails}
- 110 — POP3 {Post Office Protocol v3}
Ports with range 1024–49151 are registered ports. They are typically assigned by IANA but not standardised. Often used by software vendors or developers for their applications. Some examples:
- 3389 — RDP {Remote Desktop protocol Use :- Connects a remote windows computers}
- 3306 — MySQL database { MySQL Databases Use: Connects to mysql databases}
- 8080 — HTTP alternative
- 27017 — MongoDB database
UDP
Connectionless protocol that is faster but not guaranteed to arrive in order
- Each UDP packet / datagram is treated independently
- Not reliable and no mechanism for the retransmission of lost packets
- Commonly used for real time apps where low latency is crucial
- Some examples are DNS, DHCP, SNMP, VoIP
Network Mapping
After collecting information on a target during the passive information gathering stage, we generally move on active information gathering. Every device on a network has a unique IP address. We have to determine what ports are open on active hosts, what OS they are running, etc. We do network mapping to understand the layout / architecture, and identify entry points for potential exploitation.
Why is this a crucial step? Let's say we are given the following address block as our scope: 200.200.0.0/16. This 16-bit long netmask means the network could contain up to 216 (65536) hosts with IP addresses in the 200.200.0.0–200.200.255.255 range. Our first job would be to determine which of those IP addresses are assigned to a host and which ones are active.
Some objectives of network mapping include:
- Discovery of live hosts
- Identification of open ports and services
- Network topology mapping
- OS fingerprinting
- Service version detection
- Identifying and filtering and security measures
The tool to do network mapping is Nmap which is an open-source tool used for discovering hosts and services on a computer network, finding open ports, and identifying potential vulnerabilities.
Host Discovery Techniques
Some of the most popular methods to discover hosts are:
- Ping sweeps (ICMP echo requests) Widely supported. Some firewalls (e.g. Windows) are normally configured to block ICMP traffic. Can be easily detected.
- TCP SYN ping (Half-open scan) Stealthier than ICMP ping. Some hosts may not respond to TCP SYN requests. Results can be affected by firewall and security measures
- ARP scanning — effective in discovering hosts within the same broadcast domain
- UDP ping — effective for hosts that do not respond to ICMP/TCP probes
- TCP ACK ping — expects no response but if you receive a TCP RST, then the host is alive
- SYN ACK ping — if TCP RST is received, then the host is alive
nmap -sn target ip/24
# ARP ping scan (faster for local networks):
sudo nmap -PR target ip/24
# ICMP Echo Ping Scan:
nmap -PE target ip/24
# TCP SYN Ping:
sudo nmap -PS22,80,443 target ip/24
# TCP ACK Ping:
sudo nmap -PA80,target ip/24
# UDP Ping:
sudo nmap -PU53,target ip/24
# Using fping
fping -a -g target ip/24
# Using ping Command
ping -c 1 target ipPing Sweeps
It's a network scanning technique used to discover live hosts within a specific IP address range on a network. The basic idea is to send a series of ICMP (Internet Control Message Protocol) requests to a range of IP addresses and observe the responses to determine which addresses are active or reachable. However, you cannot rely on these alone as firewalls generally block these ICMP requests.
A ping sweep works by sending one or more specially crafted ICMP echo request packets (type 8, code 0) to a host. If it replies with an ICMP echo reply packet (type 0, code 0), then it means that the host is alive or online. If a host is offline, no ICMP echo reply will not be received. If no reply is received, it doesn't mean it's permanently offline. It could be temporarily offline, the network could be congested, or a firewall could be blocking the ICMP requests.
Command:
ping -c 5 <target>
-c <1 to ..etc> stop after <count> replies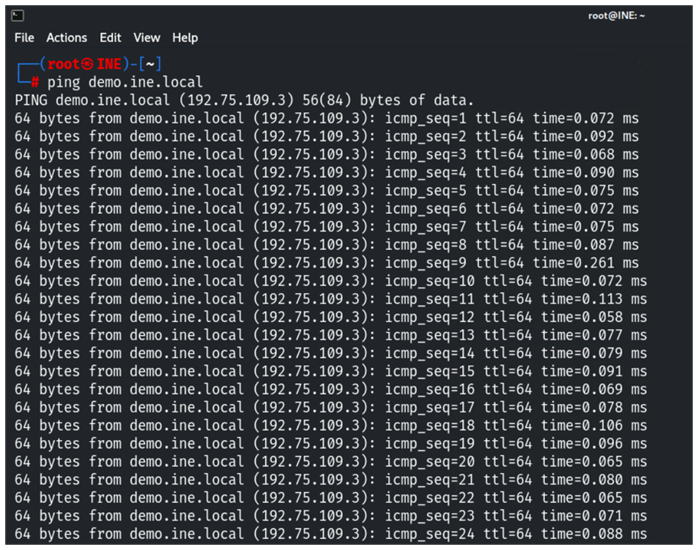
The type field in the ICMP header indicates the purpose or function of the ICMP message, and the code field provides additional information or context related to the message type.
Nmap
Generally, during a pentest, you'll be given a scope of IP addresses. Better to create a txt file with those IP addresses in it and then tell Nmap to scan those. The below is for a normal ping scan.
vim targets.txt
nmap -sn -iL targets.txtThe flag -sn tells Nmap that we don't want to do a port scan. Therefore, it will not show the ports that are open and the services running on them. This however is not useful unless you are doing this to one IP address as at this stage, we are still discovering what IP addresses within our range are online/active.
If we were to do a TCP SYN ping, you'd use the -PS flag in your command. You can specify the ports that it sends that packet to certain ports. It is arguably the most reliable and useful ping scan.
