Security isn't just about fixing vulnerabilities — it's about designing systems that resist them.
Introduction
In today's modern software landscape, where cloud-native applications and rapid CI/CD deployments dominate, embedding security across every stage of the software lifecycle is not optional — it's essential.
Over the course of five weeks, I designed, developed, exploited, and secured a vulnerable authentication API to simulate real-world attack scenarios and implement enterprise-grade remediation.
The project's goal was simple:
To demonstrate a full AppSec and DevSecOps workflow — from code to cloud — integrating secure design, threat modeling, risk analysis, and automated pipeline security.
Project Overview
Objective
Create an intentionally vulnerable web API that mimics a production environment and use it to:
- Identify common OWASP Top 10 vulnerabilities.
- Perform threat modeling and risk analysis.
- Integrate security controls into the CI/CD pipeline.
- Securely deploy to AWS ECS/ECR/S3 following least-privilege principles.
Key Deliverables
- Built a vulnerable Node.js authentication API to simulate OWASP Top 10 flaws.
- Implemented RBAC, JWT Auth, and demonstrated privilege escalation attacks and mitigations.
- Designed a Threat Model (STRIDE) and a Risk Register for security prioritization.
- Integrated a GitLab CI/CD pipeline with SAST, SCA, DAST, and Secret Scanning tools.
- Deployed securely on AWS ECS using private registries, IAM roles, S3, and CloudWatch.
Week 1 — Building a Vulnerable Application
Goal:
Develop a deliberately insecure Node.js Authentication API to observe how developer mistakes lead to exploitable vulnerabilities.
Vulnerabilities Simulated
- Input Validation Failure → NoSQL Injection & XSS.
- Sensitive Data Exposure → Leaked credentials in .env files.
- Error Leakage → Verbose stack traces revealing backend logic.
- Broken Access Control (IDOR) → Users accessing other users' data.
- Weak JWT Secrets / Hardcoded Credentials.
- Plaintext Password Storage.
- Missing Rate Limiting → Brute-force exposure.
Key Learning
Each vulnerability was mapped to OWASP Top 10 categories to understand root causes and mitigation techniques. This provided the foundation for threat modeling and secure coding principles used later.
Week 2 — Authentication, RBAC, and Access Control
Objective:
Implement Role-Based Access Control (RBAC) and test for authorization flaws. Add an admin route for deletion and the users list.
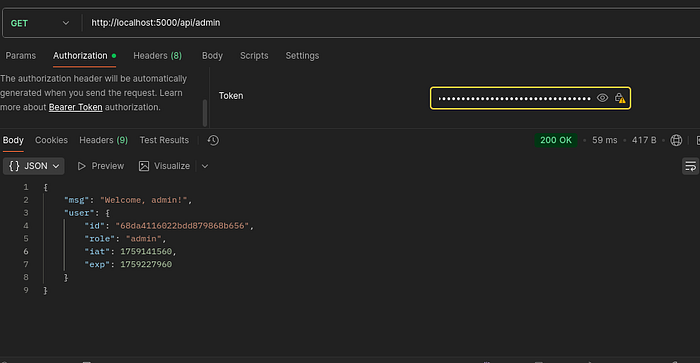
Key Findings:
- Weak JWT secret allowed token forgery → full privilege escalation.
- IDOR vulnerability enabled access to other users' profiles.
- Missing authorization checks allowed destructive admin operations.
- Excessive Data Exposure revealed sensitive user objects.
OWASP Mappings:
A01 — Broken Access Control
A02 — Broken Authentication
A03 — Excessive Data Exposure
A05 — Security Misconfiguration
Business Impact:
Such flaws could cause:
- Unauthorized account takeover
- Data leakage (PII/GDPR violations)
- Compliance penalties and reputational harm
Mitigation Measures:
- Strong, random JWT secrets via environment variables.
- Middleware enforcing requireOwnerOrAdmin checks.
- Short-lived access tokens + refresh tokens.
- Audit logs and anomaly detection for sensitive endpoints.
Week 3 — Threat Modeling
Objective:
Use OWASP Threat Dragon and STRIDE to visualize and prioritize risks.
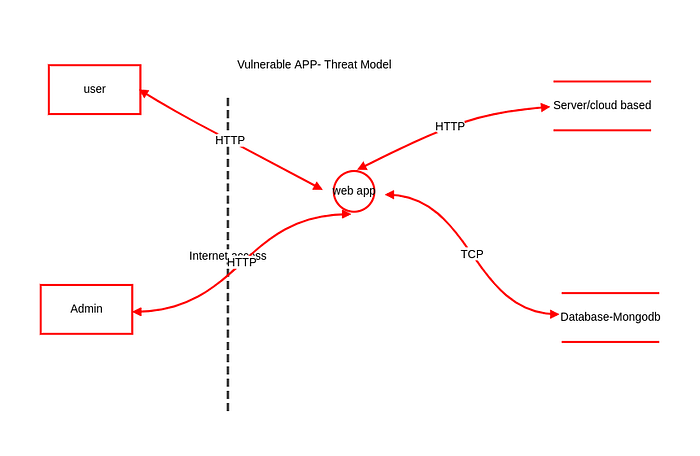
Threats Identified
Threat STRIDE Category Severity
- JWT Secret Exposure Spoofing / Elevation of Privilege: Critical
- Insecure MongoDB Config Tampering / Info Disclosure: High
- Plaintext Password Storage Info Disclosure: Critical
- Lack of HTTPS Spoofing: High
- No Rate Limiting Denial of Service: High
Mitigation Strategy:
- Secret rotation & Vault storage (e.g., AWS Secrets Manager).
- Enforce DB authentication and secure network binding.
