While most individuals use Google for everyday tasks — like finding the nearest restaurant or streaming entertainment — cybersecurity professionals and malicious actors alike harness its power for a very different purpose. With the right search techniques, it's possible to uncover hidden login portals, exposed credentials, misconfigured servers, and even unsecured database backups.
This practice is known as Google Dorking — a powerful reconnaissance method that reveals just how much sensitive information is unintentionally left exposed online.
🤔 What is Google Dorking?
Google Dorking, also known as Google Hacking, is the art of crafting advanced search queries to uncover publicly accessible (but not always intended to be public) information from websites.
Let's say you want to look for leaked SQL files containing passwords. Here's a dork that might do the job:

Look at the information we've uncovered — it all comes down to how effectively we use the search engine
filetype:sql intext:passwordThat's not hacking the system — that's just using Google smartly.
These "dorks" are simply search filters that Google understands. Combine a few cleverly, and you'd be surprised what you can find — from unsecured webcams to misconfigured admin panels.
For example, if you want to find a list of doctors in the specific location, you can use Google dorks to discover publicly available documents containing details like specialist names and their contact numbers. Some useful dorks include:
filetype:pdf intext:"location" intext:"Contact Number"
filetype:doc intext:"Doctors" intext:"Phone"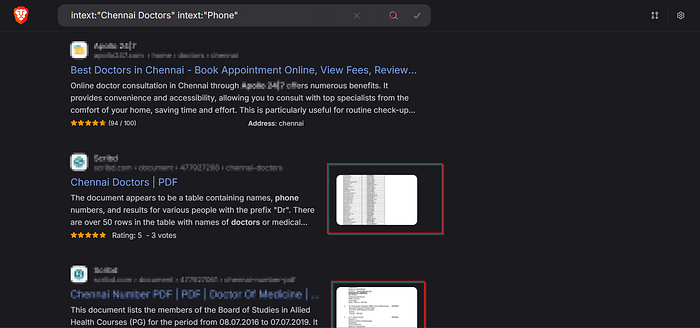
In this case, we're using Google Dorking to uncover potentially sensitive information that has been indexed by search engines — all through advanced search techniques.
🛠️ Tools That Make Dorking Easier
You don't have to manually run every dork yourself. Some tools do the heavy lifting for you:
1. Google Search Itself
Yes, plain old Google is your first and most powerful dorking tool. All you need is the right query.
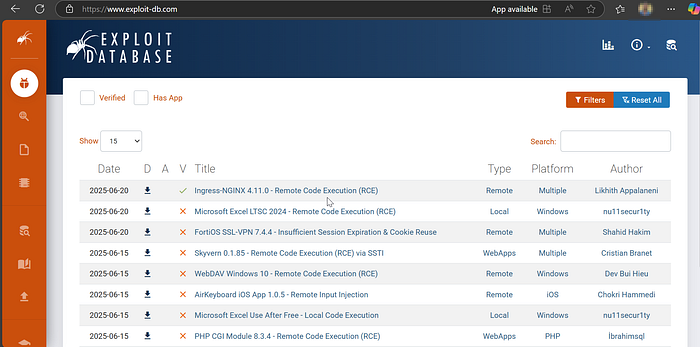
2. Google Hacking Database (GHDB)
Maintained by Offensive Security, GHDB is a goldmine of pre-built, proven dorks. 🔗 exploit-db.com/google-hacking-database
3. GitHub-Dorker
A tool to scan GitHub for secrets like API keys, passwords, and tokens using specific dorks. Great for developers who forgot to .gitignore their secrets.
4. DorksEye
A command-line tool that automates dorking with multiple search engines. Useful for penetration testers doing recon.
5. ReconSpider / SpiderFoot
OSINT frameworks that include dorking capabilities among many other recon features.
🌐 Real-World Use Cases
Google Dorking isn't just a hacker's trick — it's used by professionals across industries:
- 🔎 OSINT Investigators use it to trace online footprints.
- 🧪 Bug Bounty Hunters find misconfigurations and earn rewards.
- 👨💻 Pentesters uncover attack surfaces during assessments.
- ⚠️ Black Hat Hackers exploit exposed resources for malicious purposes.
Try These Dorks (For Learning Only!)
Here are some beginner-friendly dorks you can try ethically:
intitle:"index of" "backup"
filetype:env DB_PASSWORD
inurl:"/admin"
site:github.com "SECRET_KEY"
intitle:"phpinfo" "PHP Version"Note: Never access, exploit, or misuse the data you find. Stay within legal and ethical boundaries.
🛡️ How to Protect Against Google Dorking
If you manage a website or app, here's how to stay safe:
- 🚫 Use a
robots.txtfile to prevent Google from indexing sensitive directories. - 🔒 Add
noindexmeta tags on pages you don't want search engines to crawl. - Don't leave admin panels unprotected — use strong authentication.
- Clean up your codebase. Don't leave secrets or backup files lying around.
- 🕵️ Monitor your external exposure using tools like Shodan or Censys.
Conclusion
Google Dorking is both powerful and eye-opening. It teaches us that the internet isn't as tidy or secure as we might assume — and that knowledge is the first line of defense.
So next time you're Googling something random, remember: with the right syntax, Google becomes a reconnaissance weapon.
Use it wisely. Use it ethically. Stay curious. Stay safe. 🔍💻
👍 If you found this useful:
Give it a 👏, follow for more cybersecurity insights, or leave a comment with your favorite dork!
✍️Stay tuned for Day 6 — we've got something exciting coming up!

