Backstory
This article breaks down an XSS vulnerability discovered by la_revoltage, where Reddit's RichText parser failed to sanitize hyperlinks — but only under a specific condition: scheduled posts. The twist? The vulnerability wasn't in the live content — it hid in the editor. And it earned a $5000 bounty.
The Vulnerability in 60 Seconds
- Target: Reddit's scheduled posts
- Vector: A malicious hyperlink embedded using javascript: scheme
- Trigger: Editing the scheduled post in the UI
- Impact: XSS on privileged users (admins/mods) via a single click
This wasn't your classic post-XSS. It required interception, modification, and timing — but once triggered, JavaScript ran freely.
Step-by-Step Breakdown
- Create a Scheduled Post
Head to Reddit, create a new scheduled post, and embed any normal hyperlink. This works because scheduled posts go through a slightly different processing flow.
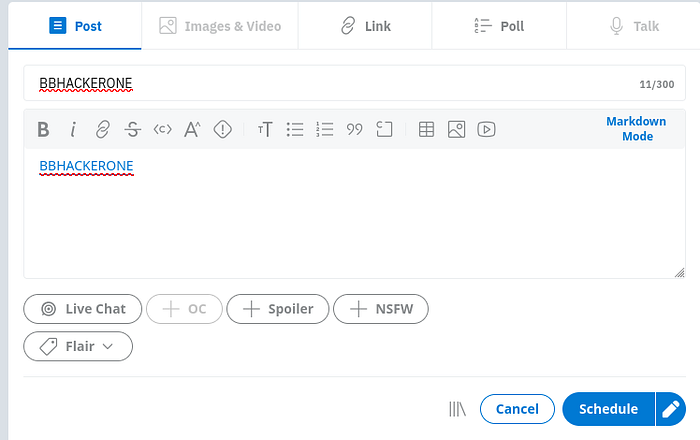
2. Intercept the Request
Use Burp Suite (or any proxy) to intercept the submission request.
Inside the request payload, locate the link markup and modify it like so:
"[Click me](javascript:alert('XSS'))"Yes, that's still valid Markdown. But Reddit's RichText parser normally filters this… just not here.

3. Edit the Scheduled Post
Now, navigate to the list of scheduled posts and click "Edit" on the one you just created.
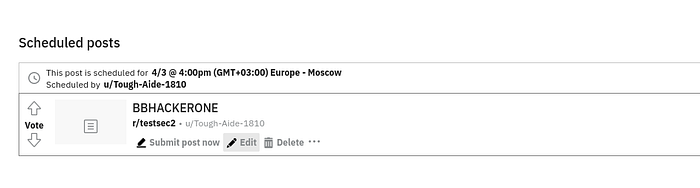
Boom. The XSS payload is still there. It appears as a clickable link.
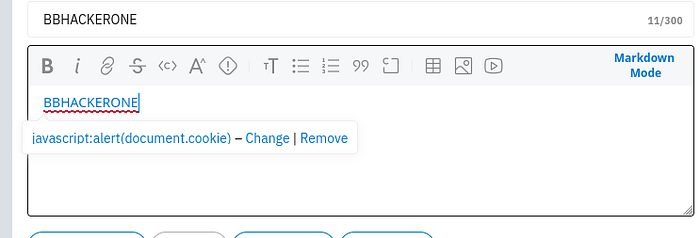
Why It Works (and Why It's Scary)
- Reddit's client-side validation filters were working fine — but server-side filtering was skipped during scheduled post submission.
- In regular posts, when RichText is converted to Markdown and finally to HTML, invalid links like javascript: are stripped.
- But this flow doesn't trigger until the post is published. So during editing, the bad link survives.
- If an admin or moderator clicks the forged link while editing a scheduled post, the JavaScript executes instantly.
Now imagine:
- A post designed to look innocent
- Reviewed by a mod before publication
- One misplaced click = account compromise
Impact
- Target Scope: Admins, mods, or privileged users reviewing scheduled content
- Vulnerability Type: Stored XSS (limited to pre-publish editing interface)
- Attack Vector: Social engineering (get a mod to click it)
- Bounty Awarded: 💰 $5000
How You Can Find Bugs Like This
This isn't a bug that jumps out — it's one that hides in feature-specific workflows. Here's how to dig into similar issues:
Focus on edge features:
- Scheduled content
- Drafts
- Previews
- Version history
Use these tools:
- Burp Suite to intercept and manipulate post requests
- Markdown cheat sheets to explore input/output behavior
- Interactsh or XSSHunter to detect blind XSS if needed
Test for:
- Inconsistent validation (client-side vs. server-side)
- Improperly filtered link schemes (javascript:, data:, etc.)
- Rendering differences between creation, edit, and preview views
Pro Tips for Hunters
- Don't just look at final posts — check every preview, draft, and editor.
- Hyperlinks with javascript: are still one of the easiest XSS vectors if you find the right place.
- Always compare how the system behaves before vs. after submission.
Credit
- Hunter: LaRevoltage (la_revoltage)
- Bounty: $5,000
- Report ID: 1930763
Final Thought
This bug wasn't in the headlines. It didn't involve uploading SVGs or chaining bugs into RCE. It was a single malformed link, in a single unguarded field — seen only by those who edit.
But it was worth $5000.
Let this be your reminder: the real vulnerabilities often hide not in what's live, but in what's scheduled.
Thanks for reading!
If you liked it, consider buying me a coffee.
Monika ☕✨

