Introduction
WordPress is a Content Management System (CMS) that allows you to host and build websites. It contains plugins and templates so that you can customize any business, blog, portfolio, or online store. It's also incredibly popular, and full of P3+ bugs!
You'd think with so many users, they'd learn to secure their system. Fortunately for us pen-testers, they're not big fans on hardening their security themselves, so we do the freelance work for a little extra cash.
Detecting if a site is using Wordpress →
Using the 'Web App Analyzer', or Wappalyzer, we can figure out the services that any website uses.

Almost all kinds of CMS, programming languages, and operating systems are detected with this tool, and the best part? It's got a Google extension →
Using automatic scanners →
Automatic scanners can be incredibly helpful if used correctly. Some of these scanners, like Burpsuite's and Nuclei, make finding these bugs effortless.
Nuclei is a free, open-source vulnerability scanner. Upon running it for the first time, the tool will download templates to run against numerous frameworks and sites. One of them, wordpress-detect.yaml which is under the technologies folder of nuclei-templates. Run this template on list of your target to detect WordPress sites, and figure out what could be vulnerable to the following exploits:
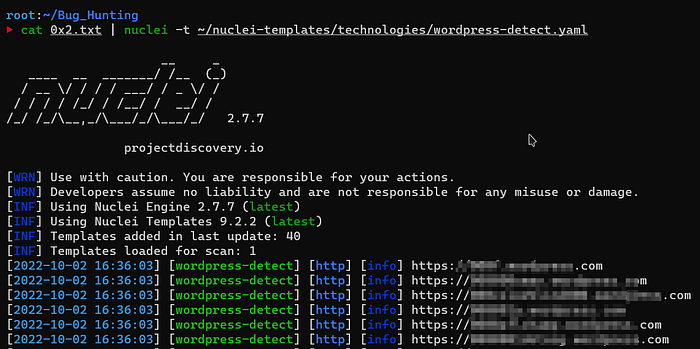
cat alive.txt | nuclei -t ~/nuclei-templates/technologies/wordpress-detect.yaml
The exploits →
After making sure that our site is using Wordpress, we'll want to approach this both through manual and automated attacks.
This section is going to go over the manual approach, through a couple of different exploit methods.
Username Enumeration via REST API
WordPress contains a REST API to list the information about the registered users on a WordPress installation. The API exposed user data for all users who had authored a post of a public post type. This can be consider as P4 as per Bugcrowd's VRT [Enumeration -> Usernames -> Non-Bruteforce] but we can increase this to P1, P2 by chaining other bugs.
We can enumerate the Usernames from the following endpoint
https://domain.tld/wp-json/wp/v2/users
If the wp-json/wp/v2/users is forbidden (403) then you should try the following bypasses:
/wp-json/wp/v2/users/n
/wp-json/?rest_route=/wp/v2/users/
/wp-json/?rest_route=/wp/v2/users/n
/?author=n'n' as in 1, 2, 3, 4, etc…

Neat!
Admin panel common password
Note: Make sure to check your target site's policies and scope, don't try this attack if brute forcing is out of scope.
In order to get access to the admin panel of WordPress site as admin, we'll need a username and password. To get those, we'll brute force the site using Burpsuite and Hydra.
Using Burpsuite for bruteforcing:
- Open the target WordPress site in your BurpSuite configured browser. If you don't have a configured browser, you can navigate to the intercept tab and click 'open browser'.
- append
/wp-login.phpto your target website's url - Enter some random credentials, such as
admin:password - Make sure to turn 'intercept' on in the "Intercept" tab.
- Enter your username from
wp-json/wp/v2/users - Clear all positions and modify the value of
pwd=§admin§ - Open the Payloads tab, and input your wordlist
- Start the attack!
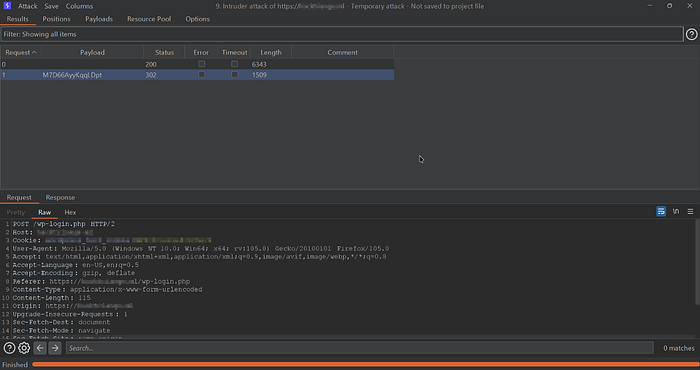
If you're successful and get into the site admin panel, you'll see a 302 status code!
Using Hydra for bruteforcing:
hydra domain.tld https-form-post "/wp-login.php:log=^USER^&pwd=^PASS^&wp-submit=Log In&testcookie=1:S=Location" -l bob -P /usr/share/wordlists/hack.txt -fThis command pretty much does the exact same thing that we did with Burpsuite, but you might need to know a bit more Linux and config details. Get started with Linux here, if you're unfamiliar-
Configuration File Leak
The wp-config.php file contains a ton of information required by WordPress in order to connect to crucial databases. It contains data such as the database name, host, username and even the plaintext password.
Occassionally, developers might forget to hide this sensitive file from the production server. Ergo, if you can access the wp-config.php file, it's an incredibly high severity bug.
The domain you're looking for-
https://domain.tld/wp-config.php
Most of the time it's going to give you a 403 or 404 (forbidden or insufficient permissions), but you can try the same file in different extensions.
/wp-config,txt
/wp-config.zip
/wp-config.md
/wp-config.php_orig
/wp-config.bak
Above is an example of wp-config.php.
Thanks for reading about how to find great Wordpress vulnerabilities! If you enjoyed this post, give it a few claps and check out The Gray Area or my website for more.
If you'd like to support my content, subscribe to a Medium membership using my referral link. It helps me create more content and posts just like this!
Thanks!