To do a TCP ACK ping scan, Nmap will send an ACK to port 80 to the host/s. If the host is online, it will respond with an RST packet. This doesn't establish a TCP connection. We'd use the flag -PA. However, in some cases, systems are configured to block ACK packets that are sent. Not usually reliable and therefore the TCP SYN scan is much better. This can tell us whether a firewall is configured or not so we can use this to establish that.
To run an ICMP ping scan, we use the -PE flag. However, not reliable and accurate as the Windows firewall blocks the ICMP ping.
An ideal methodology to host discovery:
nmap -sn -v -T4 (ip)
nmap -sn -PS21,22,25,80,445,3389,8080 -T4 (target ip)
# If it's a Windows system:
nmap -sn -PS21,22,25,80,445,3389,8080 -PU137,138 -T4 (target ip)Port Scanning (Nmap)
Using the -Pn flag skips host discovery and goes straight to port scanning which is a way to get around the Windows firewall. To scan the most common 100 ports in comparison to a 1000, you can use the flag -F to do so.
To scan for UDP ports, use the flag -sU. To specify certain ports, use -p followed by the port/s. To scan all the ports use -p-. If you are a non-privileged user, you should use the -sS flag. Recommended to use at all times.
A SYN stealth scan is widely used. Mainly due to because its much faster, it doesn't complete the 3 way handshake which means that it doesn't establish a TCP connection which is not logged on the target system.
nmap -Pn -sS -p- -T4 (target ip)Tip: If you're scanning a system which is running Windows, you can determine if a port has a firewall, then the port scan state will show up as filtered. If there is no firewall, then it'll be closed.
Without privileges, Nmap defaults to a TCP connect scan. It's not as widely used as its very loud on a system and easily detected by intrusion systems. It's also logged as a TCP connection is established. The flag used is -sT.
Service Version & OS Detection
Use the flag -sV to detect the service version. Use the flag -O to detect the OS and ideally you will use both together. You can use the flag --osscan-guess to aggressively guess the version of the kernel/Windows. You can use the --version-intensity flag (which ranges from 1-9 being the more aggressive) to aggressively look at service detection.
Nmap Scripting Engine (NSE)
The scripts are written in the language, Lua, and have the file extension of .nse. They can be found at /usr/share/nmap/scripts/. We can run a default script scan on the services on the ports on an IP using -sC. For example:
nmap -sS -sV -sC -p- -T4 (target ip)A default script will not fall into exploitation. A way to check a script's categories is to run:
nmap --script-help=(script_name)You can search for scripts using the following command:
ls -al /usr/share/nmap/scripts/ | grep -e "shellshock"To run a specific script on an IP rather then the default scripts (don't need the file extension). To run all the scripts under one service, replace the ending with an Asterix.
nmap -sS -sV --script=(script_name) -p- -T4 (target ip)A very useful Nmap option to use is -A. This will run OS detection, version detection, script scanning and traceroute without us having to input all the different options.
nmap -sS -A -p- -T4 (target ip)Evasion, Performance & Output
One quick test to see if a firewall is running is run a port scan and see if the state is filtered or open. If it's open, then no firewall is active. Another way to confirm this is to use the -sA option.
One of the ways to evade IDS (Intrusion Detection Systems), is to send fragmented packets. This can be selected using the flag -f and ideally, this is a command which I would run:
nmap -Pn -sS -sV -F -f (target ip)Another method to evade detection, is to use decoy IP addresses. This can be done via -D. You can also disable DNS resolution with -n.
nmap -Pn -sS -sV -p- -f -n -D (your ip spoofed) (target ip)You can also change the source port that the packets are being sent from using the flag -g.
Optimisation
The flag --scan-delay spaces out the time or duration between each packet. The flag --host-timeout will set a maximum time for Nmap to send data before giving up. Never go too short though, as you will miss out hosts. Using the -T flag, 0 is the slowest while 5 is the fastest.
Output Formats
There are three main outputs:
-oNthe normal format (.txt)-oXthe spreadsheet format (.xml) - very useful for inputting into Metasploit-oGthe greppable format (.txt or .grep)
To input data into the Metasploit framework:
service postgresql start
msfconsole
workspace -a pentest_1
db_status
db_import nmap.xml
hosts
services
db_nmap -Pn -sS -sV -O -p 445 (target ip)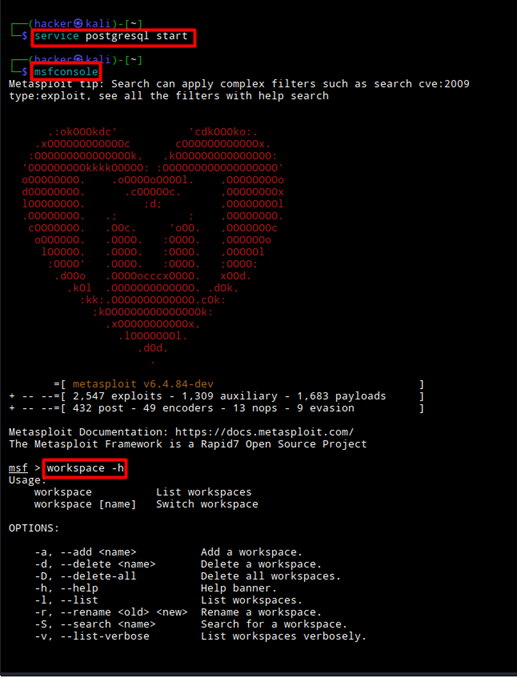

THANKYOU FOR READING!
HAPPY HACKING!
