Local File Inclusion (LFI) is one of the most common yet impactful vulnerabilities in modern web applications. It arises when user-supplied input is used to build file paths without proper sanitization or validation. Exploiting LFI can lead to unauthorized access to sensitive system files, information disclosure, or even remote code execution under specific conditions.
This presentation will demonstrate how I approach vulnerability research, specifically focusing on identifying LFI and Path Traversal flaws. The discussion will cover reconnaissance techniques, parameter discovery, proof-of-concept exploitation, and the potential security implications of such vulnerabilities.

Introduction
Local File Inclusion vulnerabilities occur when a web application dynamically includes files on the server based on user input. If the input is not properly sanitized, attackers can manipulate parameters to load unintended files, sometimes even executing malicious payloads. This talk aims to provide a step-by-step walkthrough of how I conduct my reconnaissance, test for inclusion points, and validate the presence of an exploitable vulnerability. By sharing this methodology, I hope to raise awareness among security researchers and developers about the importance of secure coding practices and thorough validation.
How to Hunt Local File Inclusion?
To find Path Traversal vulnerability we have to do slight recon as follows
- Crawl the target website
- find the inclusion function paramerter
Methodology for Hunting Path Traversal and LFI
1. Reconnaissance and Crawling
The first step is to enumerate all accessible endpoints of a target application. Crawling ensures that we have a complete map of URLs and their associated parameters. Tools such as gau (GetAllUrls), Burp Suite Spider, or custom scripts can be used for this purpose.
Example workflow:
- Use gau to extract archived URLs from various sources.
- Use Burp Suite to crawl and identify hidden or dynamic parameters.
gau target.com > urls.txt2. Identifying Parameters of Interest
Once we collect the URLs, the next step is to search for parameters that are likely to be tied to server-side file operations. Common parameters include:
file=, document=, folder=, root=, path=, pg=, style=, pdf=, template=,
php_path=, doc=, page=, name=, cat=, dir=, action=, board=, date=,
detail=, download=, prefix=, include=, inc=, locate=, show=, site=,
type=, view=, content=, layout=, mod=, conf=, url=To automate the filtering process, I use tools like gf patterns, or alternatively, Burp Suite search functionality. This allows me to quickly isolate parameters that might accept user-controlled input leading to inclusion.
3. Manual Testing of Parameters
After isolating potential candidates, I manually test each parameter for file inclusion or path traversal behavior.
Example test case:
http://█████.redacted.com/showimage.php?file=By injecting traversal sequences such as ../, I can attempt to escape the intended directory and access sensitive files.
4. Proof of Concept Exploitation
The most common sensitive file to test for is /etc/passwd on Unix/Linux systems. This file contains account information and is often the first step in confirming an LFI vulnerability.
Example attempt:
http://█████.redacte.com/showimage.php?file=../etc/passwdIf unsuccessful, additional traversal sequences can be tested:
http://█████.redacted.com/showimage.php?file=../../etc/passwdWhen successful, the /etc/passwd file is disclosed, proving the existence of an LFI vulnerability.
Why /etc/passwd is Important
The /etc/passwd file stores essential details about user accounts, including:
- Username
- User ID (UID)
- Group ID (GID)
- Home directory
- Default shell
While it no longer stores password hashes (moved to /etc/shadow in modern systems), the file remains critical for system operation and can provide attackers with valuable reconnaissance data, such as valid usernames for brute force or privilege escalation attempts.
Demonstration (Step by Step)
- Website Crawling with gau Collect URLs from archives and public sources.
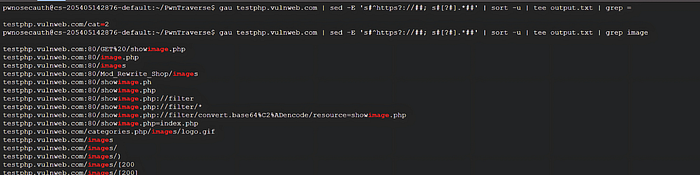
- Parameter Discovery with PwnTraverse Filter URLs to highlight potentially dangerous parameters and save as domain.txt run as python3 main.py — file domain.txt
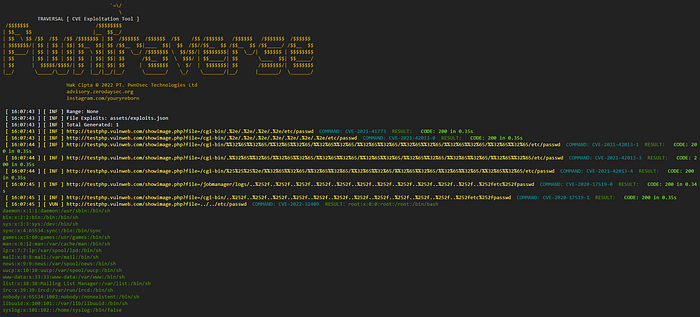
- Manual Payload Injection
Test URLs with
../sequences for path traversal attempts. - Successful Exploitation
Access sensitive files like
/etc/passwd.
Impact of Local File Inclusion
The risks of an exploited LFI vulnerability can vary depending on the context:
- Information Disclosure: Attackers can access server-side files, exposing sensitive data.
- User Enumeration: Extracting details from
/etc/passwdprovides valid usernames for further attacks. - Configuration Disclosure: Reading files such as
config.phpcan leak database credentials. - Remote Code Execution (RCE): In some cases, attackers can include log files or uploaded files containing malicious PHP code, leading to RCE.
Thus, while an LFI might seem like a minor flaw, its impact can escalate into a severe system compromise.
Conclusion
Local File Inclusion vulnerabilities highlight the importance of secure coding practices and strict validation of user input. My methodology — starting from reconnaissance, identifying potential parameters, testing for traversal, and validating exploitation — demonstrates a practical way to identify these flaws during vulnerability research.
Key Takeaways:
- Always validate and sanitize user inputs.
- Restrict file inclusion to whitelisted directories.
- Regularly test and audit applications with both automated and manual techniques.
By addressing these issues proactively, organizations can protect their systems from potentially devastating attacks and ensure the confidentiality, integrity, and availability of their services.
PwnTraverse is an advanced Path Traversal & Endpoint Vulnerability Scanner designed for security researchers, bug bounty hunters, and penetration testers. This tool automates the discovery of Path Traversal vulnerabilities and related CVEs, helping security professionals quickly assess and report security issues.

