Google dorks are special search terms that can help you find hidden information or vulnerabilities on websites.
1. My Favorite Google dork
Start with "site:<domain>". Then, exclude boring pages with "-www" or other terms until you get to the juicy stuff:
site:tesla.com -www -shop -share -ir -mfa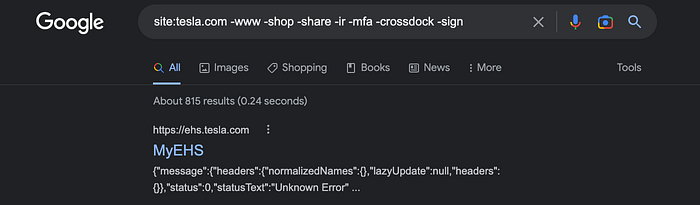
2. Pastebin Leaks
Check out sites like pastebin, jsfiddle, and codebeautify for code left over from developers:
site:pastebin.com
site:jsfiddle.net
site:codebeautify.org
site:codepen.io "tesla.com"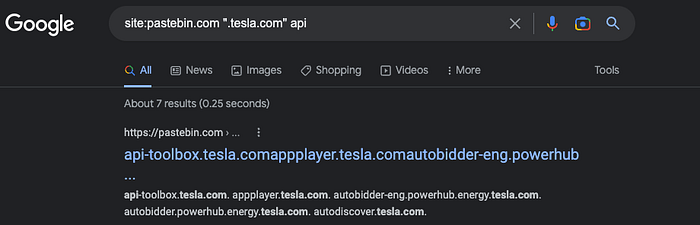
3. PHP extension w/ parameters
Use "ext:php" and "inurl:?" along with the domain to find .php files with a question mark in the url:
site:tesla.com ext:php inurl:?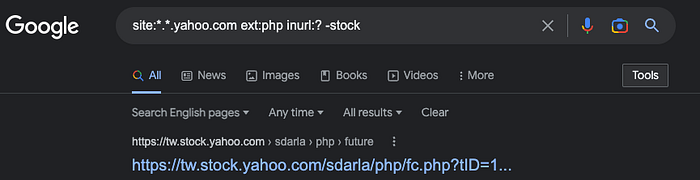
5. Disclosed XSS and Open Redirect Bug Bounties
Look through both fixed and unfixed bug bounties publicly disclosed through OpenBugBounty:
site:openbugbounty.org inurl:reports intext:"yahoo.com"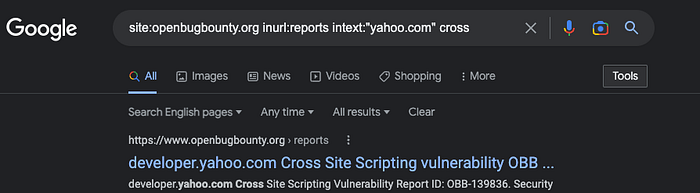
4. Combine your dorks
Use the "|" operator to include both queries or the "&" operator to require both queries. Here's an example of attempting to search for file upload endpoints across multiple domains:
(site:tesla.com | site:teslamotors.com) & "choose file"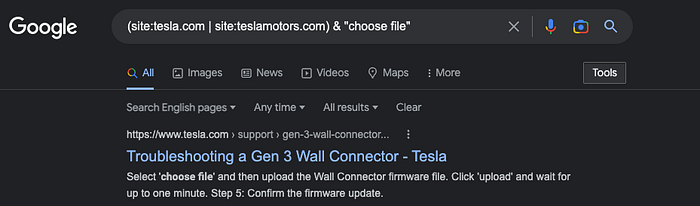
Bonus Dork: Alternative search engines
Try other search engines like DuckDuckGo, Bing, Baidu, and Dogpile to further expand your findings.

Be sure to check out the following resources for even more Google dorking tips and tricks:
Follow me on Twitter for daily hacking tips:
Happy hunting!
The Gray Area is a collection of great cybersecurity and computer science posts. The best articles are highlighted in a weekly newsletter sent out every Wednesday. To get updates whenever The Gray Area publishes an article, check out our Twitter page, @TGAonMedium.


