OPC UA (Open Platform Communications Unified Architecture) is the protocol backbone of modern industrial automation. It's designed for interoperability, encryption, and cross-vendor communication — a must-have for Industry 4.0 systems.
But here's the catch: even the most secure protocol fails when misconfigured.
What is OPC UA?
OPC UA is a platform-independent, service-oriented protocol developed by the OPC Foundation. It's used to connect and orchestrate:
- PLCs
- SCADA and HMI systems
- MES and ERP layers
- Energy systems
- Sensors and actuators
It replaced legacy DCOM-based OPC protocols with modern security features: encryption, certificates, and authentication.
Sounds secure, right?
The Reality Check
Let's look at real-world data from Censys:
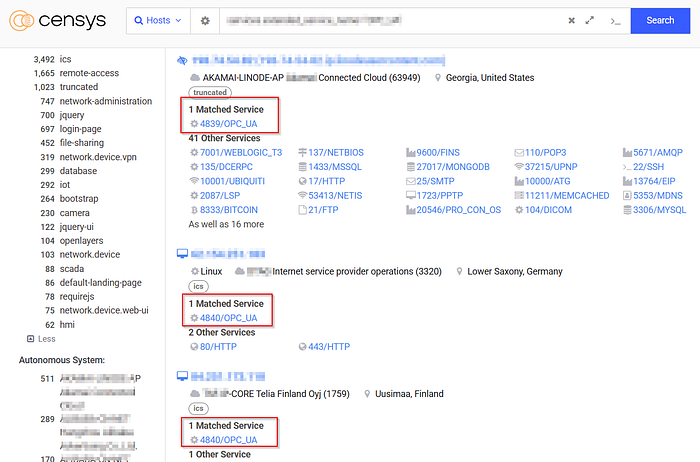
- 🌐 Over 4,500 OPC UA endpoints are exposed to the public internet
- ♨️ 2,700+ of these sit on TCP port 4840 — the default for OPC UA
- 🗽 The USA leads in exposed instances, followed by China and Germany
- 🎢 615 systems are tied to known, exploited CVEs
So what happened to "secure by design"?
It doesn't mean secure by default.
Common Misconfigurations That Break OPC UA Security
These mistakes aren't rare. They're everywhere.
- ❌ No authentication enabled at all
- ❌ Security policy set to "None/None" (no encryption, no signing)
- 🔓 Default or weak credentials still in place
- 📜 Expired, self-signed, or improperly validated certificates
- 🧱 Servers exposed directly to the internet, bypassing segmentation
- 🛠️ Outdated OPC UA stacks vulnerable to known exploits (CVEs)
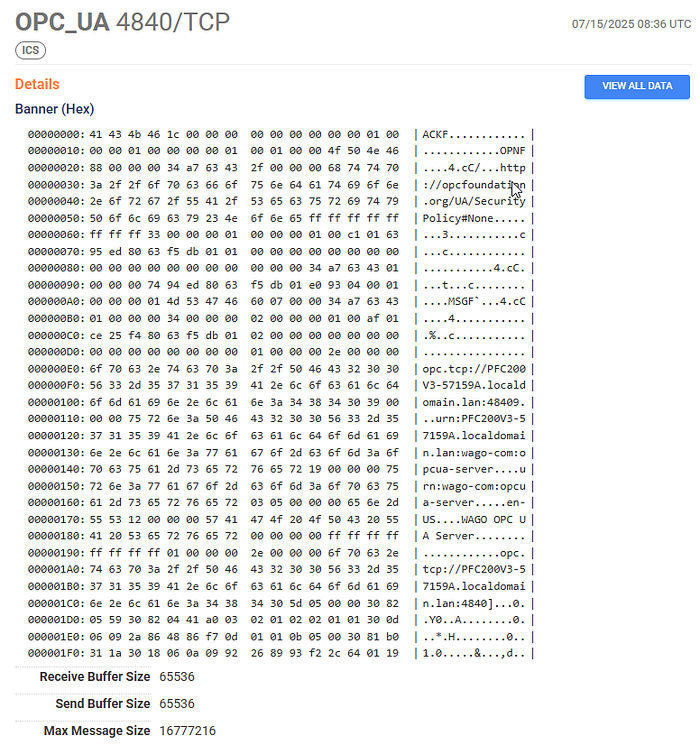
Every one of these issues turns a secure protocol into a soft target.
How to Actually Secure OPC UA
Here's your quick checklist to avoid being part of the statistics:
✅ Enforce only secure security policies (e.g., Basic256Sha256)
🔐 Use certificate-based authentication — not just username/password
🧱 Segment OPC UA traffic within your OT network, never public
🚫R Block
Final Thought
Modern ≠ secure. Encrypted ≠ impenetrable.
OPC UA can be secure — but only if configured, maintained, and monitored properly. One sloppy certificate, one unpatched library, one public IP… that's all it takes to compromise an entire industrial system.
This research part of oaps_another_attack_surface series, another interesting blog about industrial exposed: ProConOS Attack And you found me LinkedIn
Support Palestine