- HTTPS + HSTS header enforcement.
- Rate limiting and CAPTCHA.
- IAM hardening and runtime monitoring.
Risk Analysis
Objective:
Quantify risks using Likelihood × Impact Matrix
Risk Likelihood Impact Rating
- Hardcoded JWT Secret - High Critical
- Plaintext Passwords -High Critical
- Exposed MongoDB -Medium High
- No TLS Enforcement- Medium High
Treatment Plan:
- Remove secrets from code; enforce GitLeaks scanning.
- Hash passwords with bcrypt or Argon2.
- Secure HTTPS-only deployment.
- Harden MongoDB and implement role-based DB access.
---
Week 4 — DevSecOps CI/CD Security Pipeline
Objective:
Automate security across the pipeline to ensure Shift-Left Security.
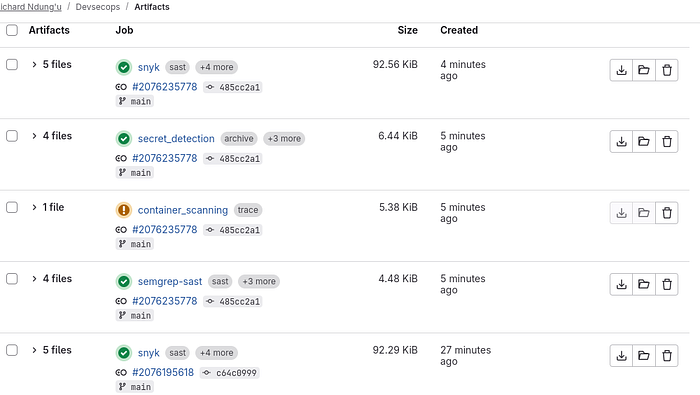
Pipeline Tools Integrated
- SAST Semgrep Detect insecure code patterns
- SCA Snyk + GitLab Identify vulnerable dependencies
- Secrets GitLeaks Scan leaked keys and credentials
- Container Trivy Scan images for CVEs
- DAST OWASP ZAP Runtime scanning of the deployed app
Key Practices:
- Security integrated early (Shift-Left)
- Automated vulnerability dashboards in GitLab
- Merge Request gates to prevent vulnerable builds
- False-positive tuning to streamline Dev workflow
Week 5 — AWS Cloud Security & Deployment
Objective:
Securely deploy the application to AWS ECS (Fargate) using containerization and least privilege.
Steps Implemented
1. IAM Configuration — users, roles, and policies using least-privilege principle.
2. Dockerization — reproducible builds.
3. ECR — private image registry.
4. ECS (Fargate) — managed container hosting.
5. VPC Security Groups — segmented access control.
6. S3 Bucket — restricted access for image storage.
7. CloudWatch — centralized logging and alerting.
Cloud Security Controls Applied
- Enforced defense-in-depth with layered network segmentation.
- Enabled encryption in transit (TLS) and at rest (S3/IAM policies).
- Enabled continuous monitoring and alerting.
Weekly focus and deliverables
Each week contains a different focus that is critical to application security :
- Week 1–2 AppSec & Secure Coding Node.js, JWT, RBAC Vulnerability discovery & mitigation
- Week 3 Threat Modeling OWASP Threat Dragon, STRIDE Prioritized threats & risks
- Week 4 DevSecOps GitLab, Semgrep, Snyk, Trivy Automated CI/CD scanning
- Week 5 Cloud Security AWS ECS/ECR/S3/IAM Secure deployment & monitoring
Technical Skills
This project helps one gain these skills:
- Programming & API Security Node.js, Express, MongoDB Secure coding, JWT, RBAC
- AppSec Testing OWASP ZAP, Postman, Manual testing & exploit analysis DevSecOps Automation GitLab CI/CD, Semgrep, Trivy, GitLeaks
- Automated scanning pipelines
- Cloud Security AWS ECS/ECR/IAM/S3 Secure deployment & runtime security
- Threat Modeling STRIDE, Threat Dragon Architecture risk analysis
- Security Governance OWASP Top 10, NIST 800-53 Risk treatment & policy alignment
Roles suited
For cybersecurity engineers learning appsec, the project is suited for these roles:
Application Security Engineer
- Conducts code review, SAST/DAST integration, and remediation.
- Designs secure auth flows (RBAC, JWT, encryption).
- Builds threat models and delivers actionable risk reports.
DevSecOps Engineer
- Embeds scanning tools in CI/CD pipelines.
- Automates compliance and vulnerability reporting.
- Applies container hardening and shift-left principles.
Cloud Security Engineer
- Manages IAM, VPC, and encryption policies.
- Implements continuous monitoring (CloudWatch, GuardDuty).
- Ensures security configuration management.
Secure SDLC Contributor
- Integrates security checks across SDLC stages.
- Facilitates security design reviews and engineer enablement.
- Aligns AppSec metrics with DevOps velocity.
Final Reflection
This project embodies real-world application security engineering — not just vulnerability discovery, but strategic defense-building.
I learned how to:
- Transform insecure APIs into resilient ones.
- Embed automated scanning into CI/CD pipelines.
- Deploy securely to AWS with least privilege and defense in depth.
- Document risks and remediation using professional frameworks.
> "DevSecOps isn't about slowing development — it's about accelerating secure delivery."
This project can help anyone interested in gaining appsec skills
Project Repository
GitHub: https: //github.com/richardndungu94/Devsecops.git
#DevSecOps #AppSec #ApplicationSecurity #CloudSecurity #ThreatModeling #OWASP #AWS #SAST #DAST #GitLab #SecureSDLC #CyberSecurity #InfoSec #NodeJS #SoftwareSecurity

